Thesis
For a SaaS product to be considered enterprise-ready, it needs to meet three essential needs of larger customers: first, proper authentication; second, user authorization; and third, security and compliance.
User authentication entails identifying verified users who are trying to gain access to a system. Most commonly, this entails asking a user for a username or email along with a password. Password hacking has become increasingly prevalent, with over 24 billion passwords exposed in 2022 and a 65% increase in compromised passwords from 2020 to 2022. In January 2024 alone, that number was surpassed with a single breach spanning over 26 billion records. Of confirmed breaches, 80% are due to stolen, weak, or reused passwords.
As such, increased layers of security such as single sign-on (SSO), multi-factor authentication (MFA), and social sign-on (or OAuth) have become more prevalent, with the MFA market projected to have a compound annual growth rate of 18% from 2023 to 2028. Beyond its importance for security, user authentication is a key step in user sign-up and onboarding. A streamlined user onboarding experience can increase conversion and bolster retention.
User authorization, on the other hand, is the process of granting specific permissions to a user to access specific functionality or data in a system and is commonly a requirement by large enterprise-level customers. As such, concepts such as single sign-on (SSO) and role-based access control (RBAC) have become more prevalent, with the RBAC market projected to grow from $8.7 billion in 2022 to $15.5 billion in 2027.
The final component often required for software to be considered enterprise-ready involves security and compliance. Federal Trade Commission data show that consumers lost $12.5 billion to fraud in 2024, representing a 25% increase over the prior year. The global fraud and prevention market was valued at $58 billion in 2024 and is projected to grow to $246 billion by 2023. Common fraud and risk prevention methods include bot detection, device fingerprinting, and anomaly detection.
Stytch is building a developer platform that allows companies to become “enterprise-ready, agent-ready, and threat resistant” by providing frictionless authentication and authorization paired with fraud and risk prevention. The company’s APIs and SDKs aim to streamline user onboarding and provide low-friction authentication options such as email magic links, single sign-on (SSO), OAuth, and more. As an authentication provider, it provides enterprise authentication and user authentication services, positioning itself as an Auth0 alternative. In addition, offerings such as its device fingerprinting and active risk assessment bot screen users for fraud and abuse.
Founding Story
Stytch was founded in 2020 by Reed McGinley-Stempel (CEO) and Julianna Lamb (CTO). McGinley-Stempel and Lamb met at payments infrastructure provider Plaid while developing bank account authentication, where the duo quickly recognized that building authentication workflows remained cumbersome for developers.
Prior to Plaid, McGinley-Stempel spent over a year at Bain & Co. as a consultant. Realizing that there was a disconnect between his work spinning decks and feeding analysis back to the C-suite, he moved out to the Bay Area after a Plaid recruiter reached out to him regarding a growth role at the startup. For the first half of his stint at Plaid, McGinley-Stempel worked on the go-to-market team before moving to the product side, where he was responsible for deploying features relating to adaptive authentication.
Before Lamb joined Plaid, she spent a year as a full-stack web engineer at Strava, an exercise tracking application. McGinley-Stempel met Lamb on Plaid’s adaptive authentication team, who was working as a software engineer responsible for building client solutions via the Plaid API. At Plaid, the pair realized that users often struggled to recall their username-password combinations, leading to friction within the authentication process, and by extension, Plaid’s ability to integrate consumer-facing applications with user bank accounts.
As they grappled with potential tradeoffs between security and user conversion within the bank authentication experience, they realized that incumbent solutions were often inflexible, forcing companies to build out authentication features in-house. Although Lamb later left Plaid for Very Good Security, the two continued to meet regularly, exchanging frustrations around the lack of a flexible, accessible authentication solution geared towards developers. In June 2020, McGinley-Stempel and Lamb founded Stytch.
Product
Stytch allows its customers to offer secure user authentication, which is intended to drive higher conversion rates at onboarding and during the login process. Stytch’s developer-first approach has enabled the company’s passwordless solution to drive traction among engineers tasked with figuring out how to integrate login functionality into their applications.
Stytch aims to build solutions to reimagine user infrastructure via either out-of-the-box or customizable authentication solutions. The platform supports B2C and B2B companies’ core authentication needs when building sign-up and login flows.
The authentication solutions it offers are designed to be modular and flexible, ranging from one-time passcodes to magic links and biometrics. It has also built a full suite of authentication/authorization products to obviate the need to develop identity or access management systems in-house. Stytch’s SDKs provide the flexibility to use pre-built UI components, enabling developers to customize the user authentication experience.
B2B SaaS Authentication
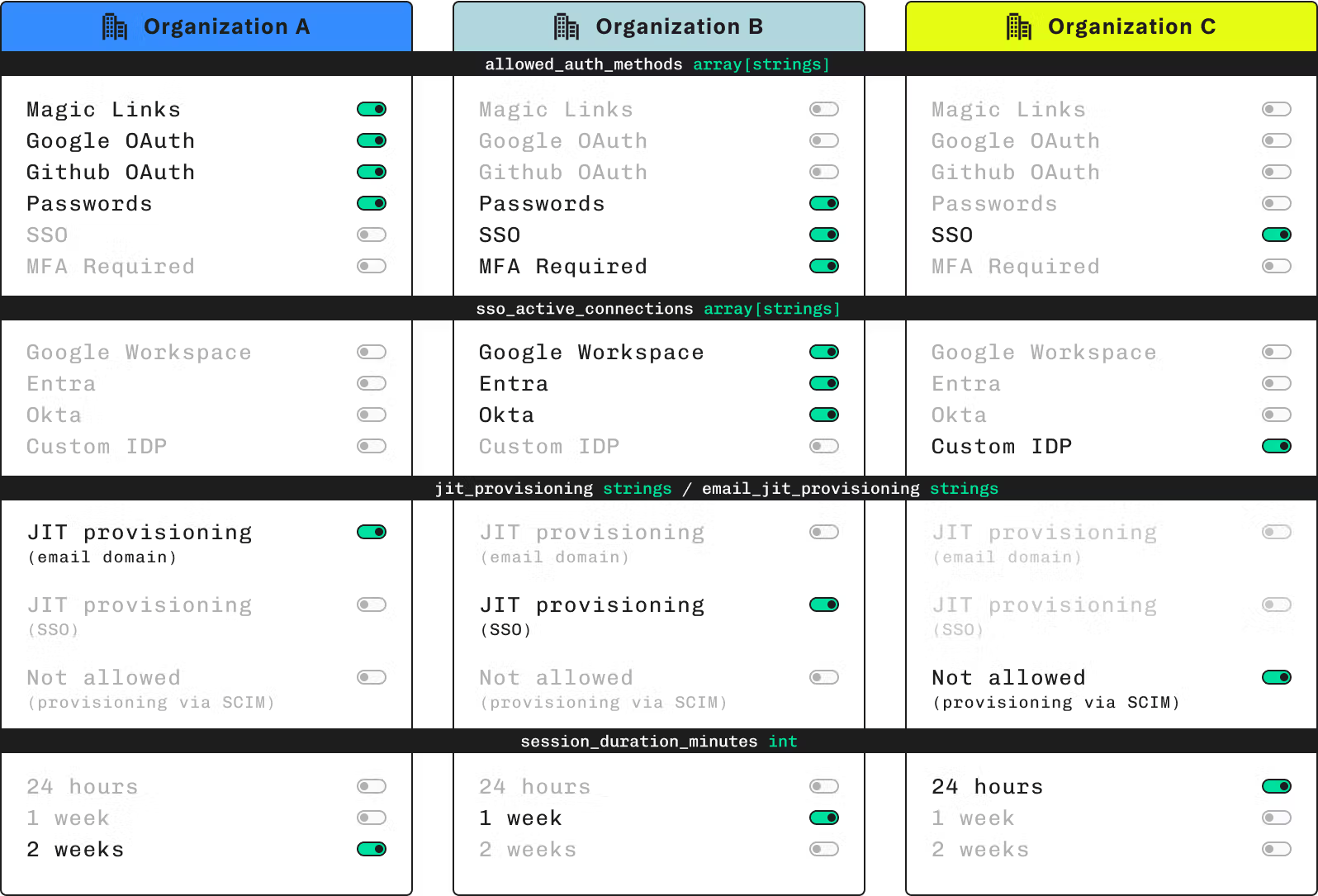
Source: Stytch
Organization Authentication Settings
