Thesis
The last decade has seen a rapid acceleration of new workloads moving to the cloud. With the rising adoption of cloud computing, companies can build and scale their businesses faster than ever. However, the downside of the cloud’s widespread adoption is an increased attack surface due to the many types of workloads that run on the cloud compared to the on-prem era.
The major cloud providers, like AWS and Azure, provide security for the infrastructure layer (database, storage, compute, networking.) However, every customer that moves to the cloud needs to secure the operating system, applications, and workloads that run on their cloud of choice. This second layer above the cloud providers has created a large opportunity for cloud security companies to help customers secure their workloads.
This dynamic has driven the rapid demand for cloud security solutions. Spending on cloud infrastructure security was estimated to be around $188 billion in 2023. It’s also estimated that 99% of cloud security failures will be the customer’s fault through 2025. This creates an increasingly critical component for enterprises to ensure company security requirements are met and that data is kept safe. That’s where Lacework comes in.
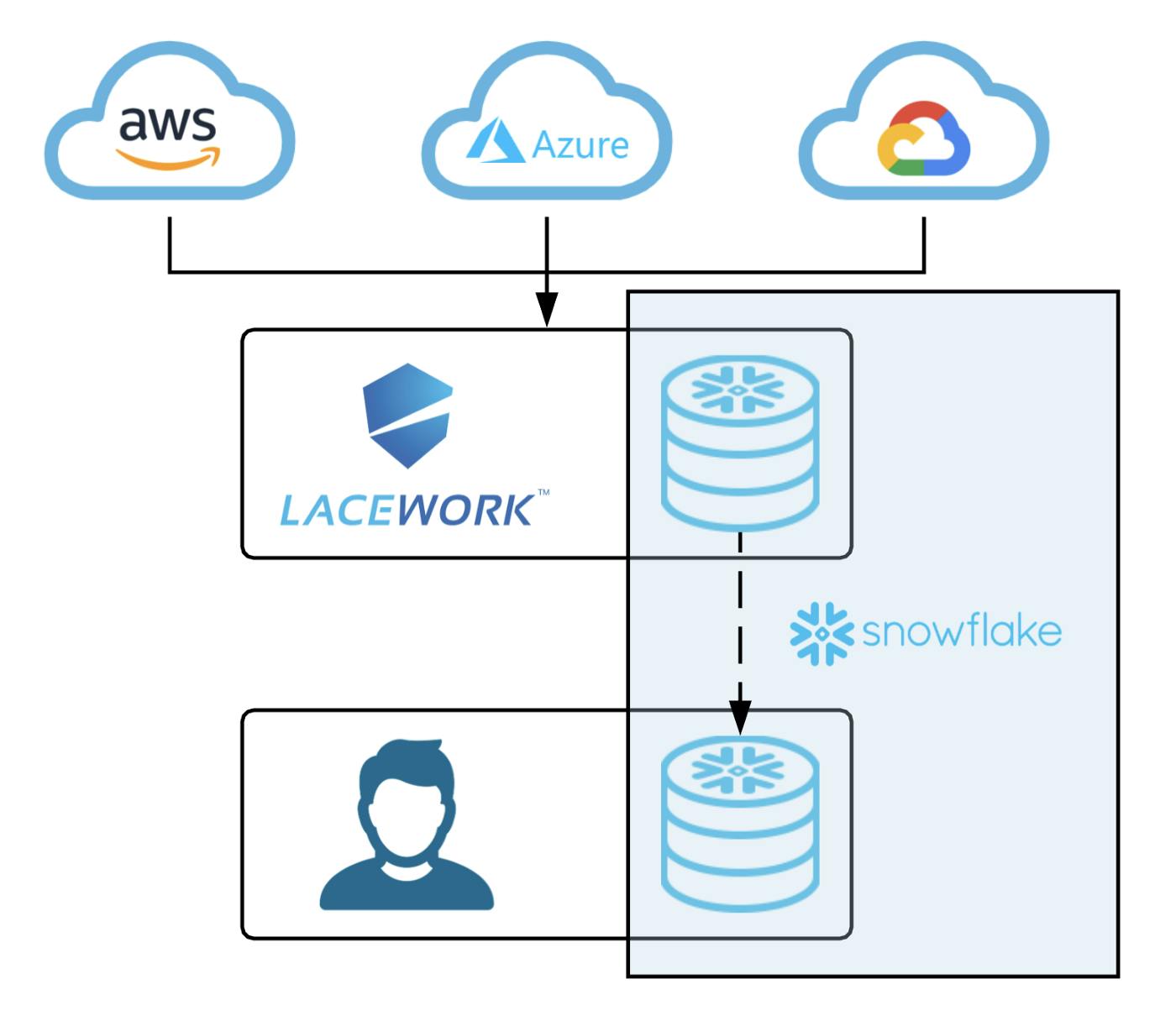
Lacework is a unified security solution that helps to secure businesses as they build on public clouds like Amazon Web Services, Microsoft Azure, and Google Cloud Platform or hybrid/private clouds. Lacework provides visibility into threats and vulnerabilities across an organization's cloud environment in a single platform. The size of the market opportunity has attracted investors and led to Lacework raising one of the largest funding rounds in the cybersecurity industry's history.
Founding Story
Sanjay Kalra (former CPO) and Vikram Kapoor (CTO) founded Lacework in 2015. The company was incubated by Sutter Hill Ventures.
Since the company’s founding, there have been a number of changes to leadership. In 2019, Kalra left his role at the company, and the company's board was joined by Mike Speiser, a Sutter Hill Ventures partner who was well-known for co-founding Snowflake in 2012, and John McMahon, who was also a board member at Snowflake.
The company has also had a number of changes at the executive level. Since 2017, Lacework has had at least five different CEOs including Jack Kudale in 2017, Stefan Dyckerhoff in 2018, and Dan Hubbard from 2019 to 2021. In February 2021, David Hatfield joined Hubbard as co-CEO for a month, before Hubbard stepped into the role of Chief Product Officer until his departure in November 2021. Hatfield continued as CEO until Jay Parikh joined him as co-CEO in July 2021. Hatfield and Parikh served as co-CEOs until Hatfield stepped down in October 2022, though he continued to serve as a member of Lacework’s board as of May 2024. Parikh became sole CEO in October 2022 and remained CEO as of May 2024.
