Thesis
Cybercrime continues to increase with time, and attacks are becoming more advanced. In Q2 2024, global cyberattacks increased by 30% compared to the same period in 2023. Organizations now face an average of 1.6K attacks per week. Financial losses from cybercrime hit $16 billion in 2024 and are expected to grow to $15.6 trillion by 2029. The average cost of a data breach has reached an all-time high of $4.9 million.
These attacks are becoming especially dangerous due to AI. Cybercriminals are using AI tools to scale phishing attacks and create realistic voice or video scams. The FBI has issued warnings about these threats. In response to the shifting landscape, 75% of businesses report that security is becoming a bigger priority.
At the same time, cloud adoption has become a major shift across industries, with more companies moving their operations and data to cloud platforms. As of May 2025, 94% of organizations with over 1K employees ran a significant portion of their workloads in the cloud. Additionally, 54% of enterprises plan to move more workloads to the public cloud by May 2026. The prevalence of sophisticated cyberattacks and the widespread adoption of cloud computing among large enterprises present a substantial market for cloud-based security and management solutions.
Tanium is positioning itself to meet this need. Its XEM (Converged Endpoint Management) platform focuses on securing and managing endpoints, an area critical for protecting cloud-based environments. The platform allows organizations to gain real-time visibility and control over their devices, ensuring systems are up-to-date, compliant, and protected against threats.
Founding Story
Tanium was founded in 2007 by father-son duo David Hindawi (Executive Chairman) and Orion Hindawi (Executive Chairman).
David, born in Iraq and raised in Israel, earned his Bachelor of Science and Master of Science in Industrial and Management Engineering from the Technion. He also has a Ph.D. in Operations Research from the University of California at Berkeley. He has various software patents in network communications and systems management.
The Hindawis had previously worked together on BigFix, an endpoint security company founded during the dot-com boom. Orion had dropped out of UC Berkeley to join his father in building the company. While BigFix found early success, it faced challenges during the tech downturn and was eventually sold to IBM for $400 million in 2010. Both David and Orion left BigFix before the acquisition and soon began work on what they saw as a more scalable, cloud-focused successor—Tanium. Their goal was to solve the same core problem of endpoint security but do it better, with faster performance and more reliable data.
Despite their initial skepticism toward venture capital, stemming from earlier fundraising experiences at BigFix, the Hindawis eventually accepted $90 million in funding from Andreessen Horowitz in 2014.
David and Orion Hindawi led the company through its formative years, with Orion taking over as CEO in 2016 and David stepping into the role of Chairman. In the years following, Tanium made several critical executive hires to support its growth. In 2017, the company brought in senior leaders, including Fazal Merchant, the former CFO of DreamWorks, first as COO and CFO in May 2017, before he became co-CEO in June 2019. In addition, Tanium added Mark Wayland as Chief Revenue Officer in July 2017 and Chris Bream as CTO in May 2017. Between 2020 and 2021, Tanium saw high turnover at the executive level, with the departures of co-CEO Merchant, CFO Jim Jackson, CMO Chris Pick, and others. Orion Hindawi acknowledged internal leadership challenges and used the moment to reset company culture and strategy.
In May 2021, Tanium appointed Marc Levine as CFO, leveraging his experience at RSA Security, C3.ai, and HP to bolster financial operations. That July, the company hired Teddra Burgess as SVP of Public Sector to expand its government footprint, drawing on her background at HP and ASG Technologies. The most significant leadership change came in February 2023, when Dan Streetman, former CEO of Allvue Systems and Tibco, and a US Army veteran, was named CEO. Orion transitioned to Executive Chairman, and David became Chairman Emeritus. As of June 2025, under Streetman’s leadership, Tanium reinforced its executive bench, including Tyker Fagg as Chief Revenue Officer and Christian Hunt as Senior VP of Engineering.
Product
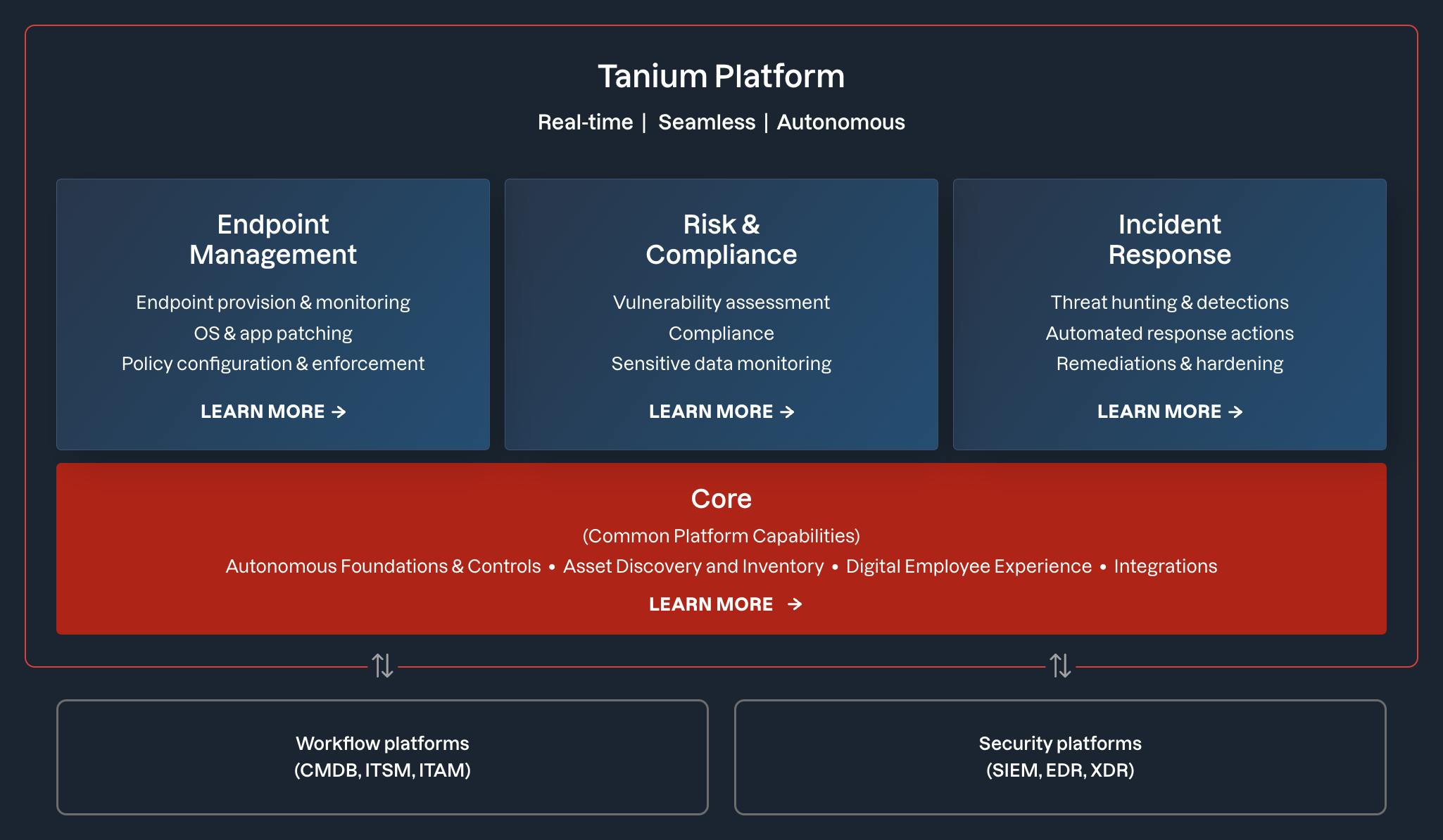
Source: Tanium
Tanium is a unified endpoint management and security platform that provides real-time visibility and control across all endpoints in an enterprise. It helps organizations streamline endpoint management, ensure risk and compliance through continuous monitoring, and accelerate incident response by enabling instant investigation and remediation from a single platform. This consolidation reduces tool sprawl and empowers IT and security teams to act quickly and at scale.
Endpoint Management
Tanium's Endpoint Management solution provides a centralized platform for managing the entire lifecycle of IT assets from initial provisioning to decommissioning. It supports multi-OS environments including Windows, macOS, and Linux, and offers features like bare-metal imaging, patch management, software deployment, and self-service tools for end users. The platform claims significant efficiency gains, such as provisioning endpoints up to eight times faster than traditional tools. It also includes a pre-built gallery of common applications for easier deployment and supports automated patch scheduling and compliance enforcement.
The solution is part of Tanium's broader real-time platform, integrating with risk management, incident response, and IT operations tools. It emphasizes real-time visibility and control across all endpoints, enabling IT teams to respond faster to vulnerabilities which, according to Tanium, are typically exploited within 40–60 days of discovery. The product is designed to address the growing complexity of endpoint environments, with the number of devices per user reportedly increasing year over year. It integrates with external systems like ServiceNow and SIEM tools, supporting automated workflows and IT service management.
Customer testimonials highlight increased visibility into patch compliance, reduced operational workload, and better endpoint hygiene. Tanium’s approach aims to replace fragmented endpoint tools with a unified platform that improves security, speeds up IT operations, and scales to enterprise needs.
Software Inventory & Usage (SIU)
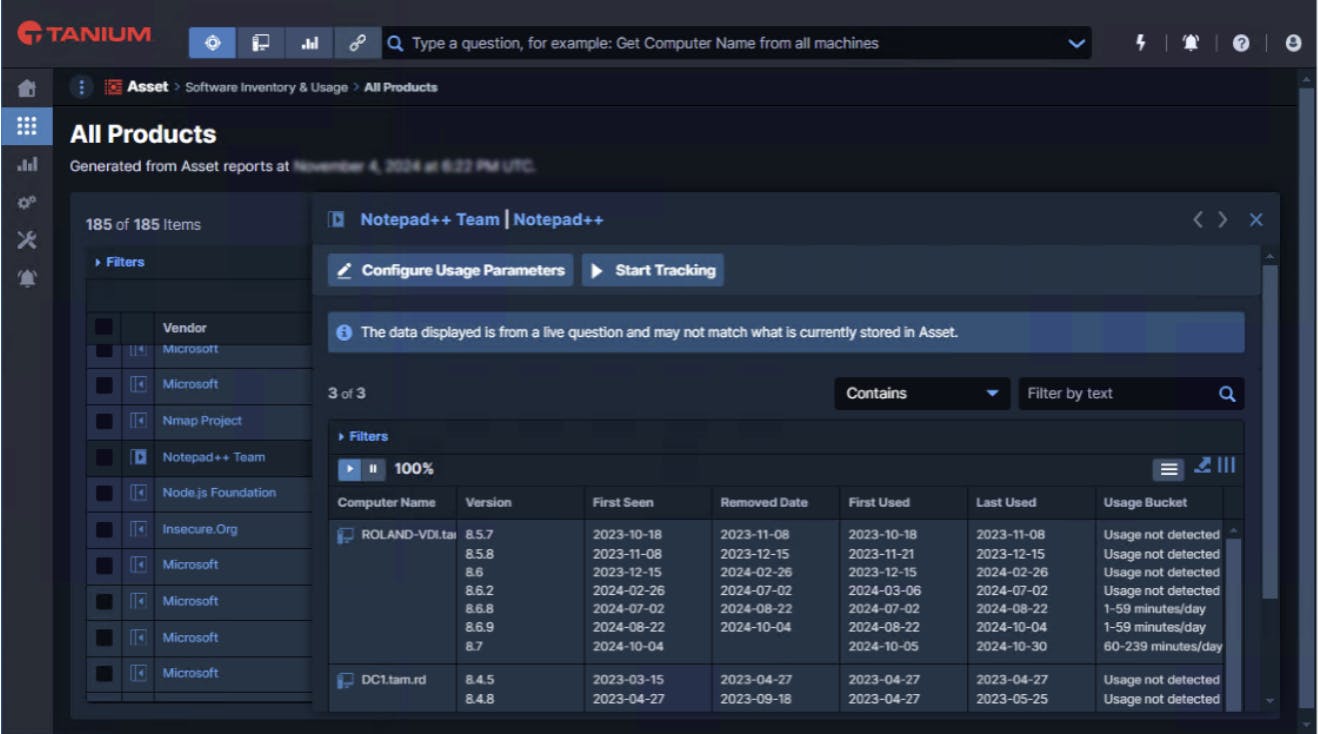
Tanium’s SIU solution allows organizations to identify all running applications across their environment, regardless of installation method. This includes software installed via traditional means, as well as applications introduced through less conventional methods like USB transfers or downloads from shared drives. By capturing this breadth of data, SIU allows for accurate software inventory that catches untracked or unauthorized software (visible in image below)
This module is able to normalize software naming conventions automatically. By resolving inconsistencies in vendor and product names, such as varied spellings, versions, or aliases, Tanium reduces the manual effort that is typically required to clean and fix software inventories. This automated normalization leads to more consistent reporting and a clearer understanding of software footprints across various distributed environments.
