Thesis
Cyber threats on corporate networks are on the rise, with more than 262 million network exploitation attempts and over 11K network-related vulnerabilities reported in 2021 alone. This was catalyzed by the pandemic-induced remote work environments as the number of attacks tripled from pre-covid levels. Further, 20% of breaches are attributed to internal sabotage from network insiders.
Traditional perimeter-based network security models that were designed for on-premise applications and data centers are no longer effective in protecting distributed workforces, devices and cloud-hosted company assets. Additionally, these models had fundamental security flaws as they rendered implicit trust to internal users who could move laterally within the network and access unauthorized sensitive resources.
As a result, organizations are increasingly moving towards adopting zero trust security strategies which focus on securing enterprise assets at any location for any user or device, instead of the perimeter network. This framework assumes that attackers are already in the network and no connection, whether internal or external, can be implicitly trusted. Users are therefore given the minimum privilege necessary to perform their intended tasks and are continuously authenticated.
Netskope is a network security platform that offers secure remote access, cloud-hosted application protection, and secure internet access solutions based on zero trust principles. The company is riding industry-wide secular trends including remote and hybrid work environments, cloud adoption, and the convergence of networking and network security functions.
Founding Story
Netskope was founded in 2012 by Sanjay Beri (CEO), Krishna Narayanaswamy (CTO), Ravi Ithal, and Lebin Cheng. Beri had prior experience in startups having co-founded a data center encryption company, Ingrian Networks, in 1999 which was sold to Safenet in 2003. He also spent 8 years at Juniper Networks where he last held the position of VP & GM, and ran the company’s Access & Security product line.
While at Juniper Networks, Beri noticed that there was a shift in the cloud and was eager to build a cloud-based security product for protecting cloud workloads. As Beri told Forbes in 2021:
“[Users are] going to access the cloud on their own devices. It's an unstoppable force. Don't try to stop it mister security person, cause that's what they would do. No, the answer is to enable it. But to enable it, you need a new architecture for security. You need to think about how to build a security in the cloud that can protect your most valuable asset, your data.”
Early on in the ideation process, Beri sketched out the idea for this new security architecture at a meeting with the then-CEO of Symantec, Enrique Salem, and later he did the same thing in a meeting John Thompson, the former chairman of Microsoft. Both proved very receptive and became early investors.
Convinced that it was an opportunity worth pursuing, Beri quit his job at Juniper Networks and assembled a team of co-founders in 2012. They then built their first product, a tool for IT teams to monitor and manage the cloud applications used by their employees. The company came out of stealth in October 2013 with the announcement of $21 million Series A round from Social Capital and Lightspeed Venture Partners. Fast forward to November 2022, Netskope has over 2K employees across its global offices and more than five network security products.
Product
In the pre-cloud computing era, organization assets and IT resources were hosted in data centers and most corporate activities took place at company offices. Enterprises would traditionally put perimeters around their assets whereby any authorized user inside the network could access the resources while external intruders were kept away. This model, also known as castle-and-moat typically, involved implementing firewalls and intrusion detection systems at the network's entry point to prevent unauthorized access from the outside.
Enterprises also used virtual private networks (VPNs) to allow the few remote workers, or employees on the road, to securely connect to the network servers. The perimeter-based security model was working well to some extent but even then it had limitations. Once users were verified, they were given implicit trust and could move freely within the network. So if attackers stole credentials and breached the perimeter they could move laterally within the network to access sensitive resources. It also risked internal espionage from rogue or disgruntled employees.
The emergence of cloud computing technologies dismantled the castle-and-moat security architecture as more workloads and corporate sensitive data were migrated to the cloud. Organizations rapidly adopted SaaS applications and cloud infrastructure products that were hosted in locations outside of corporate network perimeters. Further, the rise of remote and hybrid work environments meant that company assets, users, and sensitive data were distributed far and wide. As a result, the zero trust security model was introduced.
Zero trust is based on the concept of “never trust, always verify”. It requires all users and devices to authenticate and authorize access to each resource on the network, regardless of whether they are inside or outside the network perimeter. it is also based on the principle of least privilege, which states that users and devices should only be granted the minimum level of access necessary to perform their intended tasks and blocking their ability to access the rest of the corporate network. Moreover, access is continually re-evaluated and changed as needed.
In the zero trust framework, VPNs are replaced by Zero Trust Network Access (ZTNA) which allows remote users to securely connect to authorized internal corporate applications only. Organizations also typically use other zero trust-based network security technologies such as Cloud Access Security Broker (CASB), which sits between users and cloud vendors to provide visibility into all cloud applications and enforce data security policies; Secure Web Gateway (SWG) which protects users against internet-based threats and blocks malicious sites; and Firewall as a Service (FWaaS) which is a cloud-hosted firewall that filters out malicious network traffic.