In 2021, the team added Ulfar Erlingsson, who joined as Chief Architect for the company. Ulfar has over 30 patents and has authored dozens of publications on the impacts of data processing, operating systems, computer architecture, and more. He joined from Apple where he previously served as the Head of Machine Learning. Erlingsson left Lacework for Google in January 2024.
In May 2023, Lacework announced Lea Kissner would be joining as the company’s new Chief Information Security Officer, having previously held that role at Twitter. In October 2023, Lacework brought on Kevin Kiley as Chief Revenue Officer. Kiley had previously served as CRO of OneTrust. Prior to OneTrust, Kiley built VMWare’s cloud computing business.
Product
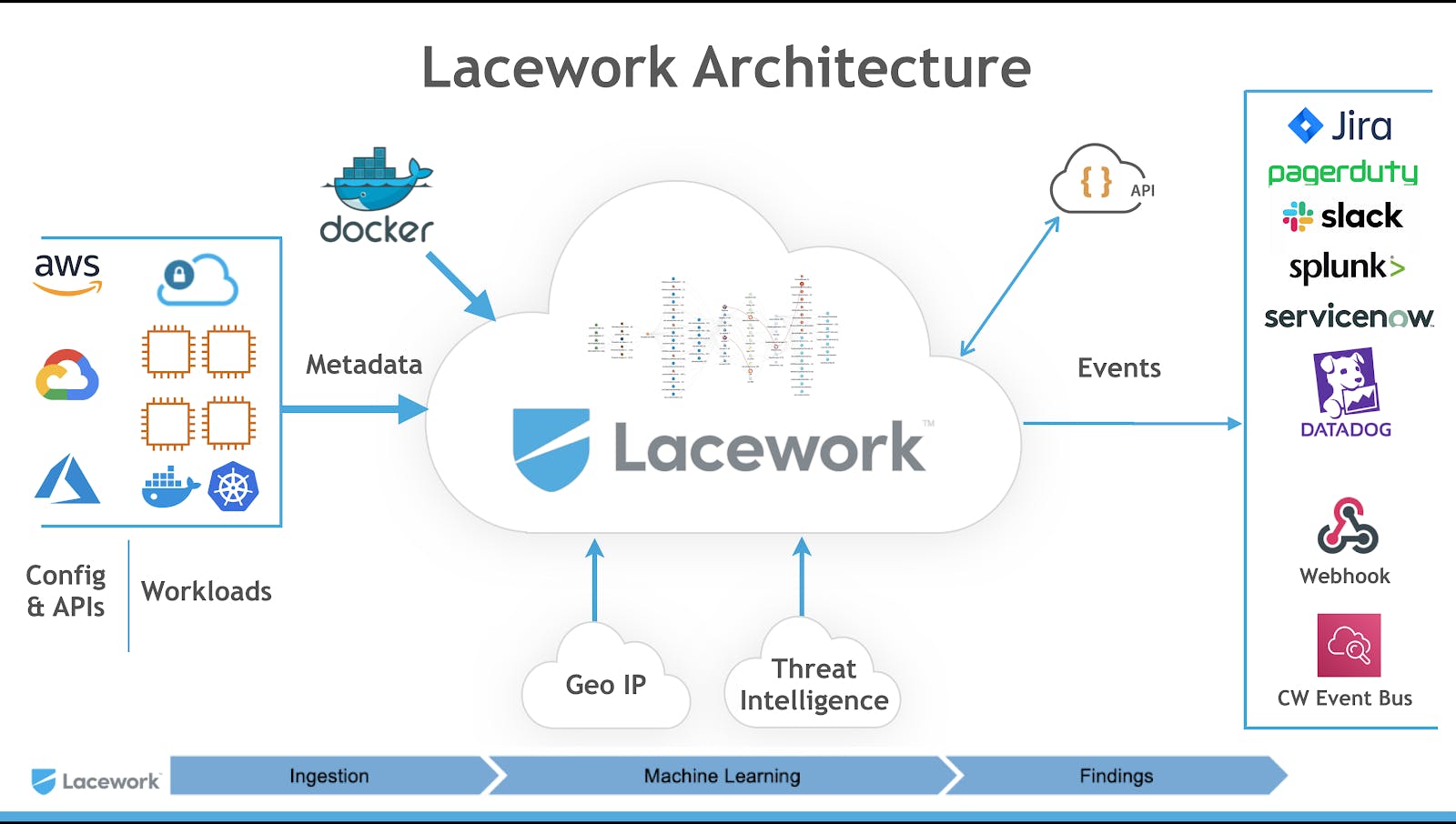
Source: Lacework
Lacework’s cloud-native platform offers automated anomaly detection that provides consistent visibility, context, and security across multi-cloud environments. It provides customers with the ability to detect attack activity stemming from known and unknown threats. The platform is able to prioritize risks before creating an alert for security teams. Unlike traditional security services, Lacework’s objective is to merge the way data and security intersect, by providing security through continuous monitoring and analysis of data across cloud environments. The product ingests volumes of data to analyze behavior, uses machine learning to detect abnormalities, and provides actionable insights for security teams without requiring a manual sifting through the data to identify vulnerabilities.
One of the biggest challenges facing SOC teams today is the extremely high number of alerts that security teams have to face on a daily basis. Lacework helps security teams overcome this security alert fatigue and frees time for them to focus on more advanced security problems. Laceworks’ architecture is able to ingest and integrate with a wide variety of data points from many enterprise solutions.