Stytch’s organization authentication settings solution allows organizations to manage multi-tenant requirements related to memberships, self-serve or enterprise onboarding, and organization-wide settings.
Organizations, which refers to groups of end users (e.g., businesses and their constituent employees), are designated as top-level tenants in Stytch’s B2B offering and have configurable settings for access control along with regulation of authentication and member provisioning. Organization controls encompass specification of approved authentication methods, restrictions around email domains members can sign up with, disabling or enabling invites to join the organization, management of SSO connections, and storing of application or business-specific attributes.
Members, or end users who belong to the organization, can be identified via email address. Stytch supports the following mechanisms for creating members: invites (Magic Link-powered email invitation), just-in-time (JIT) provisioning (organizations can specify trusted sources like identity providers or verified email domains), and manual provisioning (direct API calls).
Single Sign On
Single Sign On (SSO) allows users to access multiple applications based on authenticated identity on another application (i.e., users can sign into a different application that will then vouch for the user’s identity when they attempt to log in to another application). SSO involves both the service provider (SP), the application the user is trying to access, and the identity provider (IdP), or the application responsible for authenticating the user. If the user opts for SSO, the service provider redirects the user’s browser to the IdP, where they’re prompted to enter their credentials to the IdP (unless already authenticated), and the IdP may then redirect the user’s browser back to the service provider.
On the developer end, SSO helps prevent security vulnerabilities by storing fewer user identities or passwords that could become avenues for credential stuffing. Stytch is compatible with major identity providers (e.g., Okta, Azure, Google Ping, Auth0, Cloudflare) and supports both Security Markup Language (SAML) and OpenID Connect (OIDC).
Connected Apps
In February 2025, Stytch introduced its Connected Apps feature, which enables integration between multiple applications by allowing users to authenticate across different apps using a single identity. Through Stytch’s frontend SDK component, users can configure any app as a fully compliant OAuth 2.0/OIDC identity provider. Stytch’s Connected Apps supports end-to-end OAuth 2.0/OIDC flows, managing token issuance, validation, and revocation while adhering to RFC 6749 and security best practices.
In addition, Stytch's Remote MCP Server Integration enables developers to build secure, OAuth-compliant Model Context Protocol (MCP) servers that allow AI agents to interact with applications on behalf of users. This integration leverages Stytch's Connected Apps feature to handle authentication and authorization flows.
Email Magic Links
Stytch’s email magic links enable end users to sign up or log into organizations via a single click of a tokenized URL. Users enter their email address at sign-in. If there’s a matching email address, they will receive a unique URL in their inbox. By clicking the link in their inbox, the users establish that they're the owner of the email address and are brought to an authenticated session.
Multi-Factor Authentication
Stytch offers phishing-resistant multi-factor authentication solutions for maximum flexibility and security, along with a suite of standard MFA methods (SMS one-time passcodes, email verification, and authenticator application-based authentication). Phishing-resistant MFA, built upon WebAuthn, employs device-based biometrics or hardware keys (e.g. YubiKey) to derail hackers looking to launch remote attacks. Unlike passwords, user biometrics are not stored or transferred over the internet. Biometric authentication in tandem with security key-based authentication leverages physical interaction to access relevant resources.
M2M Authentication
M2M (machine-to-machine) authentication enables secure, automated communication between devices and applications, commonly used by backend servers, automated workflows, IoT (Internet of Things) devices, external APIs, and more. Rooted in a zero-trust security model, M2M authentication ensures that no machine or service is inherently trusted and that every request must be continuously verified.
Stytch’s M2M authentication relies on OAuth 2.0 to verify identities and protect data exchanges. Developers can authenticate external clients against public APIs, secure internal service-to-service communication, and implement fine-grained access control with scopes and permissions. Continuous processes such as daemons and job schedulers can also be protected from unauthorized access.
RBAC
RBAC (Role-Based Access Control) models manage access to resources by assigning users to roles, with each role having associated permissions. Stytch’s RBAC model provides a flexible interface for managing user permissions in multi-tenant applications, with features like customizable roles, predefined permissions, and the ability to assign users to one or more roles.
SCIM
SCIM (System for Cross-domain Identity Management) automates user identity management across systems and applications, ensuring secure and efficient user data management, and is critical for companies managing a wide range of SaaS applications and other cloud-based services. It streamlines processes like user provisioning, updates, and deactivation, minimizing the risk of errors and security breaches.
Stytch’s SCIM offers a flexible API, helping organizations manage user lifecycles while minimizing security risks associated with inactive accounts or manual updates. Its integration offers reduced manual effort for account creation, updates, and deactivation processes.