Tanium also provides detailed and configurable usage metrics. Administrators can define thresholds like minimum usage time per day or week to determine whether a given application is actively being used. This allows organizations to identify underutilized software, properly size their license allocations, and support cost-optimization initiatives.
In addition, Tanium provides real-time software usage data, which allows IT and security teams to quickly assess how applications are being utilized across their infrastructure. This could speed up decision-making during audits, investigations, or compliance reviews.
Source: Tanium
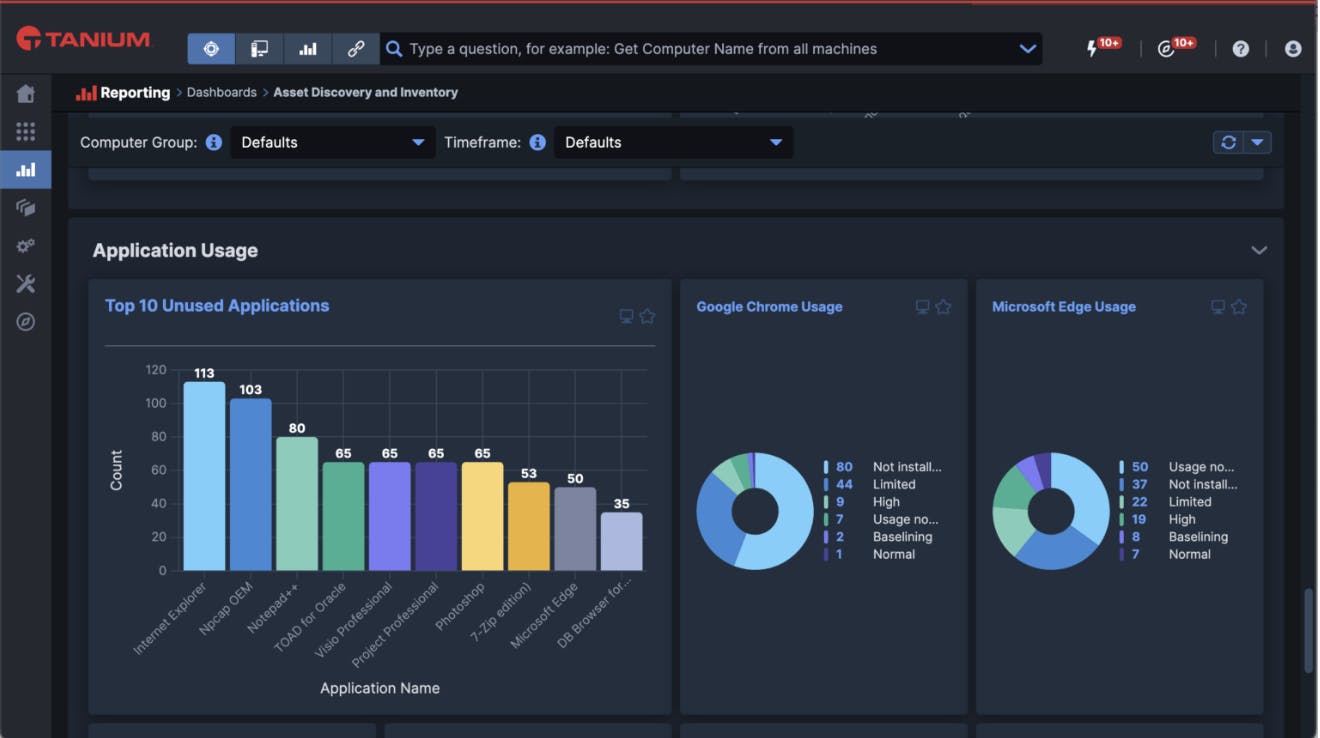
The SIU module is also designed for flexibility in how information is accessed and shared. It allows teams to query and visualize inventory and usage data using natural language and customizable dashboards, allowing them to derive meaningful insights without requiring extra data processing skills (shown in the image below).
Source: Tanium
Lastly, Tanium supports integration with external systems such as Configuration Management Databases (CMDBs) and asset management tools. By exporting normalized and up-to-date inventory and usage data into broader IT ecosystems, organizations can maintain a consistent source of information across platforms.
Client Management
Tanium's Client Management module focuses on endpoint management by emphasizing real-time visibility, streamlined operations, and proactive maintenance to ensure that IT environments remain secure, compliant, and efficient.
At the core of Tanium's Client Management is its ability to quickly discover and inventory all endpoints within an organization. Traditional tools often require extended periods to scan environments, resulting in outdated and incomplete data. In contrast, Tanium enables IT teams to scan their entire environment in minutes, providing an accurate and up-to-date picture of all endpoints and their statuses.
Once endpoints are identified, Tanium rapidly deploys patches, updates, and policies across the network to ensure that systems are compliant with security standards and reduce vulnerability to potential threats. Tanium's platform also minimizes network load during these operations, which prevents disruptions to more critical applications of the organization.
Beyond deployment, Tanium offers various tools for software management. IT teams can easily assemble, distribute, and remove software packages, simplifying the software lifecycle process. This capability is coupled with Tanium's performance monitoring features, which continuously evaluate endpoint health and proactively identify/address performance issues.
An advantage of Tanium's Client Management solution is that it consolidates multiple point tools into a single platform, which reduces the complexity of IT operations. It also ensures that all stakeholders are aligned in their understanding and approach to managing the IT infrastructure.
Asset Discovery
Tanium enables the identification of all endpoints, both managed and unmanaged, across cloud, on-premises, and hybrid environments. This real-time discovery helps organizations maintain an up-to-date inventory of their IT assets.
For each discovered device, Tanium collects comprehensive data, including hostname, MAC and IP addresses, operating system details, open ports, and historical information such as the first and last time the asset was seen on the network.
The platform supports integration with Configuration Management Databases (CMDBs), Security Information and Event Management (SIEM) systems, and other third-party tools. This facilitates a unified view of asset data across various IT management platforms.
By providing accurate and current asset data, Tanium assists organizations in making informed decisions regarding hardware and software management, including license optimization and risk reduction strategies.
Risk & Compliance Management
Tanium’s Risk & Compliance Management solution provides organizations with real-time visibility into vulnerabilities and configuration gaps across their entire IT estate, including endpoints, containers, and cloud workloads. It continuously scans all assets without impacting network performance, consolidates risk data into both generic and custom categories, and offers real-time risk scores at the endpoint and organization level.
The platform makes it easier to prioritize remediation efforts by correlating risk with endpoint criticality and lateral movement potential, benchmarking against peer data, and enabling cross‑team collaboration through shared datasets. Users can pivot from risk assessment to remediation, deploying and validating fixes in real time across managed and unmanaged systems as well as Kubernetes environments.
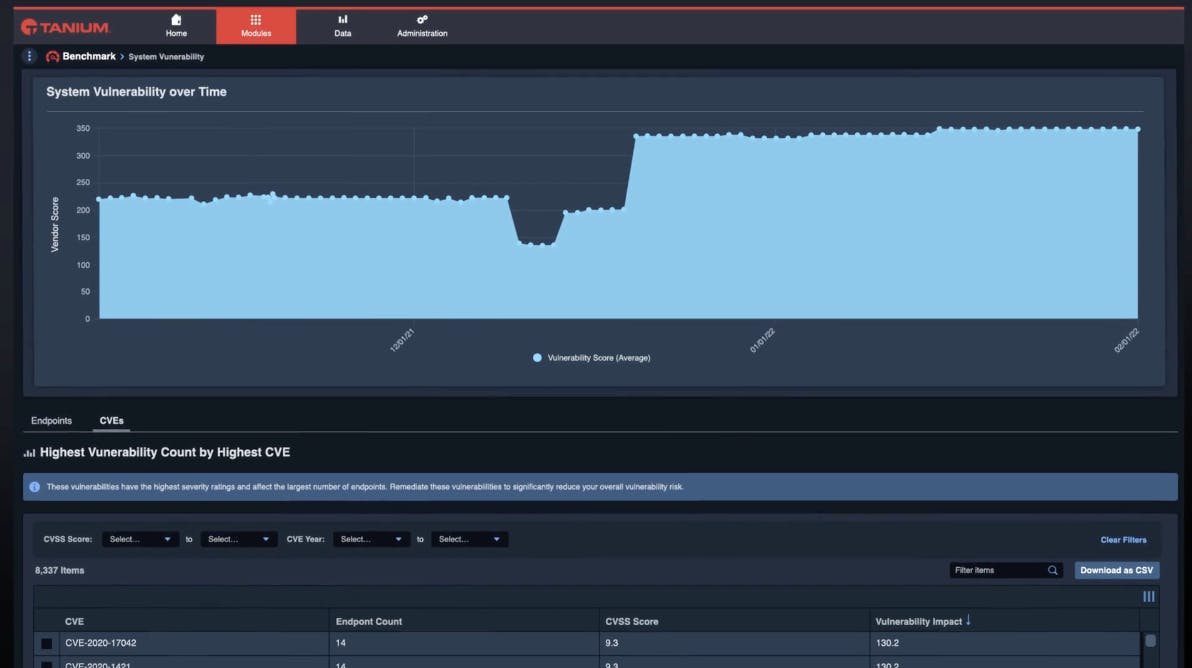
Tanium continuously scans all endpoints and container image registries for vulnerabilities and compliance gaps. This process is designed to finish in minutes without overloading the network, allowing rapid visibility into potential risks across the entire IT estate.
The platform assigns dynamic risk scores to individual endpoints and the organization as a whole. These scores are based on multiple factors, including vulnerabilities, threats, compliance status, and patch levels, enabling security teams to prioritize remediation efforts effectively (shown in the image below).
Source: Tanium
Tanium transitions from identifying vulnerabilities to executing remediation actions such as patching, software updates, and configuration changes. This integrated approach allows for immediate validation of fixes, simplifying the vulnerability management lifecycle.
The solution supports Security Content Automation Protocol (SCAP) and Open Vulnerability and Assessment Language (OVAL)-based content, including custom checks. This flexibility enables organizations to align with various regulatory requirements like PCI, HIPAA, and SOX, as well as internal security policies.
Technical Implementation Principles
Tanium’s compliance model is built around four key technical components: coverage, currency, completeness, and corrective action. Coverage focuses on whether all assets are accounted for and actively managed. Tanium enables endpoints to autonomously discover neighboring assets without relying on a centralized scanning point. This distributed approach speeds up scanning, reduces network load, and reaches parts of the network that traditional scanners might miss. It also allows organizations to identify manageable assets that are not yet under control and bring them under management.