PolyGraph Behavioral Analytics Engine
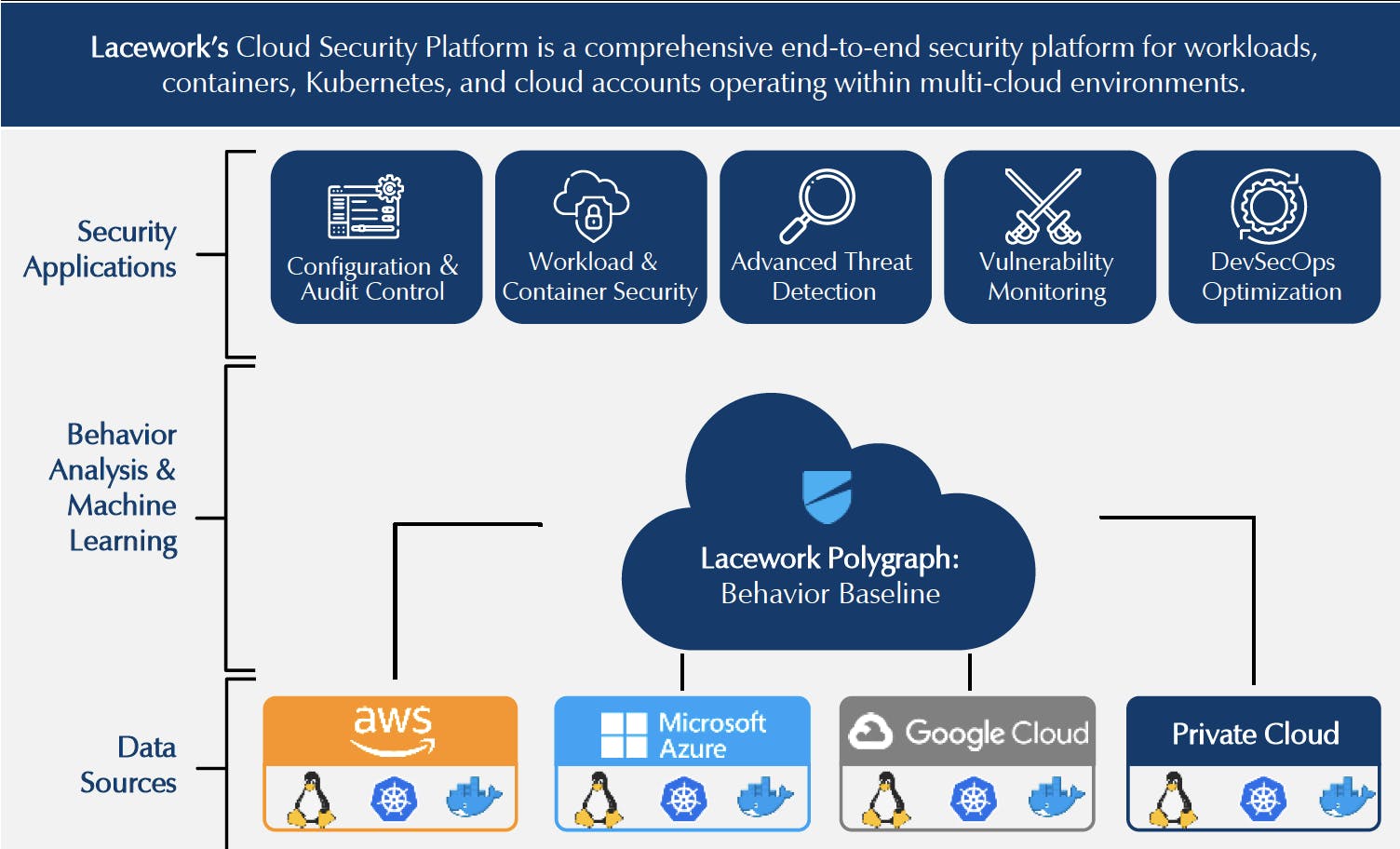
Source: Momentum Cybersecurity
Traditional security methods leverage pre-defined rules and protocols to create flags and deliver alerts. Security teams will manually write code to flag specific activities based on those pre-defined rules. But those rules are difficult to maintain in an ever-expanding attack surface where attackers are constantly changing their tactics. Instead, Lacework created their Polygraph Data Platform which uses data and machine learning to automatically identify risks, vulnerabilities, and abnormalities across the cloud environment, and then surface high-value alerts, prioritize risk, and speed up investigations.
Once the platform is installed, Lacework ingests massive amounts of data to learn about a customer's cloud environment. Lacework’s Polygraph establishes a baseline of what is normal in the users and applications engage with the customer’s cloud environment. The platform will then flag any anomalous activity. For example, if a machine sends data to an unknown IP, or if a user logs in from an IP that has not been seen before. In the below example of the Lacework platform the triage process is narrowing down 243 million incoming security data points, analyzing everything, and only sending 1 key alert to the SOC, representing a huge value add considering the average SOC can receive 11K alerts per day.
Source: Omer Singer
Integrations
Lacework enables security and DevOps teams to integrate their existing platforms in order to share data. For example, Lacework’s data platform can integrate with monitoring and log management tools like Splunk or New Relic, and incident response platforms like Atlassian, PagerDuty, or ServiceNow. In addition, Lacework’s data can be integrated with developer tools such as Puppet, Chef, and HashiCorp.
Cloud-Native Application Protection Platform (CNAPP)
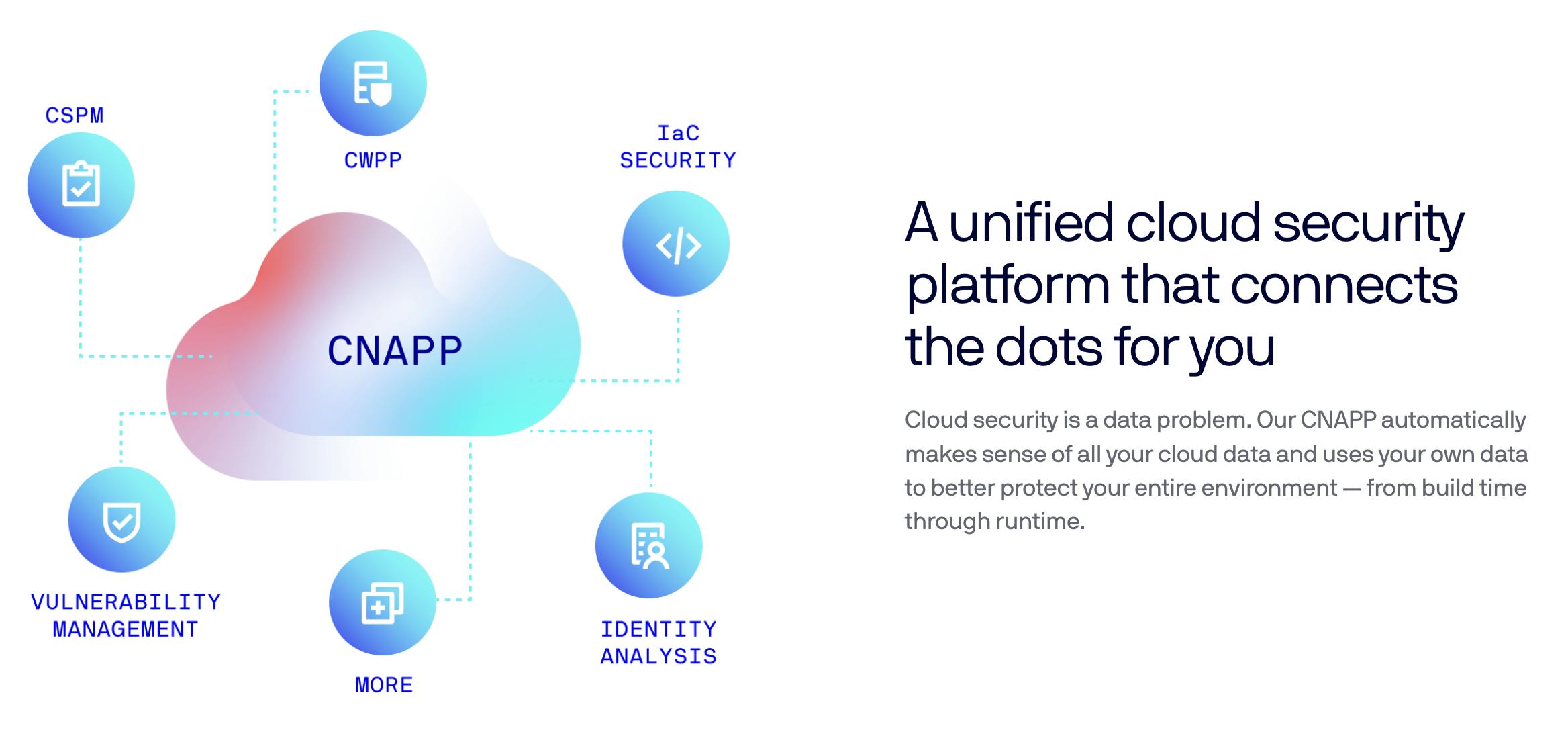
Source: Lacework