Admin Portal
In 2024, Stytch launched its Admin Portal, a customizable suite of embeddable UI components within their frontend SDKs, enabling users' customers to self-serve and manage their authentication setup and accounts. Stytch’s Admin Portal, powered by the Stytch API and protected via their RBAC product, is designed to provide a centralized interface for managing authentication policies, roles, and multi-tenant configurations.
User Impersonation
In February 2025, Stytch introduced its User Impersonation feature, which allows administrators to impersonate users within their organization, eliminating the need for users to follow complex instructions or share credentials, without the delays and miscommunication typically associated with remote access tools. This feature is designed to facilitate troubleshooting, testing, and providing better user support by enabling admins to replicate user issues and manage authentication flows.
Event Log Streaming
Stytch announced its Event Log Streaming feature in February 2025, allowing users to stream authentication, authorization, and security event logs into external log management tools such as Datadog and Grafana. Prior to February 2025, Stytch logs were only accessible through the Stytch dashboard, but with the Event Log Streaming offering, logs can be correlated with other data sources for easier anomaly detection and investigation. The feature integrates Stytch logs into users’ observability stacks while maintaining control over log storage and retention. The feature was in beta as of April 2025.
Terraform
In February 2025, Stytch released v1.0 of their Terraform Provider in General Availability (GA), offering developers the ability to automate and scale their identity infrastructure. Prior to February 2025, configuration tasks required developers to manually complete a series of steps via Stytch’s Dashboard, but with Stytch’s Terraform feature, developers can now manage their Stytch projects programmatically via HashiCorp's Terraform, eliminating the need to manually use the Stytch Dashboard. Users can automate tasks such as creating new projects, configuring password settings, managing public tokens and secrets, and updating RBAC policies.
Stytch’s introduction of Programmatic Workspace Actions, through its Management API, enables developers to automate workflows by controlling various aspects of a Stytch project, such as creating auth projects, setting SDK configurations, managing tokens, and more. The release was designed to provide greater control, flexibility, and efficiency for managing multiple projects or performing bulk operations.
Fraud & Risk Prevention
The modern threat landscape continues to evolve, with malicious actors permeating applications via identity theft, business email compromise (BEC), phishing, AI bot attacks, and other forms of fraudulent activity. Stytch adopts a multifaceted approach to addressing this, equipping users with the ability to identify malicious application traffic with built-in controls for responding to bots, web scrapers, and bad actors. As of April 2025, Stytch’s fraud and risk dashboard offered real-time monitoring and improved data visualization, allowing for deeper insights into fraud patterns.
Device Fingerprinting
Stytch’s Device Fingerprinting product identifies unique devices based on aggregated information (e.g., browser type or version, operating system, IP address, and installed fonts), enabling organizations to differentiate between authentic users and potential bad actors. While Device Fingerprinting provides unique identifiers used to detect and block fraudulent actors, many existing solutions can be reverse-engineered by malicious attackers.
Stytch’s Device Fingerprinting approach obfuscates fingerprinting methodologies and maintains encryption at rest and in transit, effectively thwarting potential reverse engineering attacks. DFP identifiers function across incognito browsing, WebViews, VPNs, IP addresses, and other masking tools employed by such individuals. Stytch’s front-end authentication SDKs integrate directly with DFP, ensuring that developers can obviate tasks relating to authentication flows while ensuring additional layers of security afforded by Device Fingerprinting.
Device Fingerprinting can be employed in stopping bot activity, enforcing paywalls (detection of unique users and tracking of articles seen), personalizations for returning or anonymous users, and prevention of account takeover (detection of whether bad actors are attempting to credential stuff endpoints). Based on fingerprint review, suggested actions are categorized into allow (verified device profiles that align with the characteristics of known groupings), block (known bad or malicious device profiles that should be restricted from completing actions), and challenge (potentially malicious devices that should undergo 2FA or other extended user verification).
Strong CAPTCHA
While traditional CAPTCHAs are employed as a basic bot protection measure, they remain susceptible to CAPTCHA farms, where bad actors exploit public key architecture to generate scalable attack vectors for bots. Stytch’s Strong CAPTCHA insulates users from bots by eliminating the public key components from client-side browser environments, eliminating bot attacks that may lead to account takeover fraud.
CAPTCHAs can be added to existing signup, checkout, or login flows, integrating with Stytch’s authentication solutions. Users are prompted to respond to simple questions before being granted full access to services. Online education platform Gather notes that Stytch creates tokens and appends them to user sessions, enabling users to go from their inboxes to Gather’s applications fully authenticated.
One 2023 report found that just over half of all web traffic is human-generated, with bots forming a significant volume of traffic while stealing credit card numbers, sensitive logins, and personally identifiable information (PII). Sites looking to distinguish between humans and bots have traditionally employed CAPTCHAs, but modern CAPTCHA systems often expose their public key, enabling bots to scrape and submit public keys to CAPTCHA-solving services, where individuals can then manually resolve tests for bots.
Stytch’s Strong CAPTCHA removes the public key site from CAPTCHA architecture, eliminating the possibility of bots scraping or mass attacking applications. McGinley-Stempel notes that users of ecommerce sites are “inundated with stimuli and friction . . . they’re asked to accept these cookies, create an account with multiple fields required, and remember yet another password,” and Stytch may be positioned to provide quality commercial experiences while obstructing bots’ ability to distort user interactions.
Breach-Resistant Passwords
Stytch’s breach-resistant passwords enable members to sign up for or log into organizations via email addresses and passwords, with the option to add more granular restrictions around password length, character types, and password strength enforcement during the authentication process. zxcvb and Lowercase Uppercase Digits Special Characters (LUDS) form part of Stytch’s password strength assessment, with the former flagging the presence of common patterns or usage of dictionary words, and the latter checking for the presence of lowercase or uppercase letters, digits, and special characters.
Breach detection, powered by HaveIBeenPwned, works in tandem with password strength enforcement to restrict unauthorized access to sensitive information by tracking compromised credentials and triggering password resets. Stytch supports an array of password hashing algorithms for migrations (e.g., bcrypt, scrypt, argon2i, argon2id, md_5, and sha_1), along with account deduplication for stronger fraud protection to mitigate password breaches and any compromise of user information.