In the past, enterprises used to buy these security tools from multiple vendors which created tool sprawl and integration problems. To tackle this challenge, a new concept known as Security Service Edge (SSE) has emerged. SSE combines all four cloud-based network security capabilities (ZTNA, CASB, SWG, and FWaaS) into a single platform. Companies could purchase one product that provides secure access to private applications, usage of cloud-based applications and secure access to the internet from one vendor.
Networking and connectivity have also seen a significant transformation in the last few years thanks to the changing nature of the work environment. Historically, companies deployed branch router appliances that connected their branch offices to centralized data centers. However, they are phasing out these legacy devices and replacing them with Software-Defined Wide Area Network (SD-WAN) products that connect remote users and branches to cloud applications and other enterprise locations by routing traffic directly to the cloud instead of first backhauling it to the data centers.
Enterprise vendors are increasingly converging SD-WAN with network security functions into a single, cloud-delivered platform known as Secure Access Service Edge (SASE; pronounced “sassy”) with the promise to natively build security into networking rather than layering on top of it, as well as simplifying the IT infrastructure by unifying multiple point solutions into a single SASE platform.
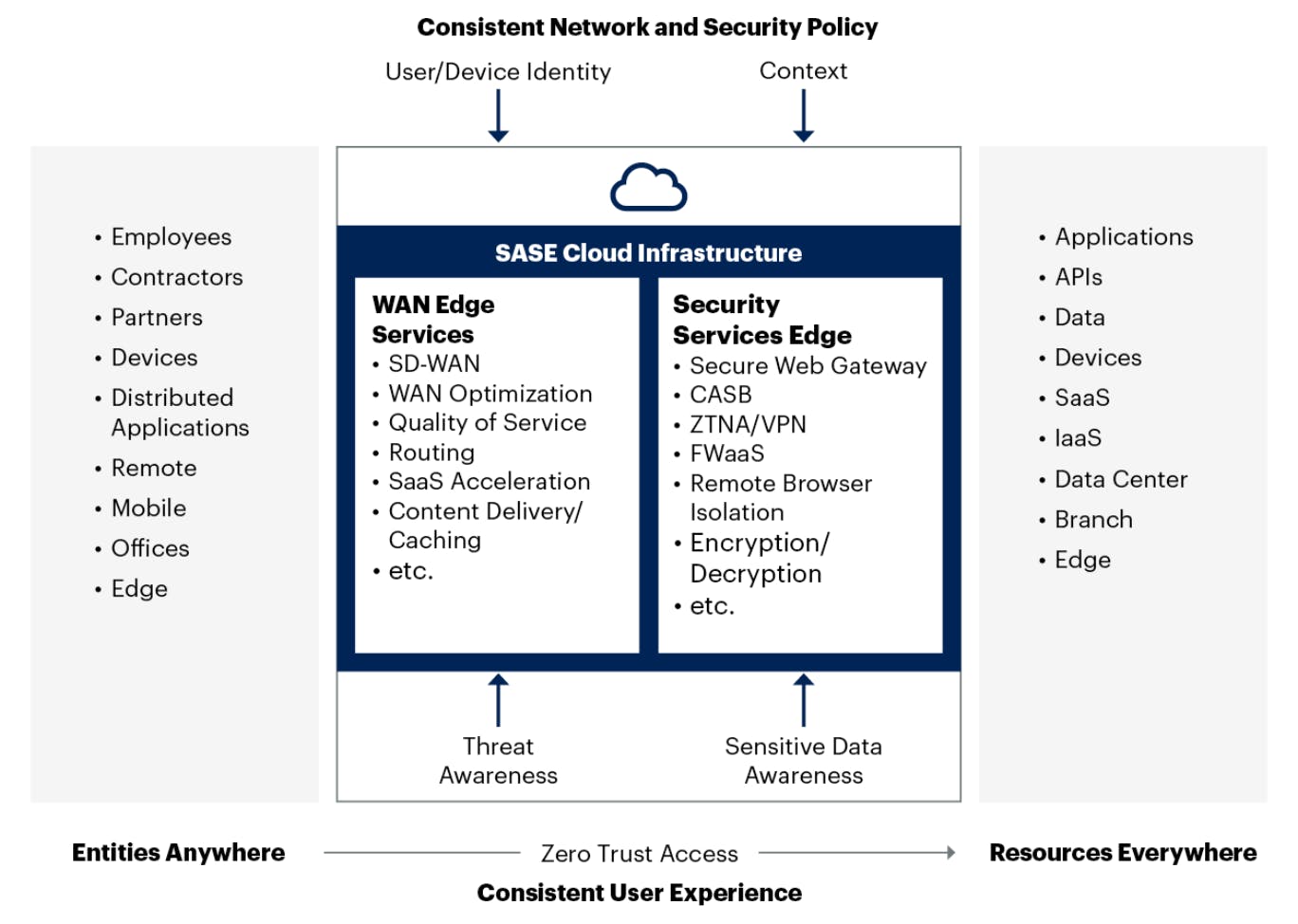
Source: Gartner
Netskope offers a number of products and solutions on its SSE platform including CASB, next-gen SWG, FWaaS, and ZTNA and is in the race to deliver an integrated SASE platform.