Cloud Native Application Protection Platform (CNAPP) is a cloud-native security model that encompasses Cloud Security Posture Management (CSPM), and Cloud Workload Protection Platform (CWPP) in a single holistic platform. CNAPPs emphasize the need for enterprises to focus on cloud-native security solutions that provide a complete lifecycle approach to application security as opposed to a patchwork of tools. For additional context on the category, see our deep dive on cloud security.
Lacework’s CNAPP platform is consolidating cloud data in order to continuously monitor user behavior and patterns in order to identify software vulnerabilities. These vulnerability assessments could include assessing workflows, enterprise management and third-party technology integrations, web application firewalls, missed patches, and different systems. It identifies potential vulnerabilities to proactively secure the cloud and address risks during the software development and release phases.
The process of reviewing cloud vulnerabilities in a security audit requires an audit log of specific reviews, which Lacework enables security to track in one place. For example, if an employee forgets to lock access to an AWS S3 bucket for several days the platform is able to detect this security risk and alert SOC teams. Lacework claims that the process of aggregating vulnerability data allows for 80% faster investigations and a significant reduction in the number of alerts.
Cloud Security Posture Management (CSPM)
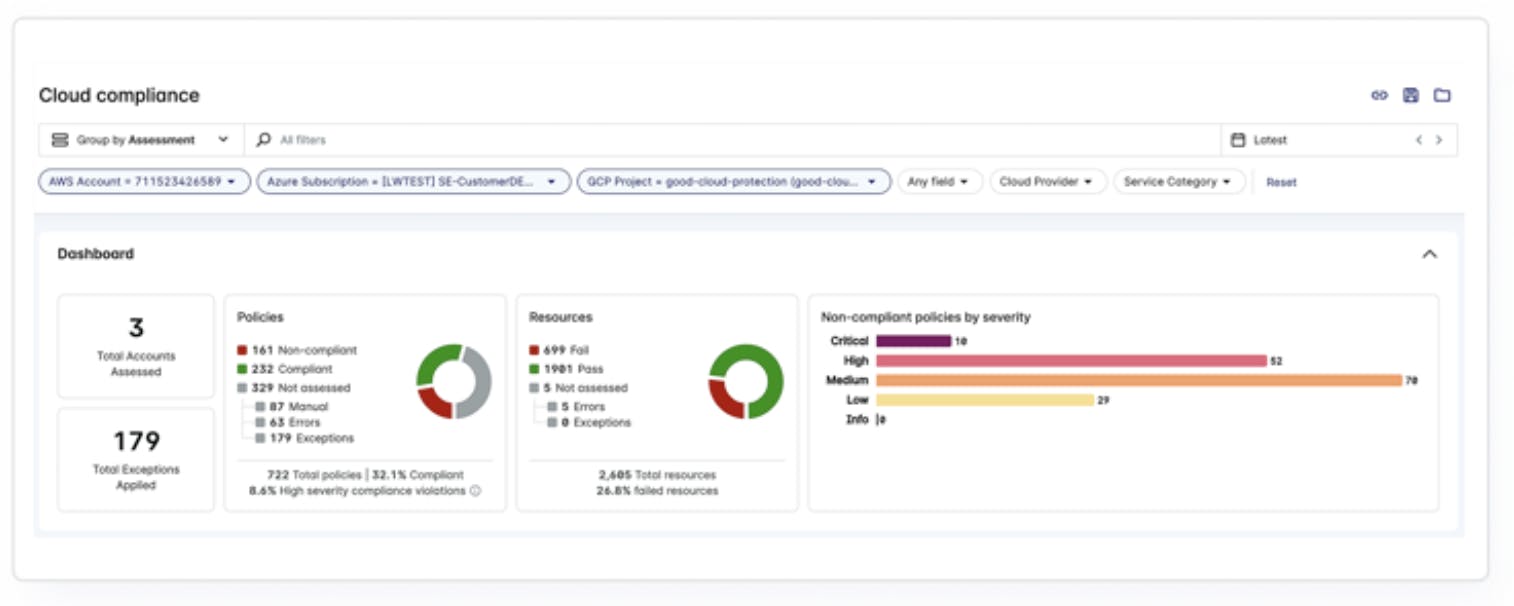
Source: Lacework
Cloud Security Posture Management (CSPM) is a process to identify and remediate risk by automating visibility, uninterrupted monitoring, threat detection, and remediation workflows to search for misconfigurations across diverse cloud environments and infrastructure, including Infrastructure-as-a-Service (IaaS). For additional context on the category, see our deep dive on cloud security.
According to Lacework, CSPM, when compared to CIEM, differs in regard to its focus. The company describes the difference this way:
“Although both CIEM and CSPM are crucial for cloud security, their focus areas differ. CIEM manages what actions users and services can take, while CSPM assesses the configuration of cloud services with frameworks and best practices. Both contribute to a comprehensive cloud security strategy.”