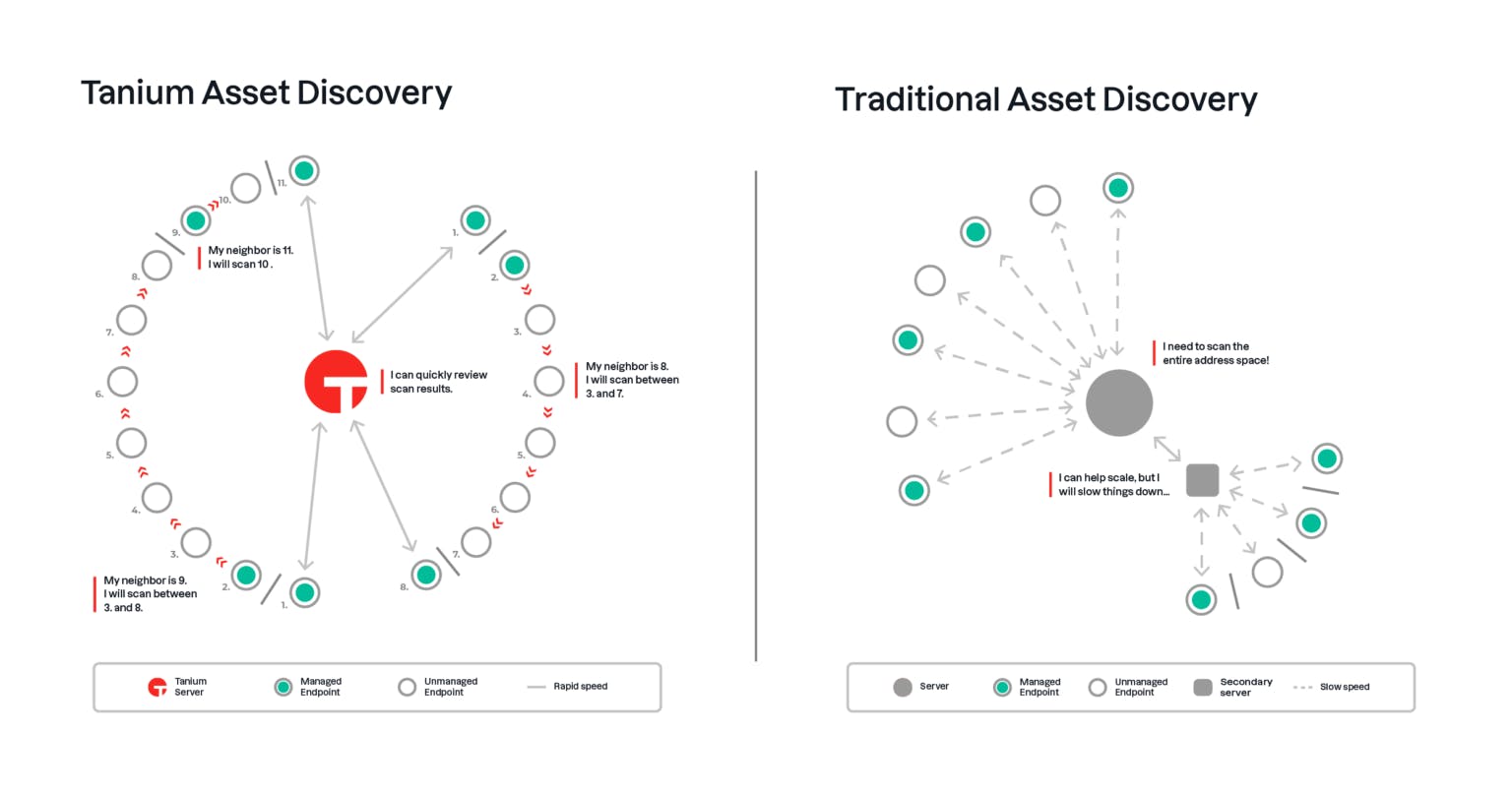
Source: Tanium
If previously managed devices fall out of compliance, they can be quickly flagged for investigation and remediation.
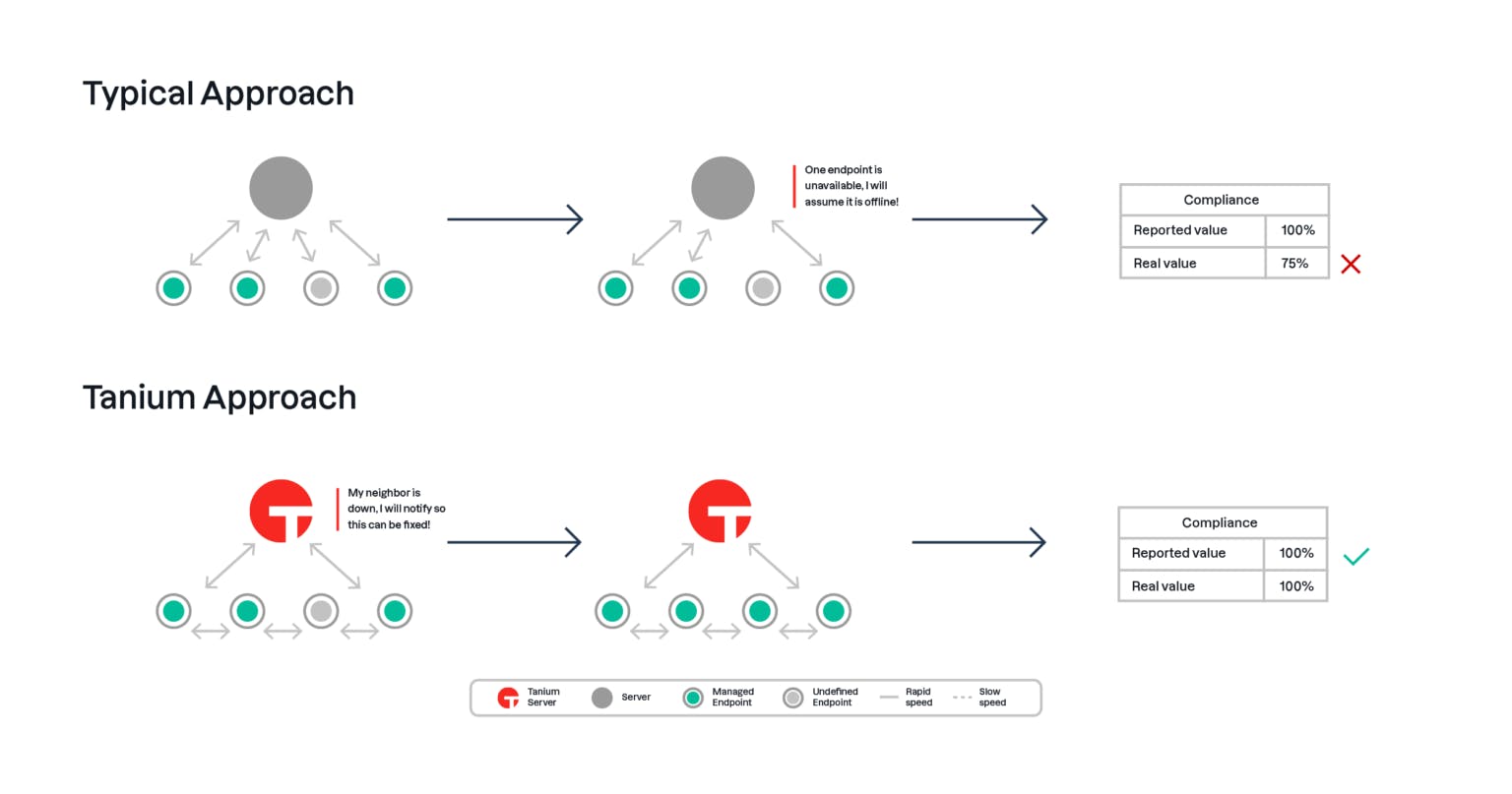
Source: Tanium
Currency refers to the freshness of the data used in compliance reporting. Tanium addresses this with a patented linear chain architecture, where endpoints communicate with one another directly rather than routing everything through a central server. This peer-to-peer system enables data collection in seconds, reducing communication delays and ensuring timely reporting.
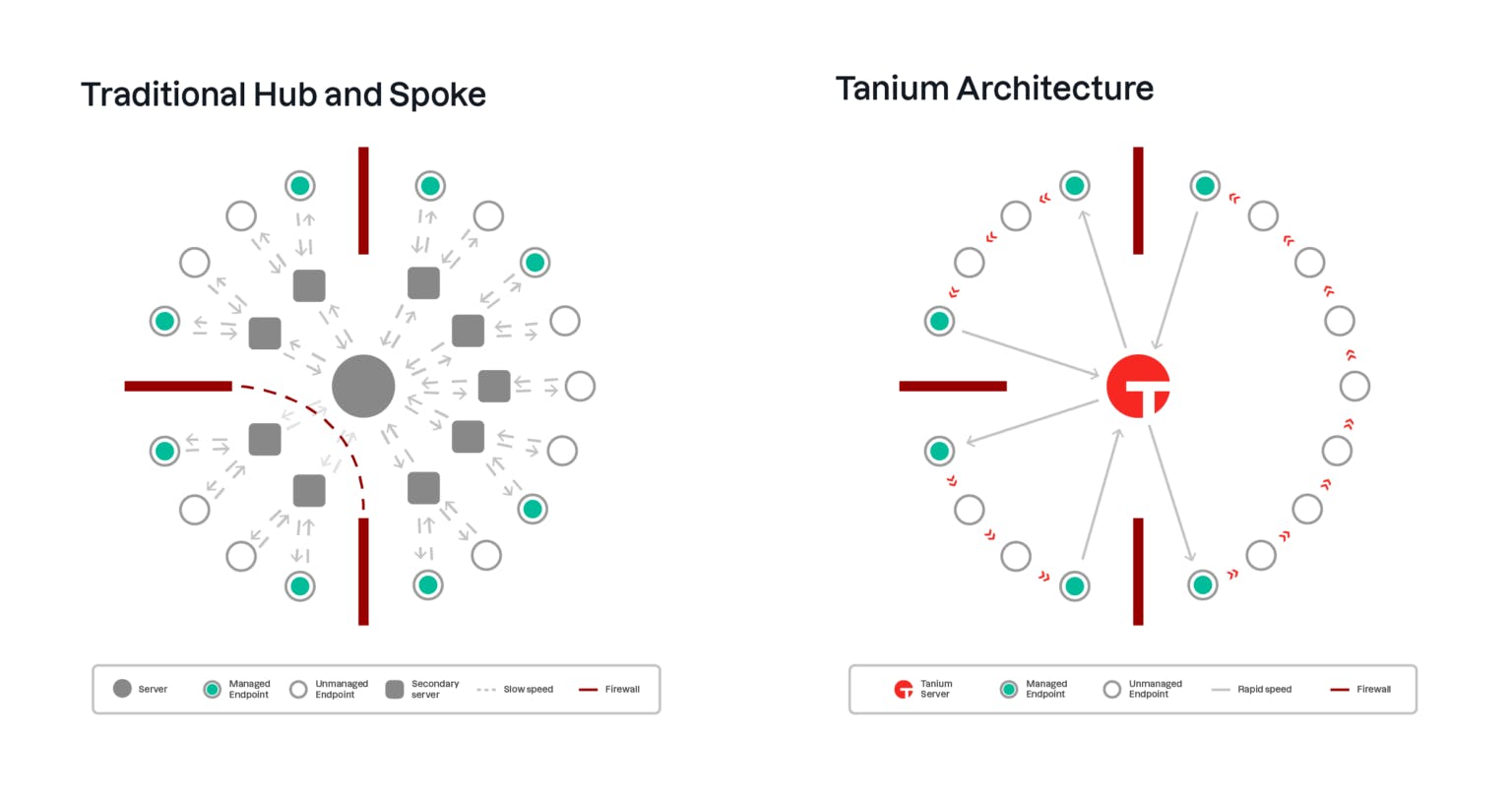
Source: Tanium
Completeness ensures that testing and compliance checks reflect the entire network, not just a portion of it. Tanium accelerates this process by sampling a small number of endpoints and extrapolating results across the network. It compares these findings against central configuration files and logs to verify their accuracy. This method supports real-time visibility across Windows, macOS, and Linux systems, even for remote or segmented endpoints, and works over any type of network connection.