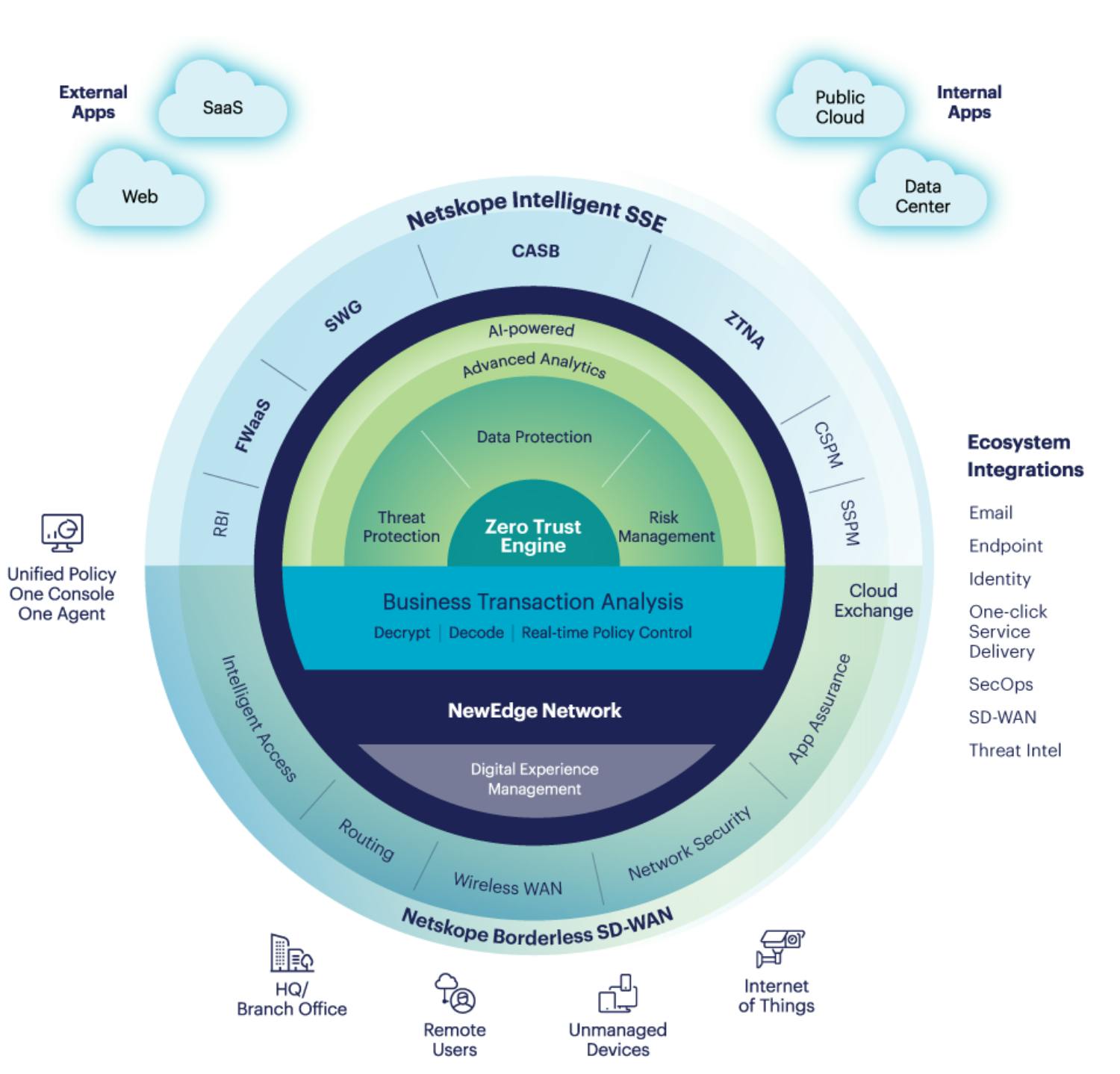
Source: Netskope
Cloud Access Security Broker (CASB)
Netskope’s CASB solution resides between users and cloud applications like Microsoft 365, G-Suite, and Salesforce as well as public cloud platforms such as AWS, Azure, and GCP. CASB functions as a gatekeeper that provides IT teams the visibility to all corporate-sanctioned SaaS and IaaS tools. It is also used to prevent shadow IT (i.e. employees using unapproved SaaS applications) by uncovering and blocking such tools.