Each company establishes its own security policies for cloud infrastructure and then attempts to maintain compliance with those policies. One key problem is that not everyone spinning up cloud infrastructure is going to have security top-of-mind. Lacework’s platform provides hundreds of pre-built policies that companies can customize to meet their specific needs. Managing a company’s cloud security posture is the result of monitoring compliance with these specific policies.
Cloud Infrastructure Entitlement Management (CIEM)
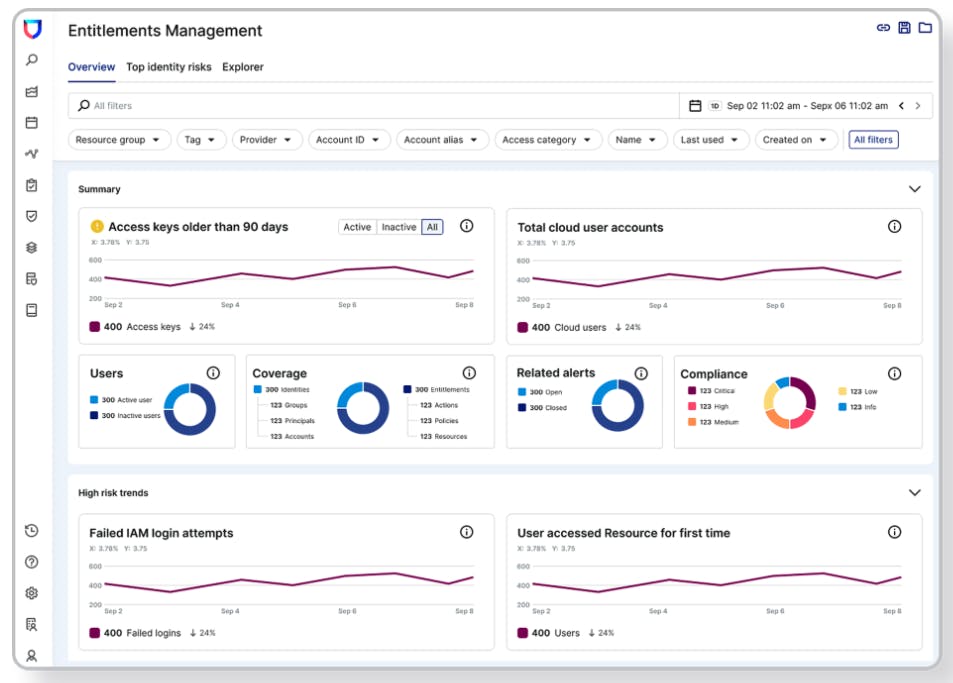
Source: Lacework
Cloud Infrastructure and Entitlement Management (CIEM) is the security process of managing access rights, permissions, or privileges for the identities of a single or multi-cloud environment. This process helps to identify and avoid risks resulting from privileges being higher or broader than they should be. For additional context on the category, see our deep dive on cloud security.
Lacework’s platform correlates user identity and resource permissions across a customer’s environment. By continuously monitoring user identities, the system can identify when a particular user is credentialed unnecessarily in a way that may lead to cloud vulnerabilities. Once these users have been identified Lacework can prioritize the potential risk of specific users.
One overview of Lacework’s launch of CIEM in June 2023 described the product this way:
“Lacework’s patented machine learning technology, Polygraph Data Platform, will power the new entitlement management offering. This capability, the company claims, will help dynamically discover and analyze cloud user, resource, group, and role identities, as well as their corresponding permissions. This is done by automatically comparing the permissions granted to the identities with the permissions actually utilized, allowing identification of identities that have been assigned excessive privileges.”
Cloud Workload Protection Platform (CWPP)
Cloud Workload Protection Platform (CWPP) encompasses platforms that provide security tailored to the needs of workloads deployed in public, private, or hybrid cloud environments. The objective of a CWPP is to keep the applications secure, by providing security for the application and all of the associated cloud capabilities. For additional context on the category, see our deep dive on cloud security.
Typical platforms will leverage rules-based engines to identify specific security requirements in a cloud environment. Lacework’s platform leverages signature-based and anomaly-based approaches in order to identify specific high-risk vulnerabilities in cloud workloads.
Infrastructure as Code Security (IaC)
Source: Lacework
In November 2021 Lacework acquired Soluble, which broadened its platform into Infrastructure as Code (IaC) and developer security. IaC enables developers to provision infrastructure within the DevOps environment. Lacework’s IaC product helps incorporate security into the build and application runtime. Developers are notified of any misconfigurations and provided with actionable instructions or can use automated fixes to address any problems. Lacework supports cloud security for Terraform, AWS CloudFormation, and Kubernetes.
Kubernetes Security (K8s)
Source: Lacework
Over 50% of Fortune 100 companies use Kubernetes (K8s) to increase the speed and efficiency of the development process. However, given the dynamic nature of K8s, its usage can create a number of potential vulnerabilities in the development process. Lacework’s platform can enable customers to ensure that misconfigured K8s resources aren’t deployed in the first place.