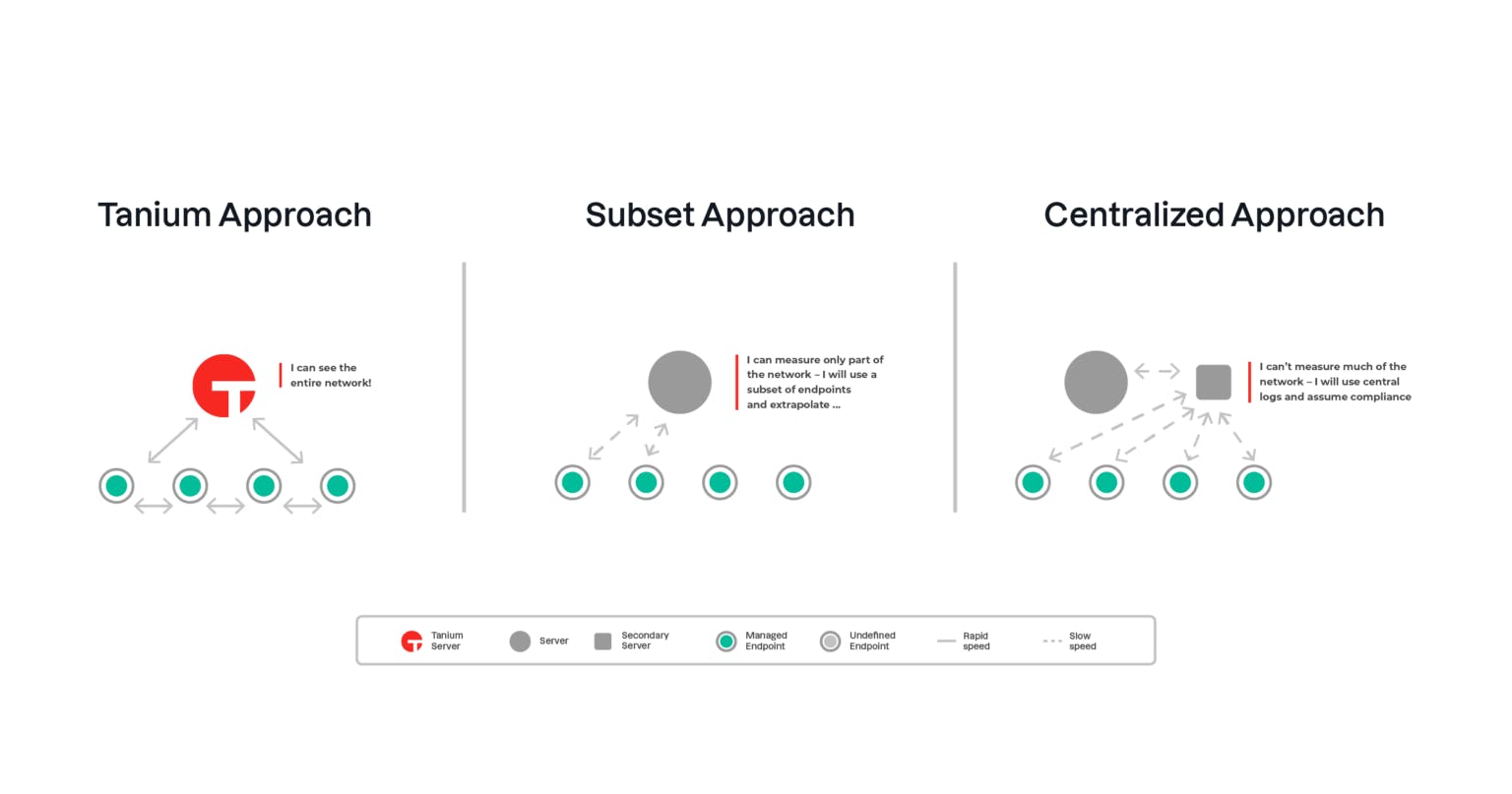
Source: Tanium
Corrective Action is integrated directly into the platform through a concept called “Compliance by Design.” Instead of relying on separate tools or teams for remediation, Tanium uses the same system to detect and fix issues as they arise. Detailed, device-level data highlights specific vulnerabilities, allowing for immediate resolution either natively or through third-party integrations. This tight feedback loop turns compliance and security from a periodic checklist into an ongoing, automated process.
Incident Response
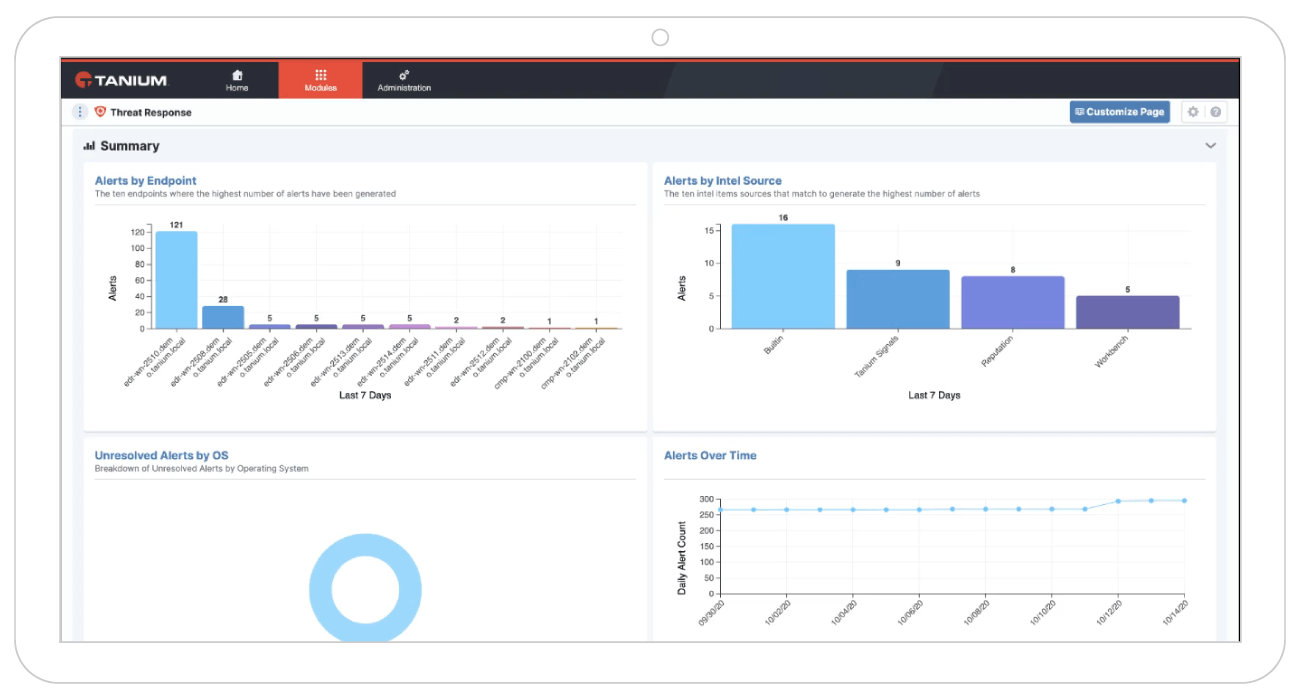
Source: Tanium
Tanium’s Incident Response solution provides real-time monitoring of both online and offline endpoints. Utilizing Tanium Signals, it delivers immediate alerts upon detecting anomalies, allowing for swift investigation. Users can also define custom detection rules to tailor monitoring to specific organizational needs.
Security teams can conduct remote forensic analyses on endpoints, accessing both current and historical data. This functionality enables comprehensive incident scoping and supports actions such as quarantining affected machines, terminating malicious processes, and collecting pertinent files for further examination (shown in image below).
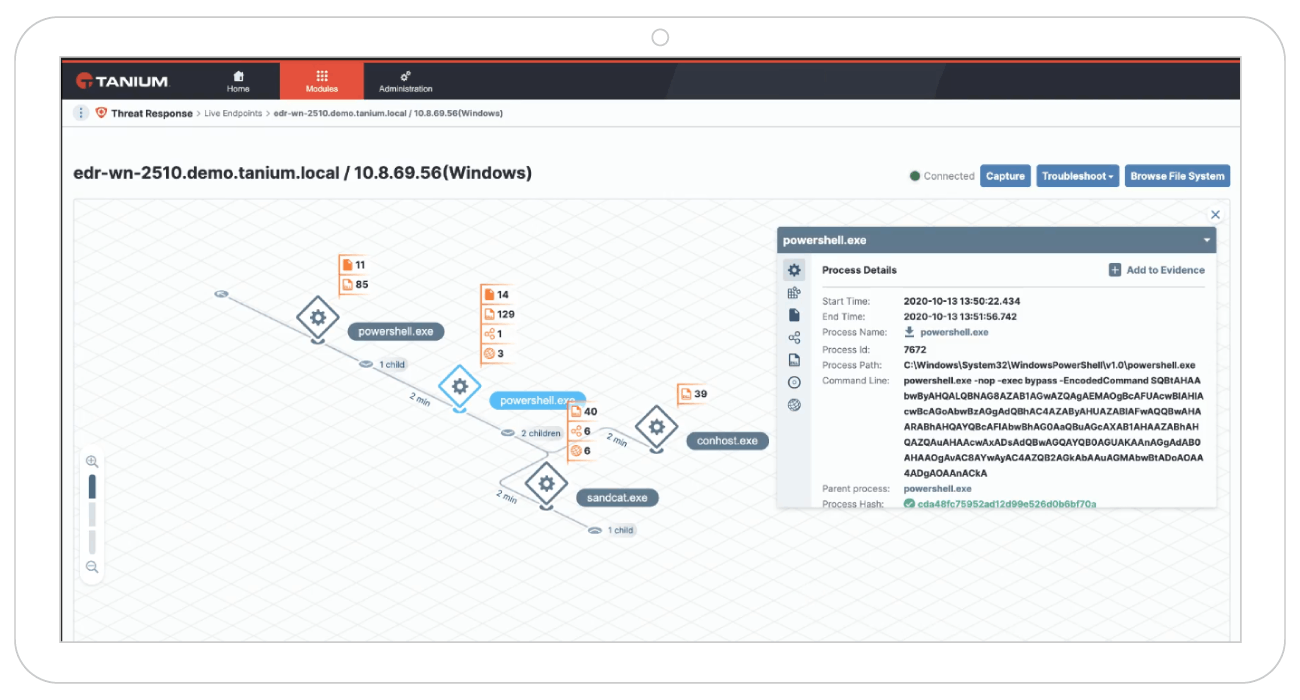
Source: Tanium
Tanium's Endpoint Reactions feature allows for automated responses to detected threats, including isolating compromised endpoints, terminating harmful processes, and deleting malicious files. These reactions can operate independently of central systems, ensuring prompt action even if endpoints are offline.
The platform supports the integration of various threat intelligence feeds through standards like STIX and TAXII, as well as proprietary formats. This flexibility enables organizations to enhance their detection and response strategies with diverse and up-to-date threat information.
Market
Customer
Tanium targets large companies, especially Fortune 500 and Global 2000, that typically fall in the categories of federal agencies, state and local government, education, energy/oil/gas, financial services, healthcare, manufacturing, retail, and technology.