Additionally, this solution offers data loss prevention capabilities that block unauthorized personnel from accessing sensitive assets and data. CASB allows companies to set and enforce policies against the transfer of unauthorized data and prevent internal data breaches. CASB is the earliest solution of the company and remains its flagship product.
Secure Web Gateway (SWG)
Netskope’s Web Gateway (SWG) solution protects a company’s internal network and users from internet-based threats and vulnerabilities by blocking access to malicious sites or inappropriate content. This is achieved through URL filtering, malware and intrusion detection, and content inspection. In addition to these capabilities, Netskope’s SWG offers threat and behavioral anomalies detection as well as granular policy control and enforcement features.
Zero Trust Network Access (ZTNA)
Netskope’s ZTNA solution provides remote users secure access to internal applications while restricting them to company-authorized tools only and limiting their movement to the rest of the network. This allows enterprises to grant employees, and third-party users like contractors and suppliers, application-level access while protecting more sensitive systems and data from untrusted personnel.
Firewall as a Service (FWaaS)
Netskope’s FWaaS product is offered as a cloud-native virtual barrier that protects an organization’s cloud platforms, applications and other assets by filtering out and blocking malicious traffic through the guidance of a set of internal policies. It also provides central access control with one policy engine for all remote users and devices as well as a firewall event logging feature that keeps track of all inbound traffic.
Borderless Software-Defined Wide Area Network (SD-WAN)
Netskope’s Borderless SD-WAN is a solution that provides remote employees and devices secure connectivity to cloud applications, branch offices, and other company locations such as factories and retail outlets. Netskope released this product in August 2022 after completing the acquisition of Infiot, an SD-WAN provider. This solution takes the company one step closer to achieving its vision to become a fully converged SASE platform vendor.
Market
Customer
From the outset, Netskope has targeted mid-market and enterprise companies and primarily focused on the financial, healthcare, and government sectors. The company has over 2K customers including 25% of Fortune 100 companies as of November 2022. Notable customers include Nvidia, Juniper Networks, Levi’s, the U.S. Department of Veteran Affairs, the Department of Health and Human Services, the Department of Treasury, Silicon Valley Bank, and the NHL.
Market Size
The overall SASE market was estimated at $4.9 billion in 2021 expected to grow at a CAGR of 32% to reach $15 billion in 2025. The SSE market, on the other hand, was estimated to have been between $2.4 and $2.6 billion in fiscal 2020 and is growing about 20% year-over-year.