Attack Path Analysis (APA)
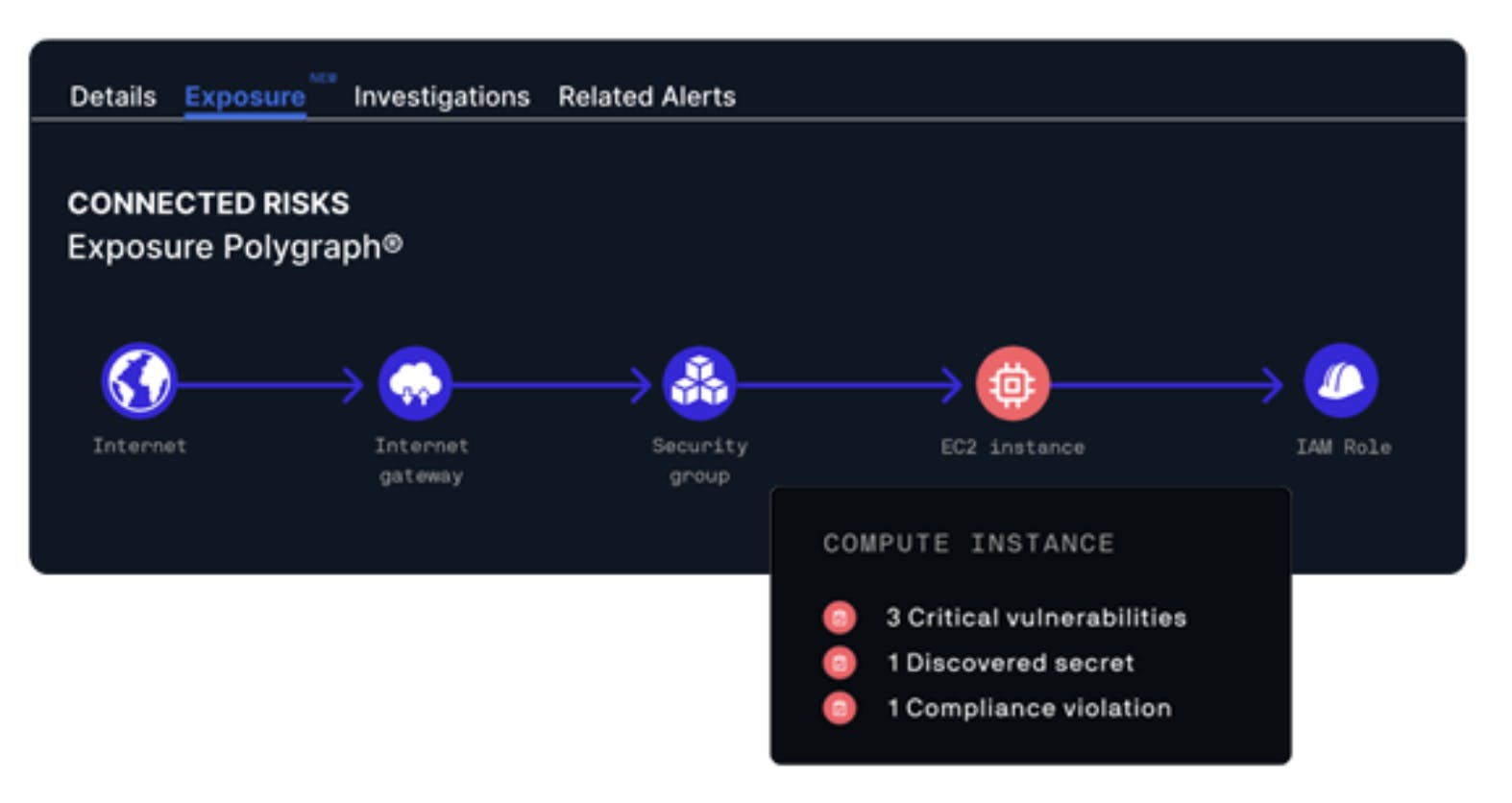
Source: Lacework
In ~31% of incidents, companies detect attempts to breach multiple vulnerabilities. These types of multi-faceted attacks are referred to as exploit chains. 56% of organizations lack the speed to address vulnerabilities, and leveraging multiple attack vectors can exacerbate the problem. Because Lacework aggregates a wide variety of cloud signals, the platform can also outline an attack path that not only maps together correlated vulnerabilities but can also prioritize specific threats. For example, identifying where an active intruder is targeting is more important than a previously leveraged vulnerability.
Market
Customer
Lacework’s ideal customer profile is a cloud-native organization that utilizes one or more of the public clouds. These organizations require a way to proactively secure cloud environments at scale, meet compliance demands, detect and remediate issues, manage vulnerabilities, and identify any threats through an easy-to-use UI. Laceworks customers include Snowflake, LendingTree, Clari, and Drift among others.
Market Size
Laceworks’ addressable market benefits from several industry tailwinds (cloud, security, and data). Enterprises are expected to spend $188 billion on public cloud infrastructure security in 2023. Some estimates indicate companies will have roughly 60% of their environment in the cloud by 2025. Cloud Security is expected to grow to $62.9 billion by 2028, up from $40.7 billion in 2023.
Lacework also plays an essential role in container security. Containers are a common option for deploying and managing software in the cloud. As containers become an increasingly common way for organizations to increase speed, the need to improve container security architecture and automation becomes critical. The container applications market was valued at $4.2 billion as of 2023. Containers provide several benefits to the cloud as they allow applications to run in isolated spaces to drive more efficiency. Their flexibility, however, also exposes the cloud to new threats. All of this opens up an opportunity for Lacework to resolve container-specific security challenges at every layer of a containerized stack.
Lacework also benefits from the shift to Infrastructure-as-Code (IaC) Security. Managing and provisioning infrastructure through code, rather than traditional manual processes, allows infrastructure provisioning to become more automated. Developers won’t need to manually provision and manage servers, operating systems, storage, and other infrastructure components each time they develop or deploy an application. This brings significant benefits to the modern enterprise; speed, efficiency, scalability, standardization, lower costs, and more.
As a result, the line between software developers and security teams is beginning to blur. Lacework provides IaC or shift-left security with their first-ever acquisition, Soluble, which has been built into the product to find and fix misconfigurations in IaC. Through static analysis of code, Soluble uncovers issues and enables remediation of IaC in the earliest stages. The addition of Soluble to the Lacework platform allows developers to reduce risk and build faster by providing automated security guidance, testing, and policy management to ensure everything is configured correctly.
Competition
Wiz Security
Wiz is an Israeli company founded in 2020 and has raised $900 million in funding from investors like Index Ventures, Lightspeed, and Greenoaks. In February 2023, Wiz raised a $300 million Series D at a $10 billion valuation. The company focuses on the infrastructure and cloud security space that provides multi-cloud capabilities. Wiz appears to be the most competitive solution to Lacework, however, a key differentiator is their approach to runtime security and agent-less scanning. Runtime and build security is the ability to protect your containers as they’re running on the cloud. Wiz scans for vulnerabilities and threats using an agent-less solution (no manual software installment) aiming to address attacks before it is too late. Lacework leverages machine learning through the Polygraph platform to deploy its agent and review both historical and active event data.
Orca Security
Orca is also another well-funded startup that provides multi-cloud capabilities and competes heavily with Lacework. Orca has a case study with the CISO at Lemonade, Jonathan Jaffe. He described the experience this way:
“At my last company, we used Lacework for over a year. In the last four months of my time there, we also ran Orca in a PoC, so it was easy to do the Orca comparison side-by-side. And, we evaluated Prisma Cloud, extensively. Unlike Orca, the others require agents. DevOps wasn’t excited about installing and maintaining agents. DevOps also feared the performance hit agents could have on our systems, especially production. And, based on my prior experiences with Laceworks, I knew I’d be fighting with missing visibility because of missing agents.”