Intelligent Rate Limiting
Stytch’s Intelligent Rate Limiting (IntRL) improves the detection of low-volume, targeted fraudulent activity. The system uses dynamic device and traffic sub-signals, rather than relying solely on IP addresses, to identify sophisticated attacks, including automated browser activity from tools like Puppeteer, Selenium, Anthropic’s Computer Use API, OpenAI’s Operator, etc.
Dashboard Features
As of April 2025, key updates to Stytch’s fraud and risk dashboard include enhanced data visualization, with live chart view providing real-time insights into traffic health, and event log filtering, allowing users to apply filters like ExternalID, OrganizationID, and UserAction for investigation. Additionally, rule creation enables users to generate authorization rules directly from the dashboard, expediting responses to false positives or negatives.
Consumer Authentication
Source: Stytch
WebAuthn
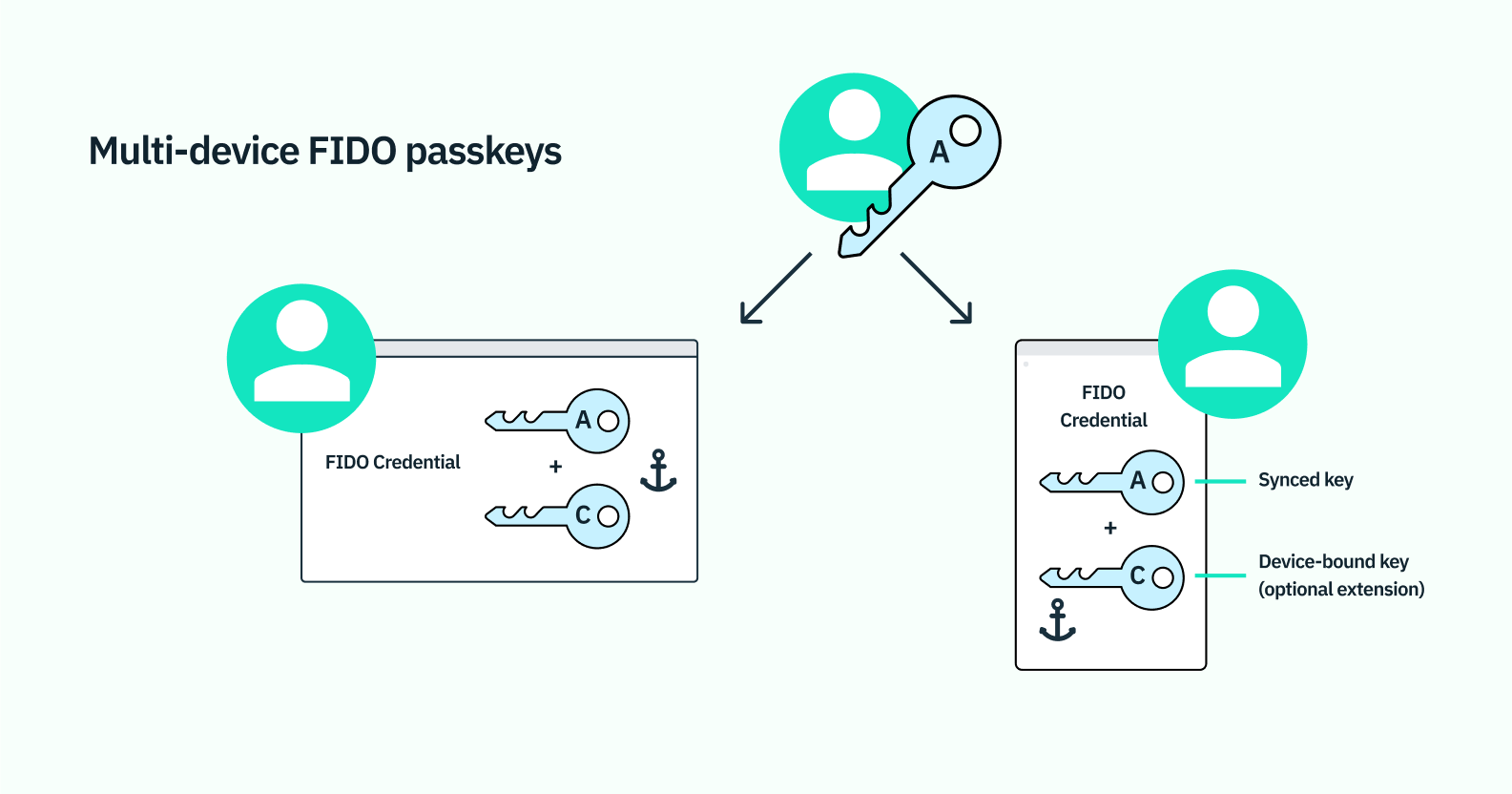
WebAuthn (Web Authentication) standard, developed by the World Wide Web Consortium (W3C) and the Fast Identity Online (FIDO) alliance, is a passwordless authentication method that uses public-key cryptography. When a user attempts to register on a website that supports WebAuthn, the website asks the user’s browser to create a public-private key pair via the WebAuthn API. The private key is stored in the user’s authenticator (e.g., built-in biometrics, security key), while the public key is sent and stored by the website.
When a user tries to access their account, the website sends a challenge request to the browser, prompting the user to authenticate using their registered authenticator. Once the authenticator signs the challenge with the private key, it sends the signed response back to the website, which verifies the response using the public key stored during registration. WebAuthn is fundamental in two-factor and multi-factor authentication (MFA). Stytch’s WebAuthn API supports two authentication methods to verify user identities - built-in device biometrics (e.g. FaceID, TouchID) or cross-platform hardware keys (e.g., YubiKey).
Passkeys
Passkeys, developed by Fast Identity Online (FIDO), provide a biometrics-based, phishing-resistant password alternative. When users are prompted to sign into applications, the user may opt to sign in with the same biometric used to unlock the device (e.g,. FaceID, TouchID), and the application can then use this mechanism in favor of insecure traditional username and password logins. Passkeys, based on FIDO authentication, are proven to be resistant to phishing threats, credential attacks, and other common remote attacks.
While the public key is registered with the application, the private key is stored locally on the device or client originally used for biometric verification. When users send login requests, the application’s server will submit a challenge decryptable only with the private key. Once the user has verified their identity via biometrics, the private key can be used to resolve the challenge, and the device sends a signed response back server-side, verifying the response and admitting users to the application.