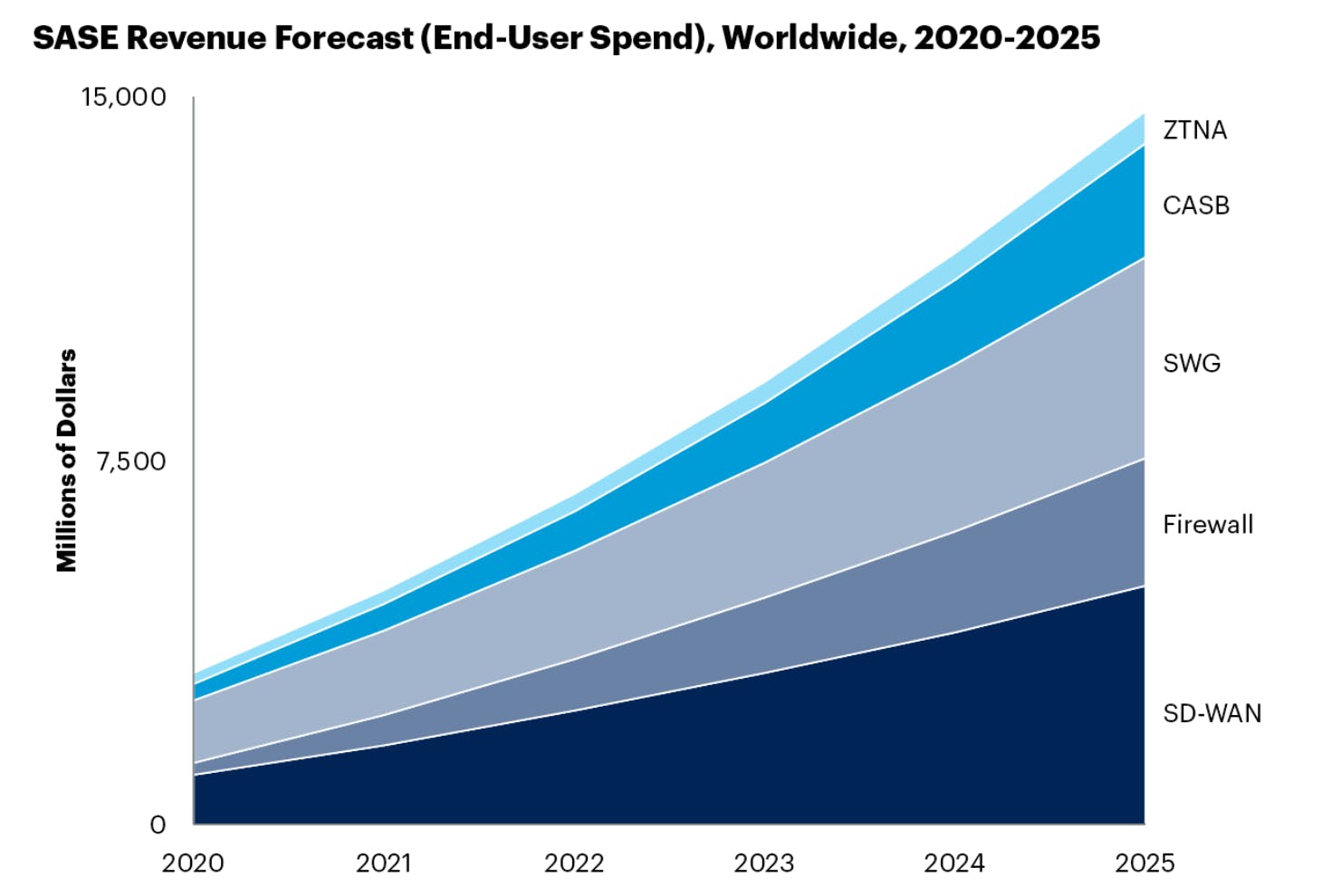
Source: Gartner
The SASE market growth is driven by a number of key factors including rapid cloud adoption, rise of remote and hybrid work environments, and tool sprawl.
Rapid Cloud Adoption: As organizations of all sizes increasingly shift workloads to the cloud and adopt cloud-first strategies for new systems, they also have to overhaul their security posture, ditch legacy network security tools that were designed to secure on-premise applications and replace them with cloud-based security solutions for protecting cloud workloads and critical corporate infrastructure.
Rise of Remote and Hybrid Work Environments: Due to pandemic-related office shutdowns in early 2020, enterprises were forced to conduct their business activities from home and remote locations, and run their corporate networks over the internet. As a result, interest and investment in SASE solutions has accelerated. Hybrid work models are expected to remain in place, which sustains the need for investment in SASE products to secure distributed workforce and networks.
Tool Sprawl: Large enterprises often adopt numerous networking and security products from several point solution providers. For instance, a typical fortune 500 company may buy an SWG solution from one vendor, CASB from a different vendor, and ZTNA from another vendor leading to increased cost but also causing delays to threat responses. To mitigate this, SASE adoption has been on the rise in recent years with 15% of enterprises consolidating their network security and networking products to a single or two vendors in 2021 and projected to reach 65% of enterprises by 2025.
Competition
The network security and SASE markets remain competitive with single-solution vendors increasingly offering multi-product, unified platforms in response to the industry-wide tool consolidation trends.
Netskope has its roots in CASB capabilities and has evolved over the years to become a leader in SSE by building additional solutions such as SWG, FWaaS, and ZTNA and acquiring an SD-WAN product in August 2022. Notable competitors include:
Zscaler, which is another leader in the space that started as a Secure Web Gateway (SWG) tool and currently offers a unified network security platform with all the network security functionalities, albeit at different maturity levels.
Skyhigh Security which spun off from McAfee Enterprise in March 2022 is another key competitor of Netskope and provides a similar SSE product suite.
FortiSASE by Fortinet, Prisma SASE by Palo Alto Networks, Cato SASE cloud by Cato Networks, VMware SASE, and Cloudflare One by Cloudflare are all also in the race with Netskope to deliver a single networking and network security platform for enterprises.