Prisma Cloud
Prisma Cloud from Palo Alto Networks has consolidated a series of acquisitions (RedLock, Evident.io, Twistlock, and Puresec) to have a cloud-native security platform deployed in multi-cloud and hybrid-cloud environments. Two major differentiators are cost and complexity as Prisma has consolidated disparate solutions and leverages a complex rule-based approach.
Splunk
Lacework competes with Splunk on incident management and endpoint protection which are point solutions of Splunk’s overarching SIEM (security information and event management) platform. Splunk’s SIEM platform is fairly expensive and requires a specific skill base of security engineers to manage and operate.
Other competitors are entering the cloud security market from adjacent categories, like Crowdstrike and SentinelOne from endpoint security, as well as developer-focused tools like Snyk which recently launched Snyk Cloud.
Business Model
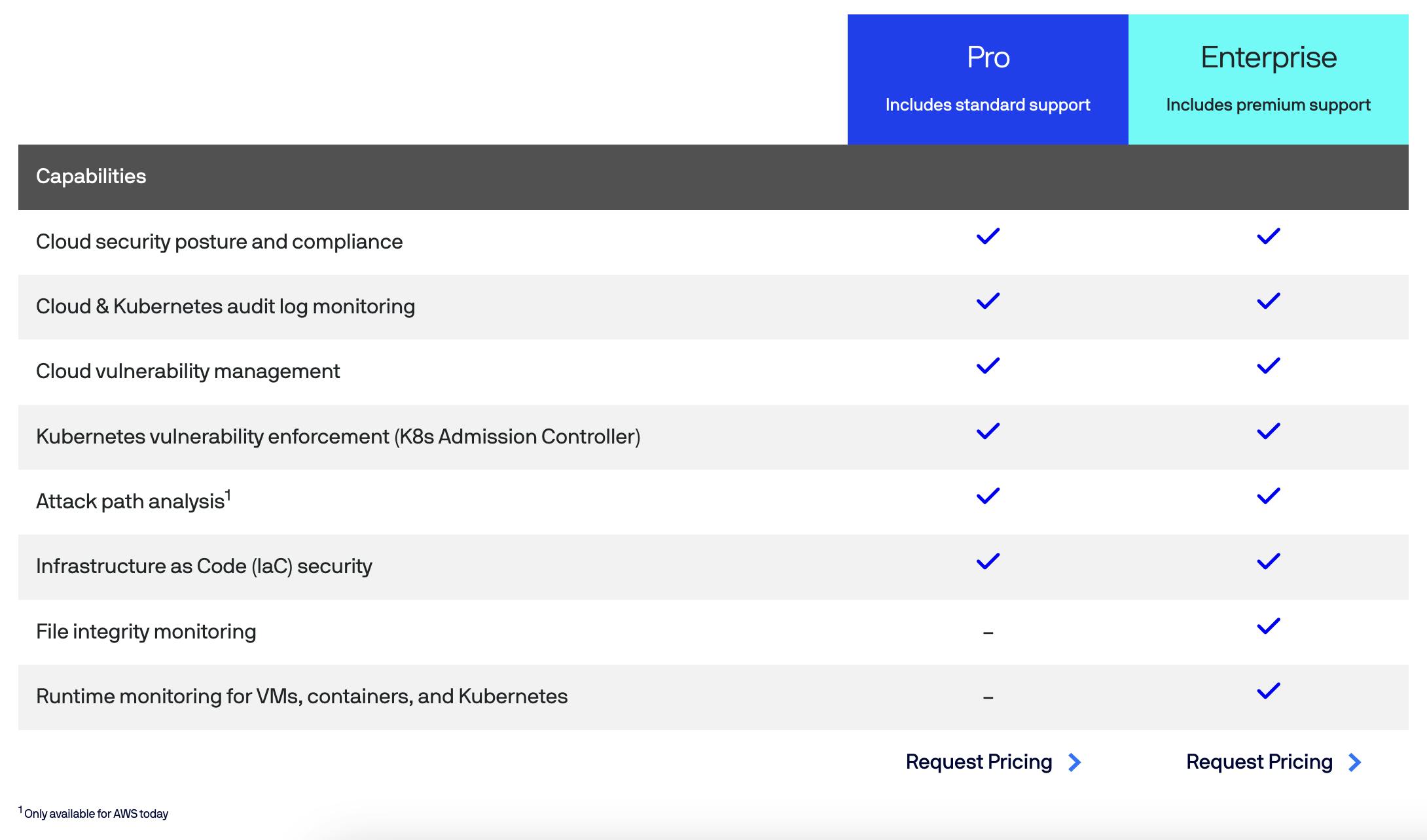
Source: Lacework
Lacework operates as a B2B Software-as-a-Service, with custom pricing plans tailored to the customer’s needs. Lacework’s model is built to take advantage of secular tailwinds as it is priced on the number of clusters and instances deployed. These are simply the work areas and workloads deployed by the customer. They also charge their customers based on the number of data points ingested and analyzed.
Traction
Lacework shared that they had experienced a 300% revenue growth year-over-year in 2021 to reach over $102 million in revenue. Lacework also experienced over 350% growth in new customer acquisition, adding customers like Sprinklr, LogicMonitor, and Hypergiant. Lacework’s ecosystem continues to expand to draw network effects from the likes of Snowflake, New Relic, AWS, GCP, Microsoft Azure, and growing channel partnerships.
Partners influence more than 60% of the company’s new business and are helping to scale the go-to-market at an ever-increasing pace. In May 2022, Lacework president, Andy Byron, shared that the company wanted to increase its focus on channel partnership, pushing for 100% of its business to come through channel sales and partnerships. For example, in June 2023 and September 2023 respectively, Lacework announced partnerships with AWS and Snowflake to improve the cloud security of each platform
One study concluded Lacework generated 342% ROI for one of their customers. The company evaluated is a high-growth mid-market organization with between $100 million - $1 billion in revenues, more than 2K B2B customers, tens of thousands of B2C customers, and over 1K employees. In addition to the 342% ROI, Forrester concluded that the customer received benefits of $2.3 million over three years versus costs of $522K, adding up to a net present value (NPV) of $1.8 million.
As of November 2023, Lacework was the #2 security product for Container Security, the #3 solution for Cloud Workload Protection, and a top Cloud Compliance solution.
In May 2022, Lacework announced it had laid off 20% of its workforce. The company said that the layoffs were the result of “a seismic shift [that] has occurred in both the public and private markets” at the time.