Passwords, which are susceptible to phishing and credential stuffing attacks, remain insecure methods of authentication. Even second-factor authentication — notably, one-time passwords (OTPs) and external mobile approvals — pose issues relating to user accessibility and can be vulnerable to phishing as well. Stytch’s Passkeys offer a complete replacement for passwords as a more secure, user-friendly approach to verifying user credentials by combining the security of web authentication (WebAuthn) with biometric authentication.
OAuth / Social Login
OAuth / Social Login options like Google enable users to easily sign up and log into applications without creating new credentials. Google One Tap, which detects the user’s existing logged-in Chrome or Gmail sessions, provides the option to continue with a recognized account. If the user opts to use an existing account and is already logged into the account on their device, sign-up becomes a one-click process. As of April 2025, Stytch supports a number of OAuth providers. Examples include social logins such as Google, Facebook, Microsoft, and Apple; GitHub, GitLab, and BitBucket for developer tools, and other prominent OAuth providers such as Coinbase, Discord, Slack, and Twitch.
One-Time Passcodes
Stytch’s one-time passcodes (OTP) enable users to log in using temporary-use passcodes, which are delivered via SMS, WhatsApp, or email, and can be used to prevent seamless cross-device logins and account takeover attacks. Authentication flows can be built with Stytch’s APIs and SDKs, with a single screen to accept a phone number or email, and a secondary screen to confirm the one-time passcode. By default, OTPs expire within two minutes, but developers can adjust the expiration time to their preferred duration. After clicking on the link, users are verified and authenticated instantaneously, and developers can choose to include additional verification at any point within the user session.
Web3 Logins
Stytch’s web3 logins allow companies to add support for crypto wallets by employing the company’s APIs or SDKs to onboard or authenticate users via Ethereum (such as Metamask or MyEtherWallet) or Solana wallets (such as Phantom or Glow Wallet).
Session Management
Stytch’s session management tools provide granular session management controls over the validation and revocation of sessions. Stytch user sessions are identified by a session token or session JSON web token (JWT) stored client-side (interoperable, both returned on every API response) and authenticated on each request. Stytch’s JSON Web Tokens (JWTs) provide a means of locally verifying user sessions without needing to contact Stytch’s servers on every request, which proves particularly useful for developers looking to lighten server load and bolster latency.
Passwords
Despite leading with its passwordless product solutions, Stytch also offers the ability for customers to authenticate their users via a password. Passwords are a simple way to protect information but are vulnerable to security risks if they are weak, reused, or not regularly updated. Stytch provides a traditional password-based authentication solution with built-in security features to enhance account protection. The platform includes password strength checks to enforce secure credential creation in accordance with the NIST password guidelines and reset capabilities to facilitate account recovery.
Embeddable Magic Links
Stytch’s embeddable magic links create one-time, one-click mechanisms to authenticate users, eliminating reset password flows or external password managers. While email magic links are constrained to inboxes, embeddable magic links can be included within any outbound messaging of choice. By embedding tokens into CTAs within email, SMS, or other marketing channels, users can access applications without re-authenticating.
From Stytch’s embeddable magic link endpoint, developers can generate tokens to include in preferred communication channels before sending the magic link to customers. By clicking on the link, users are instantly authenticated and can begin sessions. Developers are given the option to include additional authentication at any point within the user journey.
Market
Customer
Stytch offers authentication solutions across industries. Instead of spending developer cycles building bespoke user authentication flows, enterprise or B2B customers employ Stytch in building out SSO or MFA. As of April 2025, notable customers include Cisco, Replit, Hubspot, Descript, Together AI, Workday, and Calendly.

Source: Stytch
Customer Use Cases
Usage-based pricing startup Orb offers SSO, which had previously evaluated Auth0, but came to the conclusion that Auth0 would be incapable of handling session management. Many other SSO providers required additional coding, extensive customization, and branching paths for auth customers. With Stytch, Orb was able to abstract away complexity from the authentication process, ensuring that the platform could manage diverse auth SSO requirements with minimal lift.
Replit, an AI-powered platform for developers, has a free offering with some hosting and compute resources. The free offering is intended to give new Replit customers the chance to test out the platform, but it is commonly a target for bad actors to run phishing attacks or crypto-mining. Replit realized that the best way to stop these users was at sign-up and leverages Stytch to stop abuse at sign-up and prevent downstream fraud.
Irish fintech company Unbanx, which allows consumers to sell aggregated anonymized data to ethical buyers, employs Stytch’s passwordless SMS passcodes to optimize its sign-up flow. With Stytch, users can complete Unbanx’s three-step onboarding flow quickly, and verification takes place via text instead of the lengthier process demanded by Amazon Cognito.
Real estate lender Flatiron Realty Capital similarly needed a full-service authentication solution to aggregate relevant documents within the umbrella of a single user account. Within a week, Flatiron was able to implement Stytch’s sign-up and login flows, with the option to tack on SMS OTPs or TOTP authenticator applications downstream in the user journey.
Bitcoin.com opted to implement Stytch’s EML solutions instead of an in-house build to resolve support tickets from users losing their keys. While developers had already built sign-up and login flows, they quickly realized that their approach necessitated overwhelming maintenance at scale, especially with the addition of new use cases, features, and product suites. The company’s partnership with Stytch has eliminated much of the authentication maintenance previously required, especially given Bitcoin.com’s cross-platform presence across web, mobile, and external partners.
Market Size
With Stytch’s core offering allowing customers to become enterprise-ready, the company straddles both the authentication market and the security and compliance market. The global identity and access management market was valued at $22.9 billion in 2024 and is expected to reach $34.3 billion in 2029, driven by a rise in security breaches and identity-related fraud cases.
The need for multi-modal security across the cloud has accelerated demand for customer identity and access management (IAM) solutions, with the global IAM market projected to expand from $15.7 billion in 2023 to $32.6 billion in 2028. Enterprise identity providers have moved beyond enterprise offerings to include customer identity management (e.g. Okta’s Auth0 acquisition), with leading authentication/authorization platform Okta expected to generate a sizable chunk of its revenue from customer IAM.
With over 66% of smartphone users expected to use device-native biometrics by 2024, passkeys have begun to build the foundation for a passwordless future. Authentication protocols (notably, FIDO2 and WebAuthn) have set the stage for developers to add passwordless authentication methods (in tandem with OTPs, magic links, and other forms of authentication) to their applications.
On the fraud side of the equation, the global fraud and prevention market was valued at $58 billion in 2024 and is projected to grow to $246 billion by 2023. Common fraud and risk prevention methods include bot detection, device fingerprinting, and anomaly detection.