Federal Agencies: Federal agencies are constantly under threat from cyberattacks. The status quo is typically data being stored with different tools across different teams, which is both time-consuming and leads to gaps in compliance. Current systems also don’t provide real-time command, so federal agencies can’t see their degree of vulnerability. Additionally, without fast, coordinated incident response across all endpoints, federal agencies risk disruptions to mission-critical systems and essential public services. Tanium works towards securing and managing federal endpoints. This allows visibility of endpoints and cloud workloads in real-time at any scale, rapid action over all endpoints and cloud workloads regardless of their state, and responding in real-time with a unified platform for IT operations and security workflows.
State & Local Governments: State and local governments currently face a significant amount of IT complexity, including legacy systems, budgetary constraints, security concerns, and the need for modernization. This complexity can be reduced with Tanium’s solution of a singular platform to manage all endpoints, which is meant to provide visibility, control, and protection of every endpoint. The singular platform allows governments to better focus on reducing risk, automating tedious processes, optimizing costs, and focusing on their key priorities.
Education: In 2024, 82% of K-12 schools reported a cyber incident/attack. Cuts to federal spending for education under the Trump administration are predicted to make schools more vulnerable to attempted attacks to steal student data. Tanium provides endpoint visibility, control, and remediation that allows schools to keep track of their IT devices under a single platform and enables teams to investigate and respond to threats in real-time.
Energy, Oil, & Gas: In 2024, US utilities saw a 70% increase in cyberattacks compared to the previous year. Cyberattacks are particularly targeted toward the oil and gas industry because of the increasing reliance on digital technologies and growing geopolitical tensions worldwide. Tanium is meant to help oil and gas companies see and fix cybersecurity issues in real-time, reducing the risk of outages or safety problems. It brings together data from across all systems, even in remote sites, so teams can work together easily and quickly stop threats before they cause damage.
Financial Services: In 2023, ransomware attacks in the financial services industry increased by 64%. Financial institutions’ dependence on digital platforms poses a risk of cyber attackers attempting to steal sensitive customer data. Financial institutions face challenges in meeting strict regulatory requirements like PCI DSS and GLBA, which demand exhaustive data protection measures. Tanium addresses these challenges by providing real-time visibility and control over all endpoints within an organization's IT environment. This enables financial services firms to swiftly detect and remediate vulnerabilities, ensuring compliance with regulatory standards and maintaining the trust of their clients.
Healthcare: In 2023, ransomware attacks on the US healthcare sector increased by 128%. There were 258 total incidents reported across healthcare organizations in 2023, compared to 113 in 2022. These attacks put sensitive patient data at risk and cause operational disruptions and financial losses. Healthcare organizations must meet strict regulatory requirements like HIPAA, which requires thorough data protection measures. Tanium provides real-time visibility and control over all endpoints within an organization's IT environment. This enables healthcare providers to swiftly detect and remediate vulnerabilities, supporting compliance with regulatory standards and helping maintain the trust of their patients.
Manufacturing: In 2023, the manufacturing sector faced a significant increase in cyber threats. Around 5.5K successful ransomware attacks were reported, making it the most targeted industry worldwide. This surge is attributed to the sector's rapid adoption of Industry 4.0 technologies, such as Industrial Internet of Things (IIoT) devices and interconnected supply chains. Tanium provides manufacturers with real-time visibility and control over their IT and operational technology (OT) assets. Its unified platform allows swift detection and remediation of vulnerabilities across distributed environments, helping to minimize downtime and protect critical production systems from cyber threats.
Retail: In 2023, 69% of retail companies experienced ransomware attacks and 71% of those attacks resulted in data encryption (a threat to operations and customer trust). Retailers are particularly vulnerable because they store large volumes of sensitive customer payment and loyalty data, often operate on outdated POS and inventory systems, and must secure a wide range of endpoints across in-store devices, e-commerce platforms, and supply chain networks. Tanium follows a closed feedback loop called “Compliance by Design,” using the same system to detect issues, identify affected endpoints, and apply fixes. It provides detailed endpoint data to support targeted remediation, streamlining security and compliance workflows.
Technology: In 2023, the technology sector saw a 30% increase in cyberattacks compared to the previous year. This can be attributed to the rapid adoption of AI/Generative AI technologies, which often integrate with third-party APIs and cloud services, expanding the attack surface and introducing risks like prompt injection, data leakage, and model manipulation. Additionally, the sector faces challenges such as a persistent cybersecurity skills gap and the complexities of managing hybrid work environments. Tanium provides technology companies with real-time visibility and control over their IT assets through its Converged Endpoint Management (XEM) platform. This platform enables organizations to swiftly detect and remediate vulnerabilities, manage risk, and ensure the security of their digital infrastructure.
Market Size
US Federal Agencies
The US federal government includes a wide range of components, each with its own cybersecurity needs. Defense agencies like the Department of Defense and its sub-agencies, civilian agencies such as the Department of Health and Human Services and the Department of the Treasury, and intelligence agencies including the CIA and NSA all manage sensitive data and critical infrastructure. Independent agencies like the EPA and NASA also require strong cybersecurity systems to protect operational networks and research environments.
Over 2 million full-time employees worked for the federal government as of 2023, many of whom use devices connected to agency networks. These endpoints contribute to a large and complex IT environment that must be continuously monitored and secured to prevent breaches and ensure compliance.
There are around 440 departments, agencies, and sub-agencies across the federal landscape as of 2025, each a potential customer for cybersecurity platforms that can offer endpoint visibility, threat detection, and automated remediation. These organizations often face strict compliance standards and operate in high-risk threat environments.
The global federal cybersecurity market was valued at approximately $18 billion in 2023 and is projected to reach $30 billion by 2032, growing at a CAGR of 6.1%. This growth is driven by digital modernization efforts of legal systems, compliance mandates such as the Federal Information Security Modernization Act (FISMA), and the need to defend against increasingly advanced cyber threats, including those from nation-state actors.
US State & Local Governments
The US state and local government landscape is vast and highly fragmented, creating a large and varied cybersecurity market. At the state level, there are 50 independent governments, each with its own departments and agencies handling services like public health, transportation, and law enforcement. Local governments are even more numerous and diverse, including counties, municipalities, townships, school districts, and special-purpose districts. As of 2022, there were 90.8K local government entities in total. This includes 3K county governments, 19.5K municipal governments, 16.2K township governments, 12.8K independent school districts, and 39.1K special district governments.
These government entities collectively employ a substantial workforce. As of April 2025, state and local governments employed approximately 20.6 million people, with local governments making up roughly three-quarters of that total. Many of these employees rely on IT-connected devices in their daily work, contributing to an expansive and complex network of endpoints that require effective cybersecurity oversight.
From a customer perspective, there are 50 state governments and over 90K local governments—each a potential user of endpoint security platforms like Tanium. These organizations are increasingly investing in cybersecurity infrastructure to protect their networks and data, especially as digital operations grow more central to public services.
The addressable market for cybersecurity across all levels of government—federal, state, and local—is projected to reach $356.7 billion by 2030. This market is expected to grow at a compound annual growth rate (CAGR) of 14% between 2024 and 2030. Several key factors are driving this growth. State and local agencies are undergoing digital transformation, replacing outdated systems with modern, cloud-based solutions. Regulatory compliance requirements, such as those outlined in the Federal Information Security Modernization Act (FISMA), are also increasing security expectations. In parallel, the rise of sophisticated cyber threats, often backed by nation-state actors, is forcing state and local governments to adopt more advanced cybersecurity tools and platforms to protect sensitive data and maintain public trust.
Education
The education sector represents a large and globally distributed cybersecurity market. As of 2024, there are approximately 5 million K–12 schools worldwide, along with around 50K universities operating across various countries. These institutions manage vast networks of devices and users, often with limited IT resources and growing cybersecurity demands.
Source: Market Research Intellect
The number of users connected to education networks is substantial. Globally, around 254 million students are enrolled in universities. In the United States alone, 54.2 million students were enrolled in K–12 schools as of 2021. These figures do not account for faculty, administrative staff, and IT personnel, all of whom also contribute to the digital footprint and increase the number of endpoints requiring management and protection.
From a customer standpoint, the sector includes roughly 5 million K–12 institutions and 50K higher education institutions globally. Each of these represents a potential customer for endpoint management platforms like Tanium, especially as schools and universities look to improve their cybersecurity posture in response to modern threats.
The TAM for the education cybersecurity sector is estimated at $3 billion in 2024 and is expected to reach $6.5 billion by 2033, growing at a CAGR of 9% from 2025 to 2033. Several factors contribute to this growth. Educational institutions are undergoing digital transformation, upgrading legacy systems and expanding online learning infrastructure. Compliance with data privacy regulations, such as the Family Educational Rights and Privacy Act (FERPA), is becoming more critical. In addition, educational institutions face increasing threats from cyberattacks aimed at stealing student records, disrupting learning environments, and targeting under-resourced IT systems. These trends are driving demand for scalable, real-time cybersecurity solutions tailored to the needs of the education sector.
Energy, Oil, & Gas
The oil and gas industry is divided into three main segments: upstream, midstream, and downstream. The upstream segment focuses on exploration and production (E&P) of crude oil and natural gas. This includes locating underground or underwater reserves, drilling exploratory wells, and operating extraction facilities. Midstream operations handle the transportation, storage, and wholesale marketing of crude and refined products, relying on infrastructure like pipelines, tankers, and storage hubs. The downstream segment involves refining crude oil, processing and purifying natural gas, and distributing end products such as fuels, lubricants, and petrochemicals to consumers.
In 2024, the US oil and gas industry itself employed approximately 2 million professionals, marking a net increase of 10.6K jobs compared to 2023. When accounting for direct, indirect, and induced employment, the industry supported over 22.6 million jobs nationwide. Employment spanned across various areas, such as gasoline stations with convenience stores (886K workers), support activities for oil and gas operations (218K workers), oil and gas pipeline and related structures construction (142.7K workers), and natural gas distribution (116.4K workers). Texas led the nation with 480.4K oil and gas jobs, accounting for 23% of the national total.
The customer base for cybersecurity solutions in this industry includes a mix of large, mid-sized, and small operators. Major integrated oil companies such as Saudi Aramco, ExxonMobil, BP, Shell, and Chevron operate across upstream, midstream, and downstream sectors. National Oil Companies (NOCs), including Gazprom (Russia), PetroChina (China), and Petrobras (Brazil), are state-owned entities with large-scale operations. Independent operators typically focus on a specific segment or regional market. Looking at the US specifically in 2024, there were 43.3K businesses engaged in oil drilling and gas extraction, a 5% decrease from 2023. Additionally, the broader U.S. oil and gas industry encompassed 165.1K businesses in 2024. Texas had the highest concentration with 23.5K businesses, followed by California (9.4K), Florida (7.6K), Georgia (6.4K), and New York (5.7K).
Financial Services
The global financial services industry is made up of several components. These include lending and payments, covering personal loans, business loans, mortgage services, credit and debit cards, mobile payments, and digital wallets. Insurance and reinsurance services provide coverage across life, health, property, and casualty sectors. Investments include asset management, wealth management, mutual funds, and pension funds. Foreign exchange services involve currency exchange, remittances, and related services. Financial data services support the broader sector by providing institutions and investors with essential financial data and analytics.
In terms of potential users, in 2023, the US alone had around 3.8 million individuals employed in financial service activities, reflecting around a 1% increase from the previous year. Canada also experienced growth, with 707.5K individuals employed in the sector, marking a 0.3% rise. Other countries, such as the Netherlands and Estonia, saw employment increases of 1.4% and 9.7%, respectively.