Valuation
Lacework raised a $1.3 billion Series D in November 2021 at an $8.3 billion valuation, the largest funding round for any cybersecurity company up to that time. At this valuation, its revenue multiple was approximately 81x at the end of 2021. However, given the market correction its unclear what Lacework’s current valuation would be. Private investors poured $7.8 billion into cybersecurity startups during Q4 2021 alone, compared to the $8.9 billion that was invested in the sector over the course of 2020. However, in Q1 2023, that funding amount had dropped significantly to $2.7 billion.
During the first half of 2023, publicly traded cybersecurity companies held up fairly well in comparison to other enterprise software categories. As of November 2023, the NASDAQ was up 26.8% YTD but companies with exposure to cloud security such as Palo Alto Networks, Crowdstrike, and Splunk have risen 74.1%, 82.9%, and 70.8% respectively.
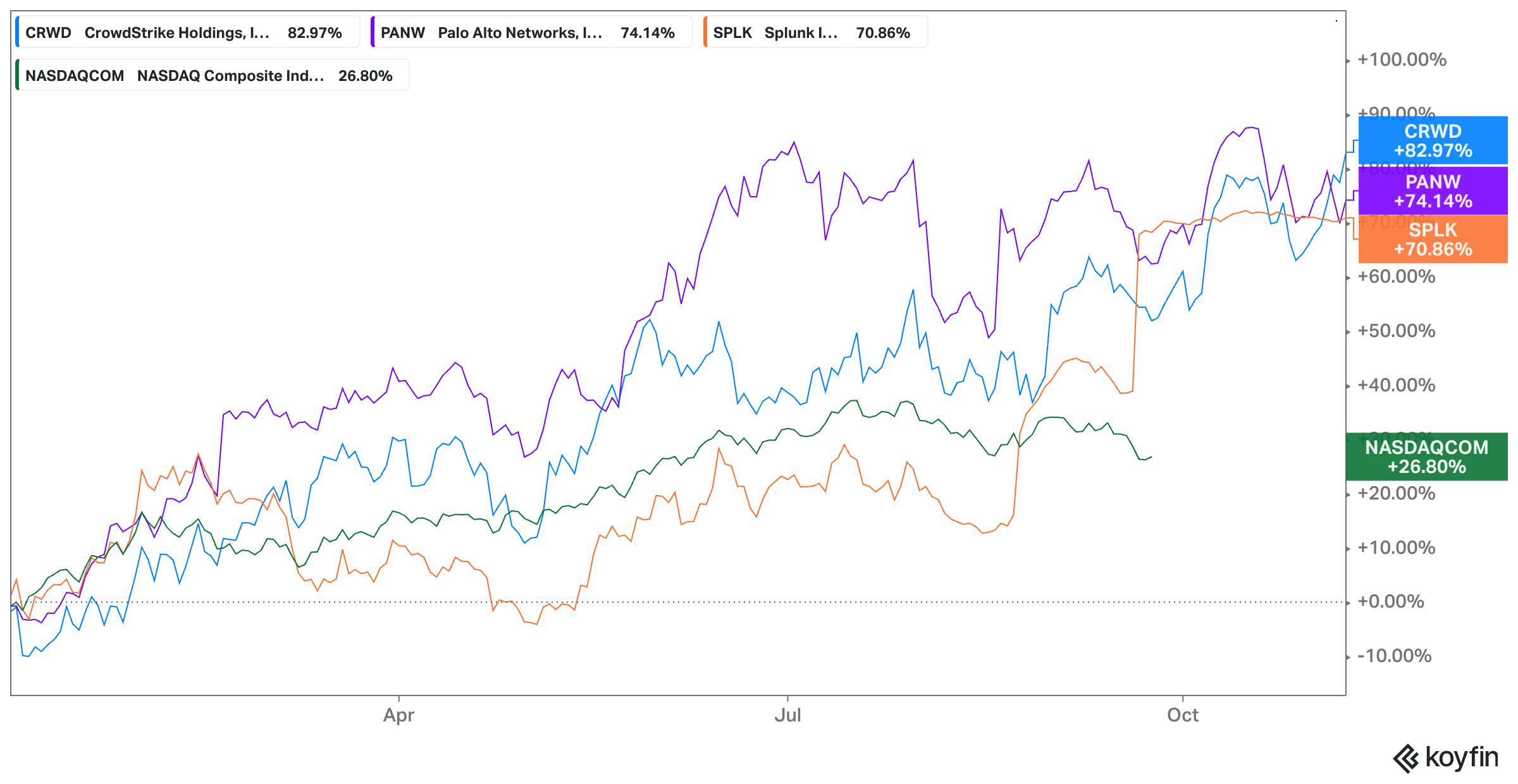
Source: Koyfin
Key Opportunities
Serverless Security
In the cloud computing paradigm, serverless refers to a distributed operational model in which applications rely on managed cloud services that abstract away the need to manage and patch servers, infrastructure, or virtual machines. Lacework already secures the build and runtime for code, however, it can serve a role in securing the serverless infrastructure on the likes of AWS or Azure. Lacework can ensure code integrity and tight permissions for serverless functions. For example, If an AWS Lambda function needs to access a MongoDB table, it can ensure that the right permissions are granted.
Key Risks
Competition
Lacework competes with organizations like Palo Alto Networks Prisma Cloud and Splunk that have deep pockets, and have more mature platforms. They also compete against cloud-native platforms like Wiz, and Orca Security. With a long list of competitors that have significant backing from the public and private markets, the competitive landscape is formidable. Most companies are expected to adjust their offerings to be multi-cloud friendly. Lacework will rely on its partner ecosystem and product innovation to remain competitive.
Summary
Lacework’s product will continue to evolve as it identifies additional use cases and as enterprises continue to adopt cloud infrastructure and containerization. Amazon’s CEO Andy Jassy was quoted in April 2021 claiming that under than 5% of IT spend pertains to cloud-related expenses. As organizations continue the inevitable migration to the cloud, Lacework supports the optionality of security for multi-cloud environments.
Lacework’s key value proposition is their ability to consolidate multiple cloud security use cases into a single platform leveraging data and analytics to automate these processes while also providing visibility into the event. They are taking advantage of multiple secular tailwinds, including the rise of more workloads moving to the cloud. Actively monitoring data in the cloud to identify security risks is a more efficient and scalable method to address security rather than the manual and siloed processes of rule-based reviews.