Competition
Auth0 (Okta): Founded in 2013, Auth0 raised over $330 million before Okta acquired the company for $6.5 billion in an all-stock deal in March 2021. The acquisition, an approximate 3.5x jump in Auth0’s valuation from the previous year, expands Okta’s workforce identity management coverage to include customer identity.
Auth0 was expected to generate over $200 million in annual recurring revenue (ARR) in 2022. In SEC filings, Okta announced its 2022 Q4 revenue to be $383 million, which was an increase of 63% YoY. While Auth0 might prove sufficient for developers looking for boilerplate authentication with limited customizability, Stytch supports a broader range of biometric logins (native biometrics on Apple devices via an iOS SDK), along with web3 logins (built-in support for Ethereum and Solana logins).
Developers commonly implement Auth0 via universal login, a modal hosted by the platform that provides login methods out of the box. Because universal login is Auth0-hosted, users are redirected away from log-in or sign-up pages, forcing them to authenticate via Auth0 or another custom domain before redirecting them back to the original page or application. By opting to use Stytch, developers fully own the UI/UX, eliminating redirection and bolstering user conversion rates. Lighthouse notably claimed that it improved conversion by 62% after switching from Auth0 to Stytch. See a side-by-side comparison of both companies, written by Stytch, here.
Fingerprint: Fingerprint, a JavaScript-based client-side browser fingerprinting library, queries browser attributes and computes a hashed visitor identifier. The commercial version of Fingerprint enables developers to implement fingerprinting in non-production environments, with over 6K companies using Fingerprint’s real-time device intelligence to ascertain user intentions as of April 2025. Fingerprint provides a wholesale view of users across web and mobile applications, with up to 99.5% identification accuracy by employing fingerprinting, fuzzy matching, and server-side techniques.
While Fingerprint performs some transport layer security (TLS) fingerprinting, such fingerprinting returns identifiers client-side, where they are then vulnerable to tampering. Stytch offers priority TLS and network fingerprinting, both performed entirely server-side, along with encryption on-wire and at rest. See a side-by-side comparison of both companies, written by Stytch, here.
WorkOS: WorkOS was founded in 2019. It offers a suite of enterprise-ready solutions for identity and access management (IAM). Its product lineup includes tools and APIs that enable developers to integrate crucial features into their applications. In June 2022, WorkOS raised an $80 million Series B round at an undisclosed valuation led by Greenoaks, with participation from Lachy Groom, Lightspeed Ventures, and Abstract Ventures. As of January 2024, WorkOS has raised $95 million in total funding.