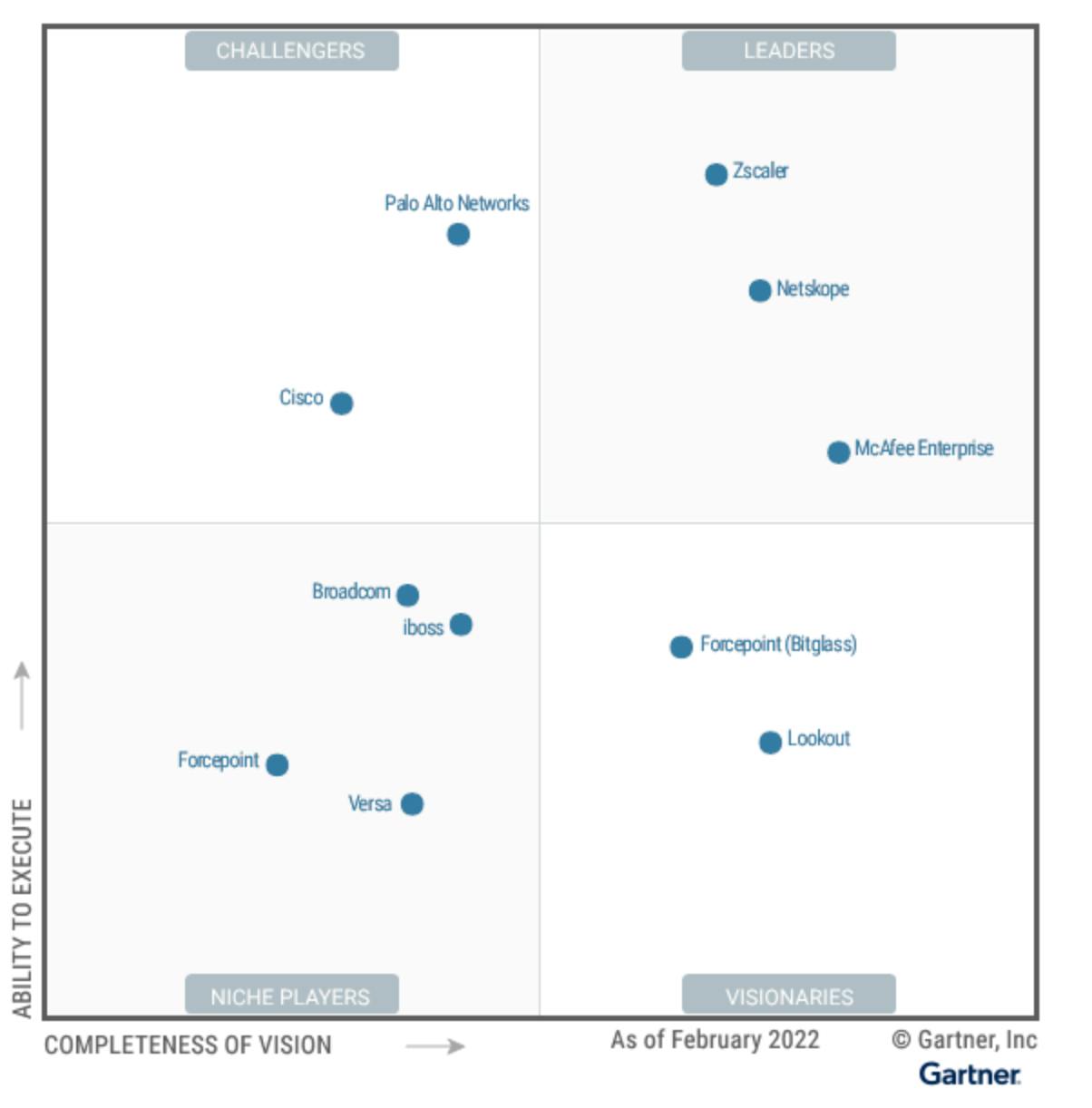
Source: Gartner
Netskope’s strength lies in the breadth of cloud applications that it can assess and audit. The company offers a database known as the Cloud Confidence Index (CCI), which consists of over 54K third-party cloud apps, their enterprise readiness levels, and risk scores. Organizations use the CCI score to determine the threat levels present in SaaS apps and set the appropriate policies to mitigate the threats.
Business Model
Netskope employs a subscription-based business model. While the company does not disclose its pricing plans on its website, its charges per seat and device for its products are listed on the AWS marketplace as follows:
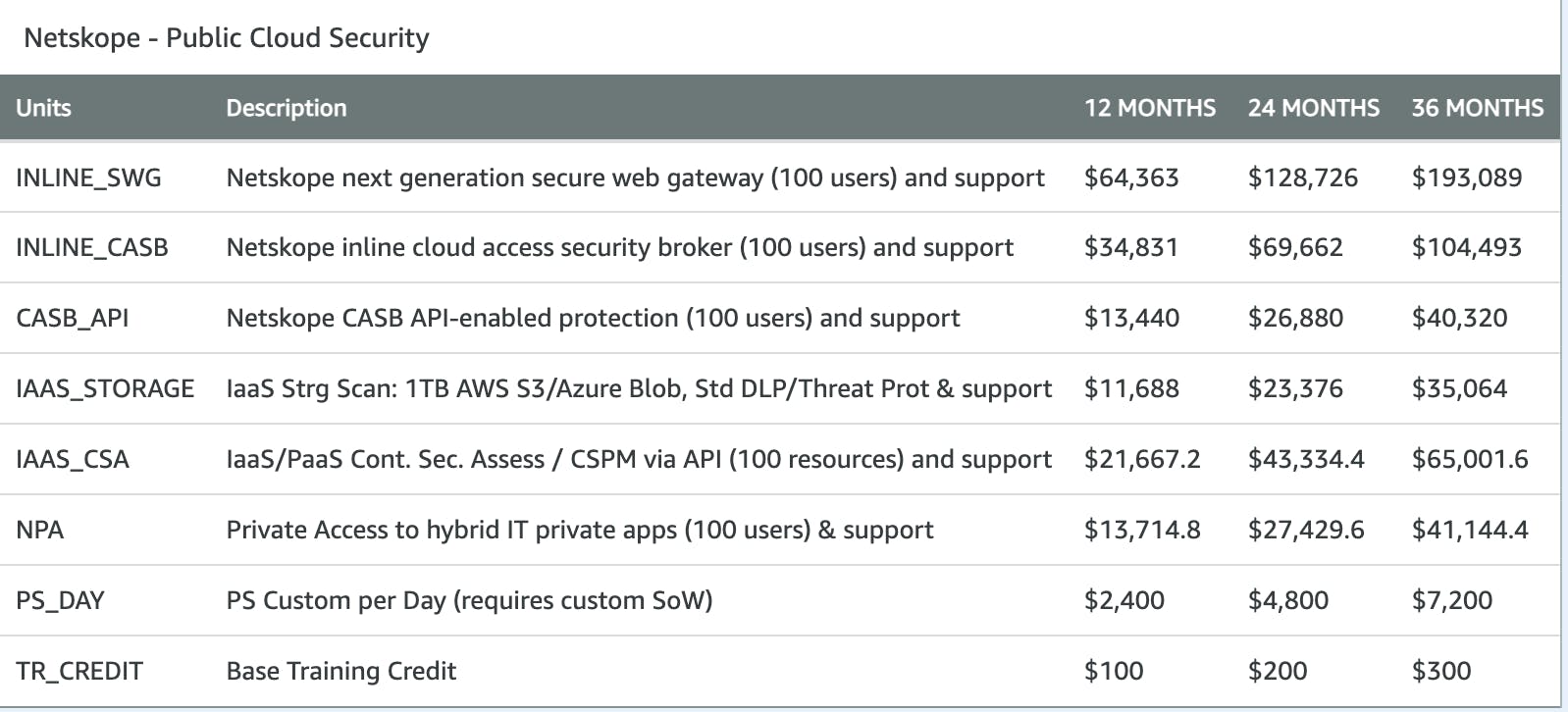
Source: AWS Marketplace
Traction
Netskope was reportedly growing its revenue by 80% year-over-year as of February 2020. Moreover, in an October 2022 interview CFO Drew Del Matto noted that it is generating more than $300 million in ARR with about 2K customers including 25% of the Fortune 500 and roughly 2,500 employees. Netskope has over 100 technology and channel partners including Crowdstrike, Okta, SentinelOne, Splunk, Sumo Logic, Microsoft, AWS, Google Cloud, Tanium, and VMware.
Zscaler which is Netskope’s closest competitor has a similar growth profile, reporting year-over-year revenue growth of 59% in the 12 months ending October 2022 but at a higher scale of $1.2 billion in revenue.
Valuation
Netskope raised a total of $1 billion in funding as of December 2022 from investors including Lightspeed Venture Partners, Accel, Sequoia, ICONIQ, and Sapphire Ventures. The company’s most recent round was a $300 million investment in July 2021 led by ICONIQ at a post-money valuation of $7.5 billion. Netskope CEO, Sanjay Beri, ruled out seeking future private investment following the July 2021 round and sees IPO as the company’s likely exit path, but did not discuss IPO timing.
Netskope’s $250 million ARR puts it at a multiple of ~25x ARR. This is premium to its public peers such as Zscaler, Fortinet, and Palo Alto Networks which have seen their valuation significantly compress since November 2021, and are trading at ~8-13x LTM revenue. Though Netskope’s comparable public companies are faring better than the broader software market that trades at a median of 5.1x LTM revenue as of December 9th, 2022.