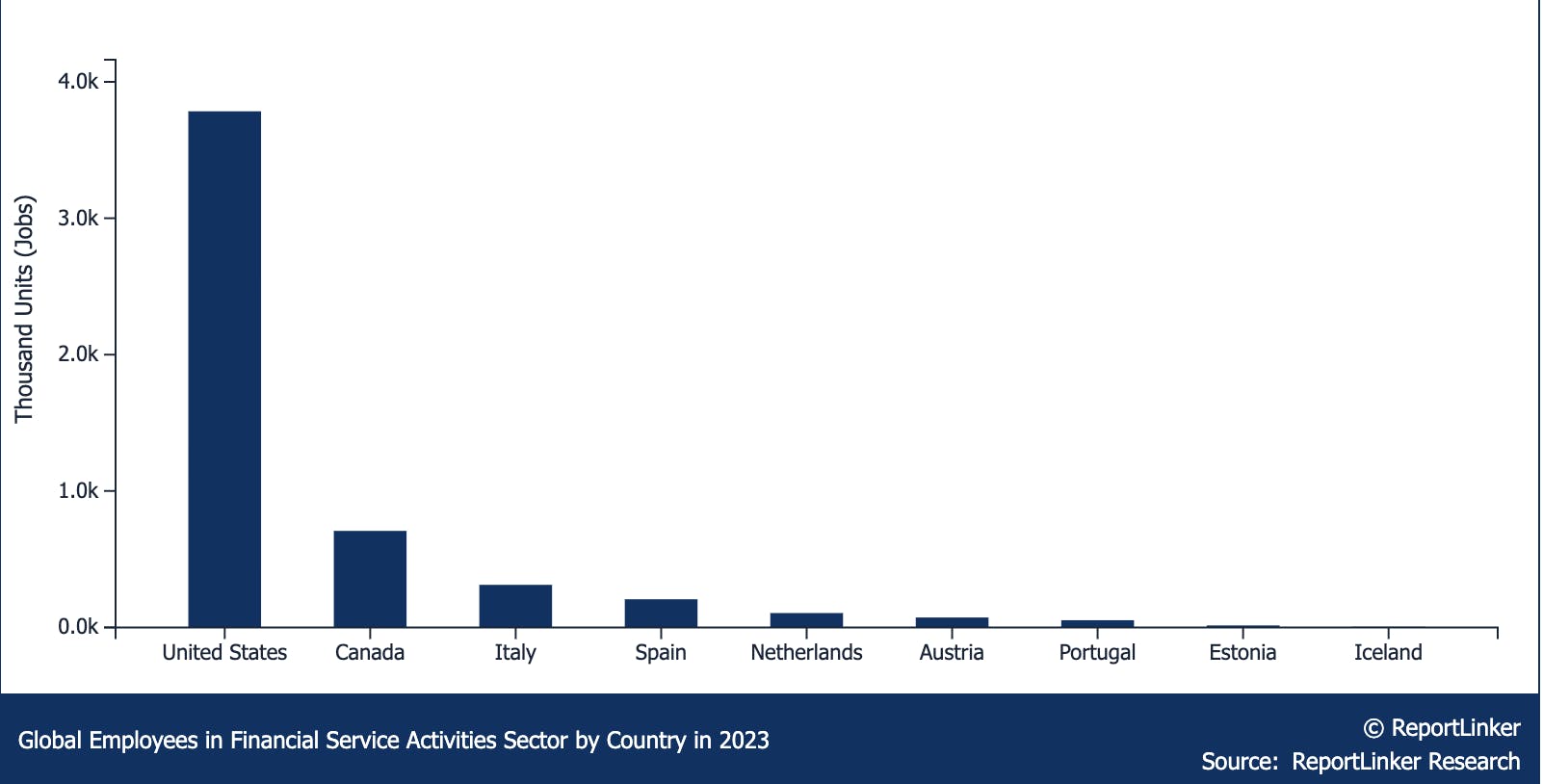
Source: ReportLinker
The number of organizations that can benefit from Tanium’s cybersecurity platform is equally broad. As of 2024, there were approximately 10.1K commercial banking businesses operating worldwide. The fintech sector has seen significant growth, with around 30K fintech startups globally as of 2025. Family offices, which manage the wealth of high-net-worth individuals, number around 15K family offices worldwide, managing approximately $5.9 trillion in assets. Insurance companies also represent a significant segment, with the top 25 insurance companies holding a majority of assets. Additionally, investment firms such as BlackRock, Vanguard Group, and Fidelity Investments manage trillions of dollars on behalf of clients worldwide.
The global financial services cybersecurity market was valued at around $29.7 billion in 2024. It is expected to grow to $28.8 billion in 2025 (CAGR of 13%), and is forecasted to expand to $60.3 billion, maintaining a CAGR of 12.6%.
As the financial sector increases the adoption of technology, there is an increased need for cybersecurity solutions. This growth is driven by factors such as increasing demand for fast and real-time fund transfers, the rise in adoption of blockchain technology in the banking sector, and the growing use of digital banking services.
Healthcare
The healthcare sector is composed of several interconnected components that span care delivery, technology, insurance, and life sciences. Healthcare providers and services include hospitals, clinics, nursing homes, and home healthcare organizations. Medical equipment and supplies manufacturers produce essential tools such as diagnostic devices and surgical instruments. The pharmaceuticals and biotechnology segment covers companies involved in drug development, production, and distribution. Healthcare technology encompasses systems like electronic health records (EHRs), telemedicine platforms, and health information systems. Health insurance providers offer coverage for medical expenses, while life sciences tools and services support research, analytics, and clinical trials.
The potential user base for cybersecurity solutions in healthcare is substantial. As of 2020, the global health workforce comprised approximately 65.1 million health workers, including dentists, medical doctors, midwives, nurses, pharmacists, and other health professionals. This represented a 27% increase from 2013. However, a projected shortfall of 10 million health workers is anticipated by 2030, primarily in low- and lower-middle-income countries. Despite the anticipated gap, healthcare systems worldwide remain highly digitized, creating a large number of connected endpoints requiring protection.
In the US, the customer landscape includes a wide range of healthcare organizations. As of 2024, there are around 6K hospitals across the country. Beyond hospitals, there are around 238.7K healthcare establishments, including clinics, nursing homes, and specialized facilities. Of these, 3.5K are community hospitals that operate as part of larger health systems. Federally Qualified Health Centers (FQHCs) alone serve 32.5 million patients annually, representing roughly 1 in 10 individuals nationwide.
The global healthcare industry is rapidly transforming digitally, which is driving a significant increase in cybersecurity needs. The adoption of electronic health records (EHRs), telemedicine platforms, remote patient monitoring, and AI-powered diagnostics has expanded the digital attack surface across healthcare systems. Growing investment in healthcare IoT (Internet of Medical Things) and cloud-based infrastructure further increases exposure to cyber threats. As digital healthcare expands, so does the need for robust, real-time cybersecurity platforms like Tanium to protect sensitive patient data and ensure system-wide security.
Manufacturing
As of April 2025, the US manufacturing sector employed approximately 12.8 million individuals. Each employee potentially interacts with various IT systems, including enterprise resource planning (ERP) platforms, manufacturing execution systems (MES), and other digital tools essential for modern manufacturing operations. In 2023, the manufacturing industry in the United States accounted for 10.7% of the total national output, employing 8.4% of the workforce. Extrapolating from this, the global manufacturing workforce likely comprises hundreds of millions of employees, each contributing to and relying on complex IT networks.
From a customer standpoint, the manufacturing sector represents a vast market for cybersecurity solutions. As of 2024, the global manufacturing sector comprises approximately 5.5 million enterprises, with projections indicating growth to 6.1 million enterprises by 2029, reflecting a CAGR of 2.2%. These enterprises range from small and medium-sized businesses to large multinational corporations, all of which require robust cybersecurity solutions to protect their operations.
The global industrial cybersecurity market was valued at approximately $26.7 billion in 2025 and is projected to reach $56.9 billion in 2034 (growing at a CAGR of 8.8%). This growth is being driven by rapid digital transformation and increased technology investment. In 2024, 98% of manufacturers have initiated digital transformation efforts, up from 78% in 2019. Manufacturers allocated 30% of their operating budgets to technology investments in 2024, compared to 23% in 2023, focusing on cloud computing, artificial intelligence, and 5G technologies. These shifts increase both operational efficiency and the risk of cyber threats, underscoring the need for real-time endpoint management and cybersecurity platforms like Tanium.
Retail
The global retail industry includes a wide variety of business types that cater to consumer needs through different formats and channels. Key components of the sector include convenience stores offering quick-access essentials, specialty stores with focused product expertise, and department stores that carry a broad range of goods under one roof. Supermarkets and hypermarkets combine food with general merchandise, while discount stores focus on low-cost, no-frills shopping. The sector also includes multichannel retailers operating across physical and digital platforms, grocery stores focused on food and daily staples, and clothing stores selling apparel and accessories. Other segments include auto retailers, home furnishing retailers, drug stores, and businesses engaged in direct sales, catalogs, and mail orders. Ecommerce businesses, which are online-only, have also become a dominant force in global retail.
In the United States alone, the retail sector employed approximately 18 million individuals as of 2025. These employees interact daily with digital systems including point-of-sale terminals, inventory management software, customer databases, and cloud-based platforms, each representing a potential entry point for cyber threats.
The global retail cybersecurity market was valued at approximately $11.6 billion in 2023. This growth is driven by the increasing digitization of retail operations and the corresponding need to protect against cyber threats.
As retailers adopt technologies like AI, IoT, and cloud computing to enhance customer experiences and streamline operations, they inadvertently expand their digital attack surfaces. This increased digital footprint makes them more susceptible to cyber threats such as phishing attacks, malware infiltration, and data breaches. For instance, phishing attacks accounted for 43% of all cyberattacks in the retail sector in 2023, up from 35% in 2022. The average cost of a data breach in the retail industry reached $4.9 million. Nearly 24% of all cyberattacks in 2020 targeted retailers, highlighting the sector's vulnerability and the critical need for comprehensive security solutions.
Technology
The global tech industry is made up of a wide range of specialized sectors, each contributing to innovation and digital transformation across the economy. Key components include ecommerce, which covers online shopping platforms; Internet Software & Services, such as business productivity tools; and FinTech, which delivers digital financial services. Other segments include HealthTech, focused on tech-enabled healthcare solutions; EdTech, which offers digital learning tools; and GreenTech, aimed at environmentally sustainable innovations. Additional areas include BioTech and CleanTech, which focus on medical research and renewable energy technologies, respectively. Emerging fields like MarineTech, related to ocean exploration, and Artificial Intelligence (AI), which powers automation and intelligent systems, are also integral parts of the broader tech ecosystem.
Potential customers for platforms like Tanium span the estimated 7.2 million companies, with China hosting the largest number at over 3.7 million, followed by the United States with approximately 459.9K companies. These organizations vary in size from small startups to multinational enterprises, all with increasing reliance on connected devices, distributed teams, and cloud-based systems.
Competition
Competitive Landscape
Key competitors vary by functional area:
Detection & Response: CrowdStrike, SentinelOne, Microsoft Defender, Trend Micro, Sophos, Symantec, Palo Alto (Cortex XDR), Cisco (Secure Endpoint), Carbon Black
Unified Endpoint Management: Microsoft (Intune), VMware (Workspace ONE), IBM MaaS360, ManageEngine, Ivanti, Sophos (via Intercept X + MDM)
Risk & Compliance Management: Qualys, Palo Alto Networks (Prisma), Tenable, Rapid7, BigFix (HCL), Symantec (for DLP), Trend Micro (for compliance visibility)
Asset Discovery & Inventory: Axonius, ServiceNow, Lansweeper, Microsoft (Defender + Intune CMDB), Cisco (via SecureX integrations)
The endpoint security market includes a mix of established players and fast-growing startups; Companies like Microsoft, IBM, and VMware represent long-standing service providers, while newer entrants such as CrowdStrike and SentinelOne are rapidly gaining traction with innovative approaches. The competitive landscape is moderately fragmented, with different companies leading specific subsegments.