Supabase Auth: Supabase Auth, first launched in 2020, is an open-source authentication solution. Supabase enables user management, row level security (RLS), and the ability to set policies. Similar to Stytch, Supabase describes itself as providing simple APIs, enabling developers to easily set up auth on their respective apps. Supabase supports sign-up, sign-in, magic links, and OAuth logins. In September 2024, Supabase raised an $80 million Series B round at an undisclosed valuation led by PeakXV and Craft Ventures. As of January 2025, Supabase has raised $196 million in total funding.
Amazon Cognito: Amazon Cognito enables developers to add user sign-up and sign-in features via a scalable identity store with support for both social and enterprise identity federation. Processing over 100 billion authentications each month as of January 2024, Cognito helps users implement customer identity and access management (CIAM) into both web and mobile applications. Notable customers include NHS Digital, Trend Micro, and Neiman Marcus.
Amazon Cognito may prove sufficient for simple authentication flows built around passwords and social OAuth logins or companies already using AWS, but may prove constricting in terms of advanced authentication features and backend stack flexibility. While Cognito’s advanced security features only support multi-factor authentication (MFA) via SMS and TOTP, Stytch’s API-first approach enables developers to construct more nuanced, bespoke application logic. Apart from authentication, Stytch also provides flexible fraud tools, including device fingerprinting, which provides more granular logic around addressing or triaging traffic according to risk level.
Apart from the competitors described above, other relevant startups in the IAM space include Descope, which provides drag-and-drop authentication and identity management for consumer-facing businesses, and Ory, a web-scale API for identity and access control. See a side-by-side comparison of both companies, written by Stytch, here.
Business Model
Authentication Pricing
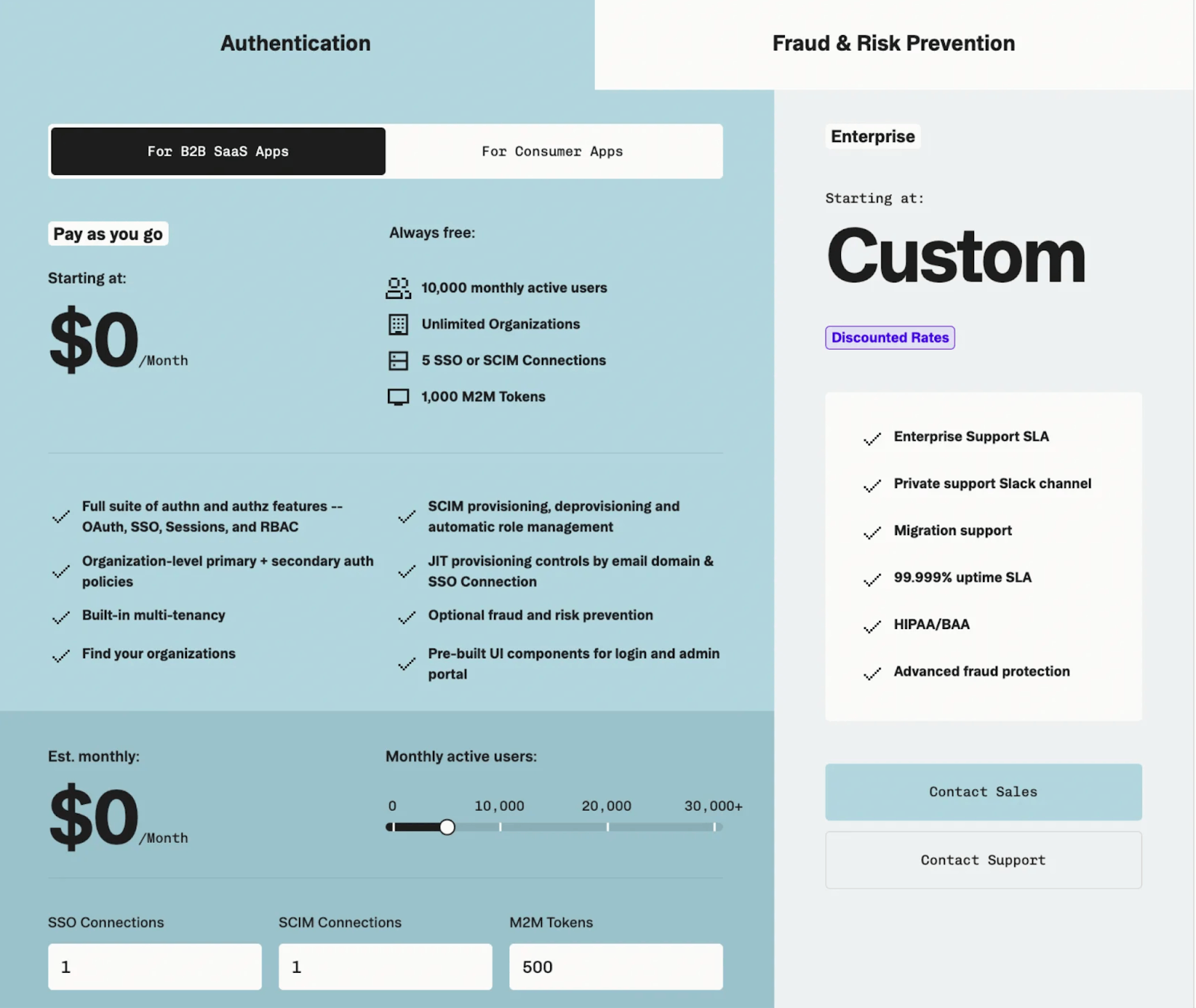
Source: Stytch
Stytch has pay-as-you-go pricing that scales with the number of users their client is trying to authenticate, starting at $0/month when there are fewer than 10K monthly active users for both B2B SaaS Apps and Consumer Apps. This includes its full suite of authentication and authorization features such as OAuth, SSO, Sessions, and Role Based Access Control. From there, Stytch’s pricing includes optional add-ons such as a customizable brand and login experience for $99, additional SSO or SCIM connections beyond the included 5 for $125/connection, and a wide range of fraud and risk prevention features such as CAPTCHA, bot detection and prevention, device fingerprinting and intelligent rate limiting.
Fraud & Risk Prevention Pricing
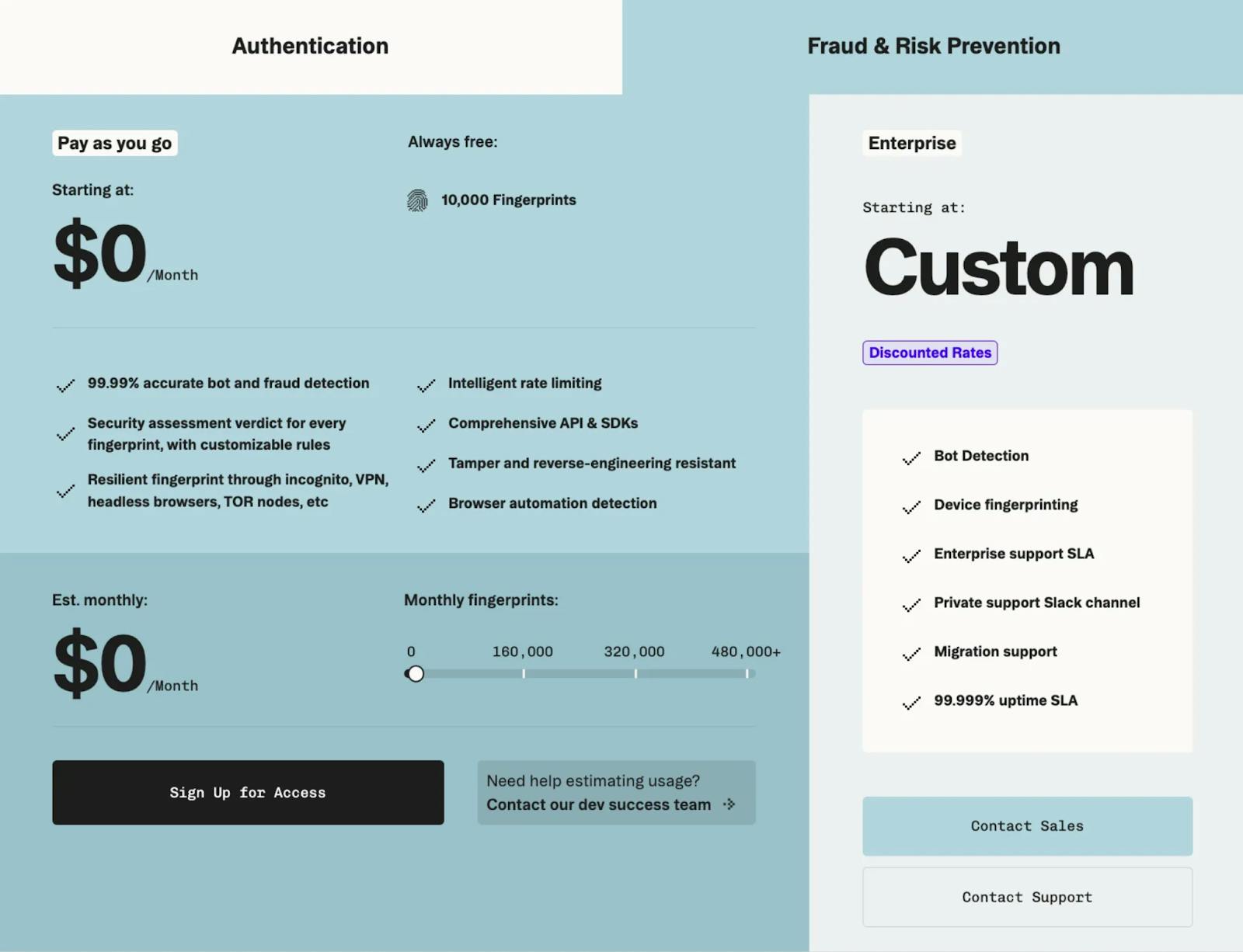
Source: Stytch
For Fraud & Risk Prevention, Stytch’s pricing also scales with the number of users, with $0/month when there are less than 10K monthly fingerprints. Beyond that, fingerprints are $0.005 each (or $5 for 1K fingerprints).
Traction
Notable customers of Stytch as of April 2025 include Hubspot, Cisco, Calendly, and Zapier. Most organizations lack a standard “buyer” for authentication products, so Stytch’s directed approach to introducing solutions at developer-centric conferences was a critical aspect of the company’s product-led growth (PLG) strategy.