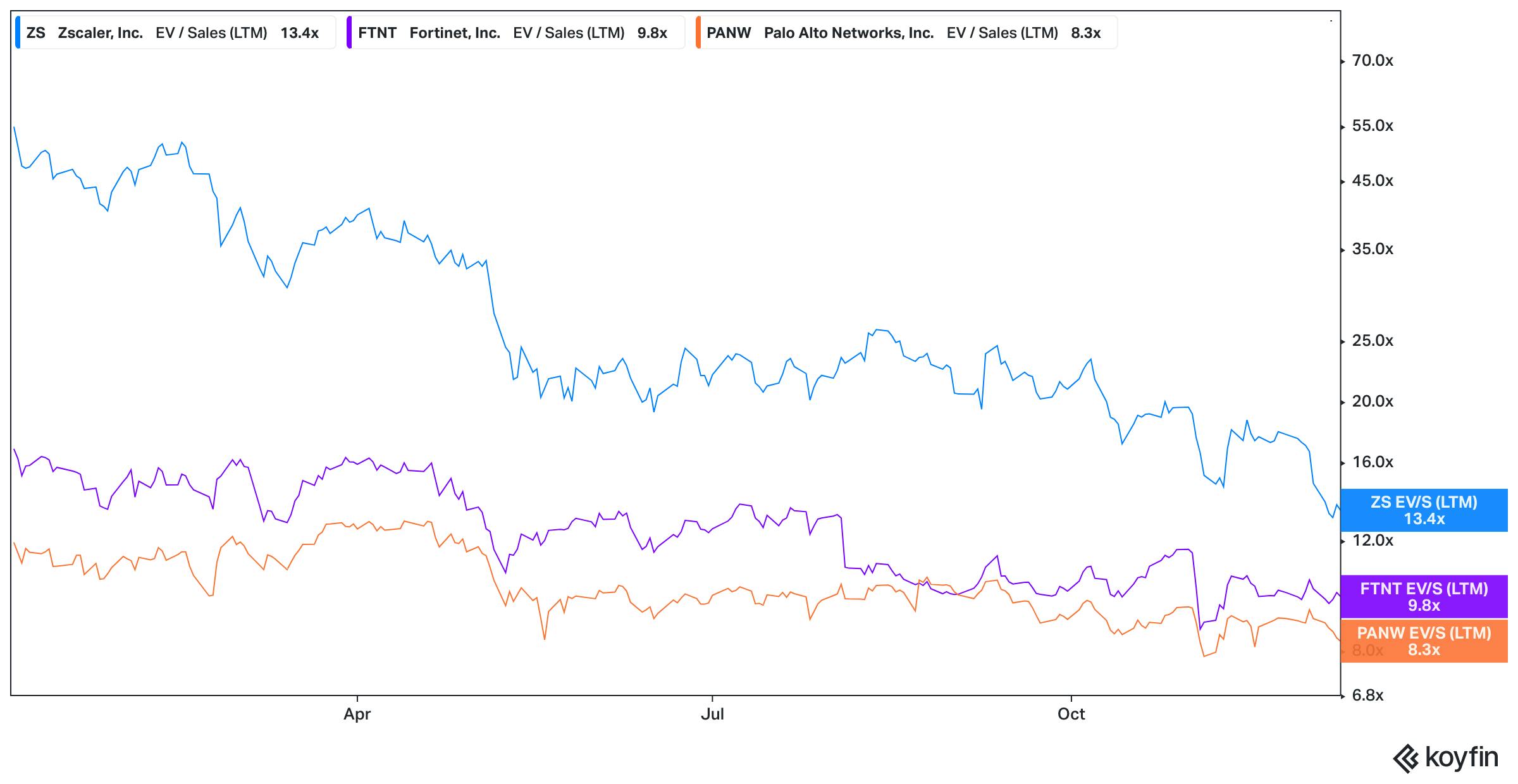
Source: Koyfin
Key opportunities
Government Expansion
In May 2021, the Biden administration issued an executive order on improving cybersecurity and mandated federal agencies to adopt and implement zero trust architecture by September 2024. Netskope has already received FedRamp authorization — the U.S. federal government’s rigorous cloud computing products assessment program — which allows the company to sell to federal agencies. Netskope counts 5 agencies as clients as of December 2022 including the Department of Health and Human Services and has the opportunity to invest more resources in the public sector vertical, ramp up its go-to-market strategy and expand to all government levels (i.e. federal, state, municipal) as they aim to overhaul and modernize their security infrastructure.
Key Risks
Organizational Silos Between Networking and Security teams
For many large enterprises, the network security and networking departments are managed separately with each procuring its own tech stacks. This has resulted in organizational silos, and could hinder the convergence of networking and security into a single platform. On a company level, Netskope could struggle to get buy-in from both teams as it builds and markets single-vendor SASE solutions and could experience longer sales cycles for its platform which could subsequently impact its growth.
Competition
The SSE and broader SASE markets are already crowded with established vendors such as Zscaler and Skyhigh Security, as well as emerging players like Cato Networks. Moreover, larger enterprises like Palo Alto Networks are increasingly bundling their endpoint security solutions with cloud and network security products and cross-selling to customers who are aiming to consolidate their security product suite for cost-saving purposes. For instance, Palo Alto Networks could cross-sell its endpoint security platform, Cortex XDR, with its SASE solution, PRISMA SASE, making it difficult for Netskope to compete for large enterprise deals against such Juggernauts.
Summary
Netskope continues to grow at a respectable pace and has evolved from a single solution to an integrated multi-product network security platform through a mix of internal product innovation and M&A activities. The company is also enjoying several industry trends in burgeoning network security and SASE markets. However, Netskope faces intense competition from well-resourced, established vendors and could struggle to gain a dominant foothold in the SASE space as tool consolidation trends intensify in the medium to long term.