Competitors
Detection & Response
CrowdStrike: CrowdStrike was founded in 2011 by George Kurtz, Dmitri Alperovitch, and Gregg Marston. It offers a cloud-native cybersecurity platform called Falcon, which provides endpoint protection, threat intelligence, and cyberattack response services. CrowdStrike uses a cloud-native architecture with lightweight agents that continuously stream telemetry to a centralized platform. This setup enables real-time detection, behavioral analysis, and cross-organization correlation using AI and threat intelligence. It is effective for identifying emerging threats across large datasets and delivering rapid, automated responses based on global threat signals. In contrast, Tanium focuses on localized, real-time detection and response at enterprise scale. Tanium keeps data on-premises and allows for distributed, on-demand queries, enabling instant investigations, targeted response actions, and full visibility even in offline or regulated environments.
SentinelOne: SentinelOne was founded in 2013 by Tomer Weingarten. It provides an AI-powered cybersecurity platform that offers autonomous endpoint protection, detection, and response across various devices and cloud workloads. SentinelOne’s Singularity platform uses autonomous AI-powered agents that detect, contain, and remediate threats directly on the endpoint, often without human input. It supports features like automated rollback and emphasizes speed and automation. This approach is ideal for organizations seeking simplicity and operational efficiency with minimal analyst involvement. Meanwhile, Tanium, although also agent-based, prioritizes analyst-driven workflows. It enables real-time investigations, command issuance, and targeted remediation, providing deep endpoint visibility and control for interactive threat hunting.
Unified Endpoint Management
Microsoft: Microsoft Intune was launched by Microsoft in 2011. It is a cloud-native unified endpoint management (UEM) solution deeply integrated with the Microsoft ecosystem, including Azure AD and Microsoft 365. Intune is designed primarily for mobile device management (MDM) and mobile application management (MAM) across platforms such as Windows, Android, iOS, and macOS. It excels in policy-based management, zero-touch provisioning through Autopilot, and compliance enforcement, particularly within organizations standardized on Microsoft tools.
In comparison, while Intune emphasizes automated provisioning and policy enforcement within a Microsoft-centric environment, Tanium focuses on enabling operational teams to take granular, real-time actions across their endpoints. For example, Tanium allows users to identify a missing patch and deploy it instantly without waiting for policy refreshes. This makes Tanium more suitable for large, complex environments, such as in the military, finance, or healthcare, where speed and control are critical.
VMware: VMware Workspace ONE was launched in 2016 by VMware. The platform is a digital workspace solution with robust UEM capabilities inherited from AirWatch. It offers cross-platform endpoint management, application lifecycle management, and conditional access controls for both mobile and desktop devices. Workspace ONE is particularly optimized for virtual desktop infrastructure (VDI) and BYOD (Bring Your Own Device) scenarios, making it well-suited for enterprises that prioritize employee choice programs and access federation. VMware was acquired by Broadcom in May 2022 for $69 billion.
When comparing the two, Workspace ONE excels in user-centric use cases like application delivery, user access, and unified workspace experiences, especially in mobile or VDI-heavy environments. On the other hand, Tanium is reportedly better suited for security-sensitive, operations-heavy environments where administrators need full visibility and command-line precision to query, investigate, and resolve issues across tens of thousands of endpoints within seconds.
Risk & Compliance Management
Palo Alto Networks: Palo Alto Networks was founded in 2005 by Nir Zuk, Rajiv Batra, and Yu Ming Mao. The company provides cloud-native risk and compliance solutions through platforms like Prisma Cloud, which is designed for Cloud Security Posture Management (CSPM), and Cortex Xpanse, which supports attack surface management. These tools help organizations maintain continuous compliance in multi-cloud environments by identifying misconfigurations, monitoring risk exposure, and aligning with over 75 compliance frameworks, including CIS, PCI-DSS, NIST, and HIPAA.
In comparison, Palo Alto Networks focuses on agentless, cloud-native monitoring of infrastructure, particularly around misconfiguration detection and CSPM in cloud and container environments. It is optimized for DevOps and cloud security teams looking to align infrastructure with regulatory frameworks via automated scans and remediation. On the other hand, Tanium focuses on on-premise and endpoint-level compliance. It delivers real-time configuration auditing, patch status tracking, vulnerability correlation, and enforcement of security benchmarks like CIS across laptops, servers, and hybrid environments. Tanium’s strength reportedly lies in deep endpoint visibility, instant querying, and closed-loop remediation; capabilities that Prisma does not extend to the endpoint level.
Qualys: Qualys was founded in 1999 by Gilles Samoun and Philippe Langlois. The company offers a cloud-based platform for vulnerability management (VMDR), policy compliance, and web application security. It is known for both agent-based and agentless scanning, supporting ongoing compliance monitoring and reporting for frameworks such as PCI, HIPAA, and ISO 27001. When comparing the two, Tanium offers real-time visibility and remediation across all endpoints, while Qualys depends on scheduled scans that can miss important changes between scan intervals. Unlike Qualys, which often needs additional tool integration, Tanium provides a unified platform for vulnerability management, compliance, and endpoint control. It relies on a single, consistent data source to power analytics and incident response workflows, resulting in better decision-making. Moreover, Tanium’s peer-to-peer architecture ensures fast coverage of both online and offline devices, even in distributed or remote environments.
Asset Discovery & Inventory
ServiceNow: ServiceNow Discovery was founded in 2004 by Fred Luddy. It automates the identification of IT infrastructure components, such as servers, applications, and network devices, and populates the Configuration Management Database (CMDB) with accurate, up-to-date information. The platform provides visibility across on-premises, cloud, and hybrid environments, allowing organizations to manage their IT assets effectively. In comparison, ServiceNow maintains a detailed CMDB by discovering and mapping IT assets and their interdependencies. It uses probes and sensors to detect devices and applications, updating the CMDB accordingly. Meanwhile, Tanium delivers real-time, continuous visibility into endpoints, including unmanaged devices, without relying solely on scheduled scans. Its distributed architecture enables rapid data collection and action at scale. Additionally, Tanium integrates with ServiceNow to enhance CMDB accuracy and timeliness by feeding it real-time endpoint data.
Cisco: Cisco Spaces was launched by Cisco in 2018. It offers a cloud-based asset-tracking solution that uses existing Cisco network infrastructure to deliver real-time visibility into the location and status of physical assets within indoor environments. This platform is especially valuable in industries such as healthcare, manufacturing, and education, where tracking high-value equipment is essential. In terms of comparison, Cisco Spaces specializes in tracking the physical location of assets using Wi-Fi and BLE technologies, offering spatial analytics and real-time location services. In contrast, Tanium focuses on the logical and operational dimensions of asset management, providing granular data on device configurations, software inventory, and compliance status. When integrated, Cisco Spaces and Tanium complement each other, combining physical location data with operational and security insights to create a more holistic asset management solution.
Competitive Differentiation
Tanium differentiates itself through its single-agent architecture, which contrasts with many competitors that require multiple agents and dashboards. This unified design allows Tanium to scale across large, complex enterprise environments. By consolidating essential functions such as patch management, compliance, threat detection, and asset inventory into one platform, Tanium significantly reduces operational overhead, licensing costs, and integration burdens.
Tanium also benefits from strong defensibility and switching moats. It is deployed in some of the most demanding and complex IT environments in the world, including US federal agencies like the Department of Defense and large Fortune 500 enterprises. These customers operate under strict compliance mandates, manage massive numbers of endpoints, and rely on deeply customized security stacks. Once integrated, replacing Tanium would involve a lengthy re-architecture process, re-certification, and introduce significant operational risk, creating high friction for vendor switching.
Additionally, Tanium consolidates multiple endpoint and IT operations tools into a single platform. Without it, enterprises typically require three to five separate tools to match Tanium’s functionality. This results in more vendors, more agents on each endpoint, and greater complexity in managing updates and integrations. Moving away from Tanium would mean giving up centralized control and efficiency, rebuilding internal workflows, and introducing unnecessary overhead, all of which reinforce the strength of Tanium’s long-term customer retention.
Platform Architecture & Scalability
Tanium employs a linear-chain communication model, where each endpoint communicates with its immediate neighbors. This design minimizes network traffic and enables rapid data collection and command execution across large-scale environments.
The platform is engineered to scale efficiently, supporting environments with millions of endpoints without requiring significant infrastructure expansion. This scalability is achieved through its distributed architecture, which reduces the need for additional servers or network bandwidth.
Tanium's architecture allows for near real-time visibility and control over endpoints. Security and IT operations teams can query endpoint data and execute actions within seconds, facilitating prompt decision-making and response.
The platform's design reduces the need for extensive infrastructure. Its efficient communication model and endpoint processing capabilities lessen the burden on central servers, leading to lower total cost of ownership and simplified deployment in complex network environments.
Integrations & Extensibility
Tanium has established a technology partner program alongside a dedicated developer portal. This initiative offers partners structured support and guidance for building integrations, including access to API documentation, examples, and the Tanium software necessary for developing and testing integrations.
The platform provides an API Gateway, serving as a single and stable integration point. This gateway is explicitly designed to facilitate the development of partner integrations, enabling the creation of solutions that leverage Tanium's flexible agent and scalable architecture.
Tanium offers a Developer Community Forum where partners can seek assistance and support from Tanium integration engineers. This community resource is intended to aid in the development and troubleshooting of integrations.
The technology partner program is tiered, providing varying levels of support and benefits. Higher-tier partners receive additional advantages, such as assigned integration engineers, support for enabling sales, and opportunities to showcase integrations at Tanium's annual user conference.