Stytch’s changelog indicates that the company has continually released features, product improvements, and broader bug resolutions. In December 2023, the company announced the availability of role-based access control (RBAC), along with passkeys for consumer applications. In February 2025, RBAC and SCIM solutions were made available to users requesting early access, along with OAuth custom parameters and device fingerprinting-protected authentication just a few weeks prior. The company has continued to release new features, with 2025 featuring intelligent rate limiting, connected apps that enable integrations with AI agents, third-party apps and multi-app ecosystems, admin portal, user impersonation, event log streaming, and more.
Valuation
In November 2021, Stytch secured $90 million in Series B funding in a round that valued the company at over $1 billion and brought the company’s total funding to $126.3 million. The round, led by Coatue Management, included participation from Contrary and existing investors, notably Benchmark, Thrive Capital, and Index Ventures. Stytch’s Series B came just four months after the company’s $30 million Series A, which valued the company at approximately $200 million. Prior to this, Stytch raised a $6 million seed round led by Benchmark in the summer of 2020. Stytch has not raised another round of funding since November 2021.
Key Opportunities
Strategic Acquisitions
Following the company’s Series B, Stytch acquired passwordless authentication startup Cotter at the time of its Series B in 2021. Cotter simplified logins via mobile app prompts, OTPs, magic links, and WebAuthn-based biometric authentication. In line with other acquisitions by relevant competitors in the space, such as Bitwarden’s acquisition of Swedish passwordless startup Passwordless.dev, Stytch may expand existing offerings to help modernize applications that presently rely on passwords for authentication. In a similar vein to Cotter, Passwordless.dev provides APIs built atop WebAuthn, simplifying the process for developers to bring WebAuthn to software via just a few lines of code.
End-to-End Identity Management
Stytch has positioned itself as an end-to-end identity platform for developers. Announcements around the general availability (GA) of passkeys in December 2023 signaled increasing interest in expanding cross-platform authentication methods and facilitating the migration to more secure, passwordless alternatives.
Stytch intends to become Stripe for passkeys by handling the building and implementation of passkeys from scratch. McGinley-Stempel noted in December 2023 that he remains bullish on passkeys being the largest accelerant towards passwordless adoption, with major players adopting passkeys as their preferred mode of authentication. Existing passkey solutions often constrain developers’ ability to customize application logic and UIs, creating disjointed user experiences and widening attack surfaces for security vulnerabilities.
As a broader provider of IAM solutions, Stytch may be well-positioned to become the platform of choice for companies looking to deliver enterprise-grade authentication alongside frictionless user experiences. By enabling businesses to centralize efforts around building core features instead of in-house authentication, Stytch can help reduce the engineering overhead required to build and manage authentication for applications. Stytch may become the authentication platform of choice for companies as they scale by providing the flexibility to support both status quo and future authentication needs.
Key Risks
IAM Incumbents & Emerging Players
Apart from Okta’s Auth0, startups operating in the identity and authentication space have developed customizable solutions around biometric onboarding and passkeys, along with KYC capabilities. Footprint, for example, vaults identity, payment card, and customer key-value data; identity data originating from user onboarding flows is verified via the decisioning platform and then secured.
Beyond authentication, Footprint bridges the gap between onboarding, authentication, and identity access management, providing an end-to-end approach that eliminates tradeoffs between fraud and friction. Footprint also links security to fraud and KYC, ensuring that individuals with verified identities can create accounts within the given ecosystem once cleared.
Within the identity access management realm, startups like Opal Security provide consolidated views and more granular employee access control to internal tooling, company applications, and environments. Other vendors including SailPoint and Veza are among a myriad of solutions operating in the enterprise identity security space.
Boston-based Transmit Security, meanwhile, offers biometric-based authentication capable of handling over 9K authentication requests per second. The company counts UBS, Lowe’s, and SunLife Financial among its enterprise customers, but also services a broad range of non-profits, fintechs, retailers, and other health systems via the company’s suite of customer identity solutions.
Stytch aims to differentiate itself from other identity and access management (IAM) solutions via a developer-friendly, API-first approach. in contrast to other players that require developers to utilize widgets, Stytch provides flexibility in terms of owning both the design and core workflows that can be built around the company’s APIs and SDKs. In a similar manner to how Stripe has streamlined payments, Stytch aims to abstract away nitty-gritty details around authentication so that developers have more control over user flows.
Deployment Hurdles
Beyond optimizing the developer experience of constructing authentication flows, Stytch grapples with reshaping traditional reliance on passwords. Organizations considering a transition to passwordless authentication might require compatibility between passwordless solutions and existing systems. Enterprise adoption requires full verification of application compatibility, with planning required to ensure that all applications and company-sponsored devices can support passwordless solutions.
For legacy solutions incompatible with passwordless authentication, identifying outliers in use cases might require alternative authentication remediation paths. Organizations capable of easily adopting emerging solutions (such as Stytch) may avoid needing to replace legacy infrastructure and embrace passwordless forms of authentication. But passwordless deployment typically requires a phased approach, with deployment occurring first via a VPN or remote access portal. Microsoft notes that the process of transitioning to passwordless mechanisms may take a considerable amount of time, and organizations looking for passwordless options should be willing to commit resources and time to the development of password replacement offerings.
In addition, IAM leaders are often uncertain of what passwordless authentication might entail, and the lack of universal solutions can prove difficult for both enterprises and their customers. Even if larger enterprises are seeking ways to eliminate security risks associated with weak passwords, workers might also be resistant to biometric authentication, especially in the face of possible privacy concerns.
Summary
Stytch is a developer-first identity and access management (IAM) platform that helps applications become enterprise-ready by simplifying authentication, authorization, and security. Founded in 2020 by Plaid alums Reed McGinley-Stempel and Julianna Lamb, Stytch offers a flexible suite of tools — including SSO, OAuth, MFA, RBAC, and fraud prevention features like device fingerprinting and intelligent rate limiting. An authentication provider, its APIs and SDKs support both B2C and B2B authentication use cases, enabling seamless onboarding, session management, and user provisioning. With customers like Cisco, Replit, and HubSpot, Stytch differentiates itself by giving developers full control over authentication flows and user experience. As security needs grow more complex, Stytch positions itself as a modern, customizable solution for building secure, scalable identity infrastructure.
*Contrary is an investor in Stytch through one or more affiliates.