Business Model
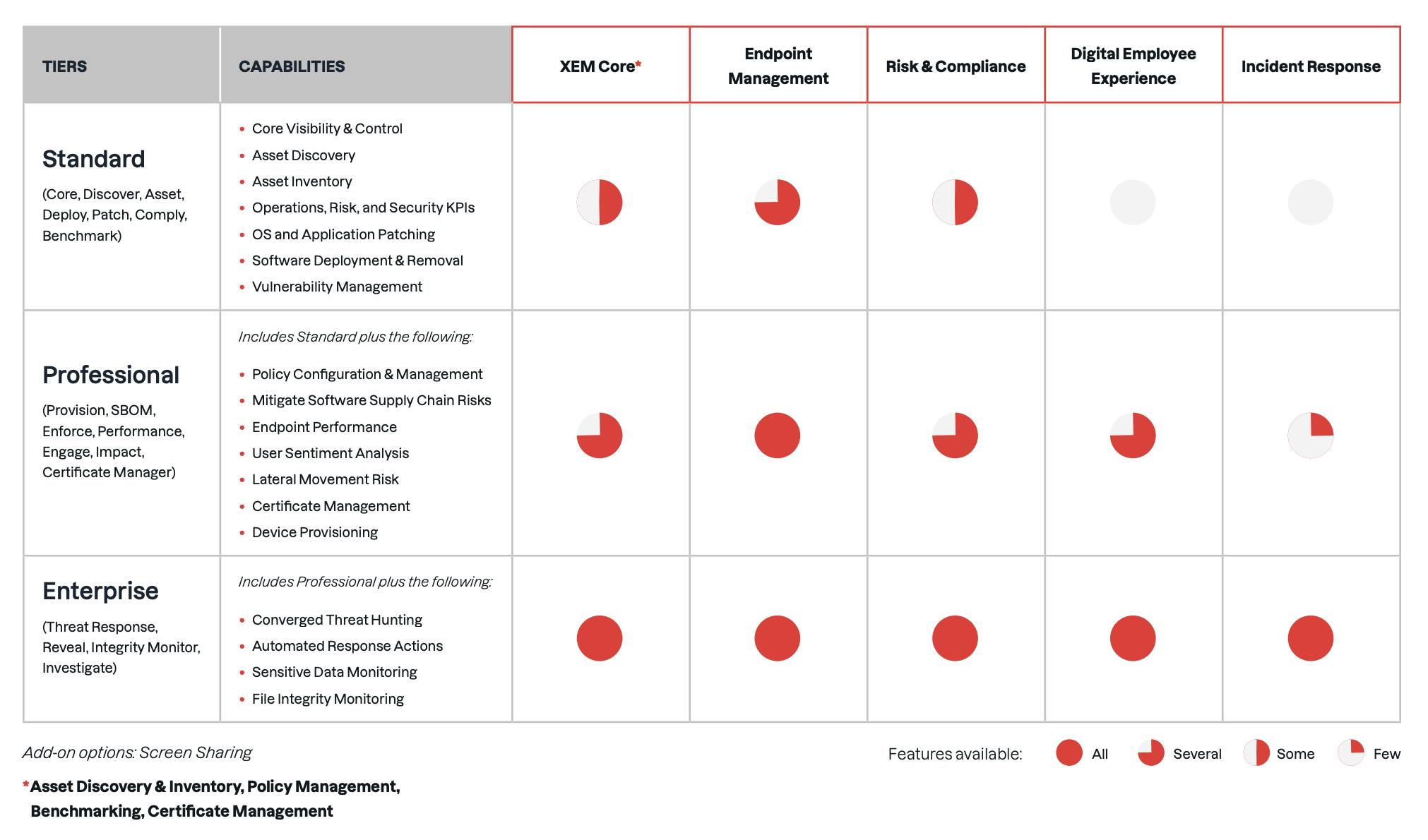
Source: Tanium
Tanium offers its cybersecurity and IT operations solutions through tiered service packages designed to match the needs and maturity levels of organizations. The Standard Tier includes foundational capabilities such as asset discovery, inventory, patch management, software deployment, and basic risk and compliance tools. The Professional Tier builds on this by adding features like policy configuration, endpoint performance monitoring, user sentiment analysis, and certificate management. The Enterprise Tier provides the full suite, incorporating everything from the lower tiers along with advanced tools for digital employee experience monitoring and incident response capabilities.
In addition to these service tiers, Tanium’s platform is modular, and each module can be licensed individually; typically with a minimum purchase requirement of 2K endpoints. Example per-endpoint annual pricing from third-party sources includes the Tanium Core Platform at approximately $24.30, Tanium Patch at $7.30, Tanium Threat Response at $19, and Tanium Enforce at $6.50 per endpoint per year.
Cloud-based pricing also varies by module and license type. Publicly listed prices from vendor sources include Tanium Patch (v.2) at $9 per license, Tanium Core Platform at $30, Tanium Subscription Suite at $34, and Tanium Client Management at $37 per license.
On the AWS Marketplace, Tanium modules are available under various contract lengths, with 12-month pricing examples including Asset Inventory at $36 per endpoint, Client Management at $42 per endpoint, Sensitive Data Monitor at $36 per endpoint, Risk and Compliance at $42 per endpoint, and Threat Hunting at $42 per endpoint. These modular pricing models and tiered offerings provide organizations with flexibility in scaling Tanium’s capabilities to fit their specific security and operational needs.
Traction
In 2024, Tanium achieved $700 million in revenue, up from $440.2 million in 2019, with 11.8% year-over-year revenue growth. The company has built a global presence of 2.5K customers globally, including more than 40% of the Fortune 100, seven of the top 10 US retailers, and nine of the top 10 US commercial banks as of 2024.
Tanium’s platform secures more than 33 million endpoints worldwide, delivering real-time visibility and control across complex IT environments. A key driver of its global reach has been its broad partner ecosystem, which includes Independent Software Vendors (ISVs), Global and Regional System Integrators, Value-Added Resellers (VARs), Managed Services Providers (MSPs), and Consulting Firms. Notable partners include Microsoft, ServiceNow, PwC, and Kyndryl, which have contributed to Tanium's growth in various regions.
One 2024 impact study of the Tanium XEM platform revealed over a 200% return on investment over a three-year period. Key areas of value included software savings where organizations were able to reclaim unused, rarely used, or unauthorized software across 90% of endpoints, resulting in over $4.8 million in savings. Operational efficiency improved by 60% through automation of software deployment, patching, and security assessments, leading to more than $1 million in cost savings.
In addition, Tanium helped customers reduce software vulnerabilities by 97% through automated patching and real-time risk assessments, avoiding $7.9 million in potential security-related costs. Tool consolidation also delivered significant results, with a 70% reduction in endpoint and security tools, producing $4.1 million in cost savings. These outcomes highlight Tanium’s value in enhancing security, streamlining IT operations, and driving tangible financial results for enterprise clients.
Valuation
Tanium has raised over $1 billion in total funding as of June 2025. The company raised a $150 million Series F at a valuation of $9 billion in January 2021 with Ontario Teachers' Pension Plan as the lead investor. Other notable investors previously include Andreessen Horowitz, Salesforce Ventures, TPG Growth, and Wellington Management. As of June 2025, Tanium’s valuation in secondary markets was estimated at $4 billion.
Key Opportunities
Founder Vision
Orion Hindawi identifies two major areas of expansion for Tanium moving forward.
The first is expanding into the mid-market and SMB segments. As of June 2025, Tanium primarily targets large enterprises, especially those in the Fortune 500 and Global 2000. However, cybersecurity needs among mid-market and small businesses are increasing rapidly, as cyberattacks are increasingly shifting downstream. In fact, SMB cybersecurity spending is projected to reach $109 billion by 2026. This presents a clear opportunity for Tanium. The company’s core platform does not require a full rebuild and can be tailored to meet the unique requirements of smaller organizations. A major advantage is Tanium’s single-agent, linear-scaling architecture, which is inherently flexible and well-suited to varying organizational sizes. Additionally, increased remote work and widespread SaaS adoption among SMBs create a strong demand for solutions that offer unified endpoint visibility and security with minimal overhead.
The second area of focus is accessing adjacent markets. There is a growing trend where organizations increasingly demand a unified source of real-time endpoint data and control to support compliance efforts, drive automation, and enable cloud migration. Tanium is already functioning as both a data plane, offering live asset inventory and telemetry, and a control plane that can manage patching, configuration, and compliance. This dual role positions Tanium to evolve into a “system of record” for all devices, enabling new workflows across compliance, IT service management (ITSM), and cloud operations.
According to Hindawi, many organizations want to migrate to the cloud but are stalled by compliance uncertainty. As he explains, "they don't know what to move, how, or to whom.” Tanium already provides trusted data to address these challenges, but to fully capture the opportunity, it must build an ecosystem of partners such as Salesforce, major cloud providers, and compliance platforms in order to deliver end-to-end solutions for domain-specific problems. It has the potential to serve as the connective tissue between siloed enterprise systems.
Looking ahead, the ability to formalize partner integrations, including with ServiceNow and Salesforce, and co-develop solutions focused on compliance and cloud migration could allow Tanium to monetize use cases far beyond traditional endpoint security. This expansion is further supported by external factors such as growing compliance pressure (e.g., GDPR, CCPA, SEC rules), increasing hybrid cloud complexity, and CIO-driven mandates for automation. Together, these forces create powerful tailwinds for platforms that offer both unified data and control.
Data-Driven Automation
Leveraging AI-driven automation presents a major opportunity for Tanium as the cybersecurity landscape evolves. The global market for AI in cybersecurity was valued at $25.4 billion in 2024 and is projected to grow at a CAGR of 24.4%, reaching approximately $93.8 billion by 2030. Tanium is uniquely positioned in this space due to its ability to provide live, trustworthy, and complete endpoint data, which is an essential foundation for training accurate and effective AI models.
This rich dataset gives Tanium a significant edge in enabling AI use cases like predictive risk scoring, intelligent patching, and automated remediation. The transformation potential grows even further when combining Tanium’s data with open APIs and partner AI models, allowing for the automation of high-value workflows such as incident response, asset rationalization, and software compliance. Independent market dynamics also favor this shift: rising cybersecurity labor shortages and increased board-level pressure on CISOs are accelerating the need to automate manual, resource-intensive processes.
Capitalizing on the shift to unified platforms is another strategic avenue for growth. As of 2022, 75% of organizations were actively pursuing security vendor consolidation, up significantly from 29% in 2020. Tanium already addresses this need by consolidating multiple capabilities including asset discovery, patch management, endpoint detection and response (EDR), compliance, and risk management into a single agent and unified platform, which delivers immediate benefits in cost and complexity reduction.
Looking forward, positioning Tanium as a platform play rather than just a security tool can help expand its footprint within enterprises. This approach enables multi-department deals and increases average contract value (ACV). External forces like tightening IT budgets, especially after the macroeconomic pressures of 2023, are driving CIOs and CISOs to eliminate redundant vendors. These factors make Tanium’s integrated platform more attractive, supporting its expansion into larger, more strategic enterprise deployments.
Key Risks
Demand Surges
Geopolitical events, technological advancements, and evolving threat landscapes can lead to sudden increases in demand for cybersecurity solutions. While this presents growth opportunities, it also poses risks if Tanium cannot scale its operations swiftly to meet client needs, which would quickly turn a large customer base to competitors. 60% of businesses acknowledge that geopolitical tensions have directly influenced their cybersecurity strategies
For instance, Russia’s invasion of Ukraine three years ago translated to many efforts to destabilize the US. This made many of Tanium’s US customers worried about their cybersecurity coverage. The Tanium team worked hard to provide customers with a more structurally sound cybersecurity and operations position
AI & Quantum Computing Threats
As quantum computing advances, existing cryptographic algorithms (like RSA and ECC) used widely in endpoint authentication and secure communications may become vulnerable. While Tanium’s platform does not rely directly on quantum-sensitive tools, many parts of its extended cybersecurity ecosystem do (e.g., identity management, certificate-based authentication). If Tanium does not proactively integrate post-quantum cryptography (PQC) support or validate its platform against new quantum-resilient standards, it risks falling behind in a rapidly evolving security landscape. 61% of organizations plan to migrate to PQC within five years, but fewer than half have started. 95% of firms lack a quantum-readiness roadmap, indicating widespread industry unpreparedness
Talent Acquisition
The cybersecurity industry faces a significant talent shortage, which can hinder Tanium's growth and innovation. 67% of organizations in a study reported a shortage of cybersecurity professionals, with 58% stating that this shortage puts their organizations at significant risk. 70% of organizations agree that the cybersecurity skills shortage creates additional risks, and 62% of IT decision-makers say that the greatest challenge is finding candidates with specific experience in network engineering and security. Inability to secure top talent may delay product development, reduce service quality, and impact Tanium's ability to respond to emerging threats.
Summary
One 2023 report found that 75% of businesses view security as a growing priority, which is a trend that’s only expected to accelerate as digital reliance deepens. Tanium addresses this need with a unified endpoint management and security platform that gives enterprises real-time visibility and control across their entire network. It enables organizations to manage software and clients, monitor vulnerabilities and compliance, detect threats, respond to incidents, and discover unmanaged devices, all from a single, scalable platform.
By consolidating these functions, Tanium reduces complexity and allows IT and security teams to act quickly and efficiently. The platform is designed for large enterprises, particularly those in the Fortune 500 and Global 2000. Its customer base spans government, education, energy, finance, healthcare, manufacturing, retail, and tech sectors, where strong cybersecurity is becoming increasingly essential alongside rising technology adoption. The opportunity going forward is for the company to demonstrate its ability to address both the long-tail of cybersecurity needs among companies and adapt to the changing threat surface from AI and quantum computing.

