Actionable Summary
Cybersecurity is at the forefront of the technology sector as security continues to become more mission-critical: Multiple CTO survey reports, such as those from Morgan Stanley, Gartner, ETR, Flexiti, and Battery Ventures, all show that security is currently one of the highest priority budget items of technology spend for CTOs. Morgan Stanley’s Q2 AlphaWise survey showed that security is the last budget item that CTOs expect to cut during an economic downturn. 98% of IT and security leaders say they dealt with a cyberattack last year (47 attacks on average).
The pandemic and global conflicts continue to raise security awareness: Cybersecurity is not new, but the past two years have seen increasing risk from cyberattacks. Attacks on core US infrastructures such as the shutdown of the Colonial pipeline, SolarWinds, and Log4j discovery have created a renewed sense of urgency.
Although there has been a slowdown in investment lately, the industry has experienced record deal activity over the past year: Analyzing over 3,500 cybersecurity companies, Momentum Cyber found that cybersecurity e companies recorded more than $77 billion in M&A deals and over $29 billion in private investments in 2021, making it a landmark year. In addition, despite the recent slowdown, the industry has seen over $16.5 billion in financing activity and $111 billion in M&A so far in 2022.
Evolution of cybersecurity from servers to the cloud will drive growth: The industry has evolved and as new applications are built on the public cloud, they will need more security. The IDC estimates that 750 million new cloud-native apps will be created globally by 2025, representing 4x growth.
Information security and risk management spend is continuing to grow: Global spending on information security and risk management is estimated to grow 11% to $188 billion in 2023. This growth for the security market is driven by the increasing sophistication of new attack methods used by hackers, and the need for organizations to continue spending to keep up with the evolving threat landscape.
Cybersecurity will increasingly become woven into other IT processes: Cybersecurity continues to be integrated with multiple aspects of the technology stack. Security has become tied more closely to DevOps, with the evolution of DevSecOps. As other processes, like AI and ML increasingly rely on more data, that presents more security risks.
Cybersecurity: Bigger & More Complex
This report discusses how cybersecurity threats have evolved over the past decade as technology has become increasingly integrated into our everyday lives. It provides an overview of the cybersecurity landscape, its structure, and the key players and trends shaping the sector.
In recent years, the move to the cloud, widespread mobile adoption, remote work, and the increasing number of enterprise software applications have created a feeding frenzy for hackers to infiltrate organizations. There are more access points and greater surface areas for hackers, allowing them to get more and more creative. The financial and reputational damages that companies have experienced from security hacks have also increased.
As threats have grown, an increasing number of cybersecurity companies have emerged to tackle the broader attack surface. This has led to a more complex industry which can be difficult to grasp for tech investors and startups. Our report aims to demystify the sector by breaking it down into subcategories centered around the four fundamental components that enable a business to perform its duties: hardware, software, users, and networking (including on-prem and cloud). Companies generally look for security solutions that meet the needs of each of these four areas.
Cybersecurity Investment Isn’t Going Anywhere
The last two years have seen fervent investor interest across all categories of technology. But unlike some categories which have become overheated, investor interest in cybersecurity may be more deserved given the continued prioritization from executives. For example, independent research firm Flexera’s IT spending survey of 500 IT executives in their 2021 and 2022 Tech Spend Pulse Report shows that cybersecurity is seen as equally important to broader organizational changes, like digital transformation. Digital transformation is considered key to survival for most large enterprises, but with the rise of cyberattacks, businesses have realized the importance of securing the organization to avoid any potentially massive threats.
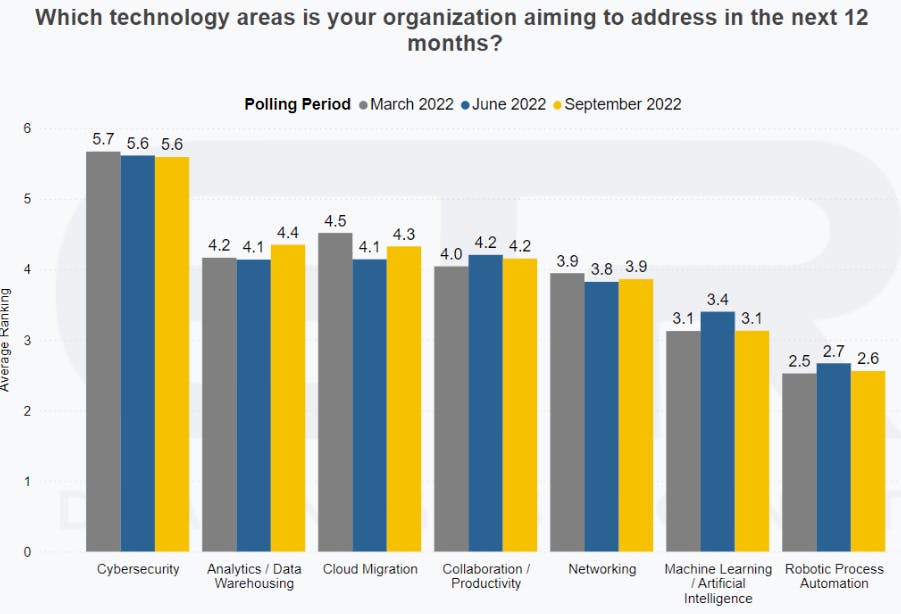
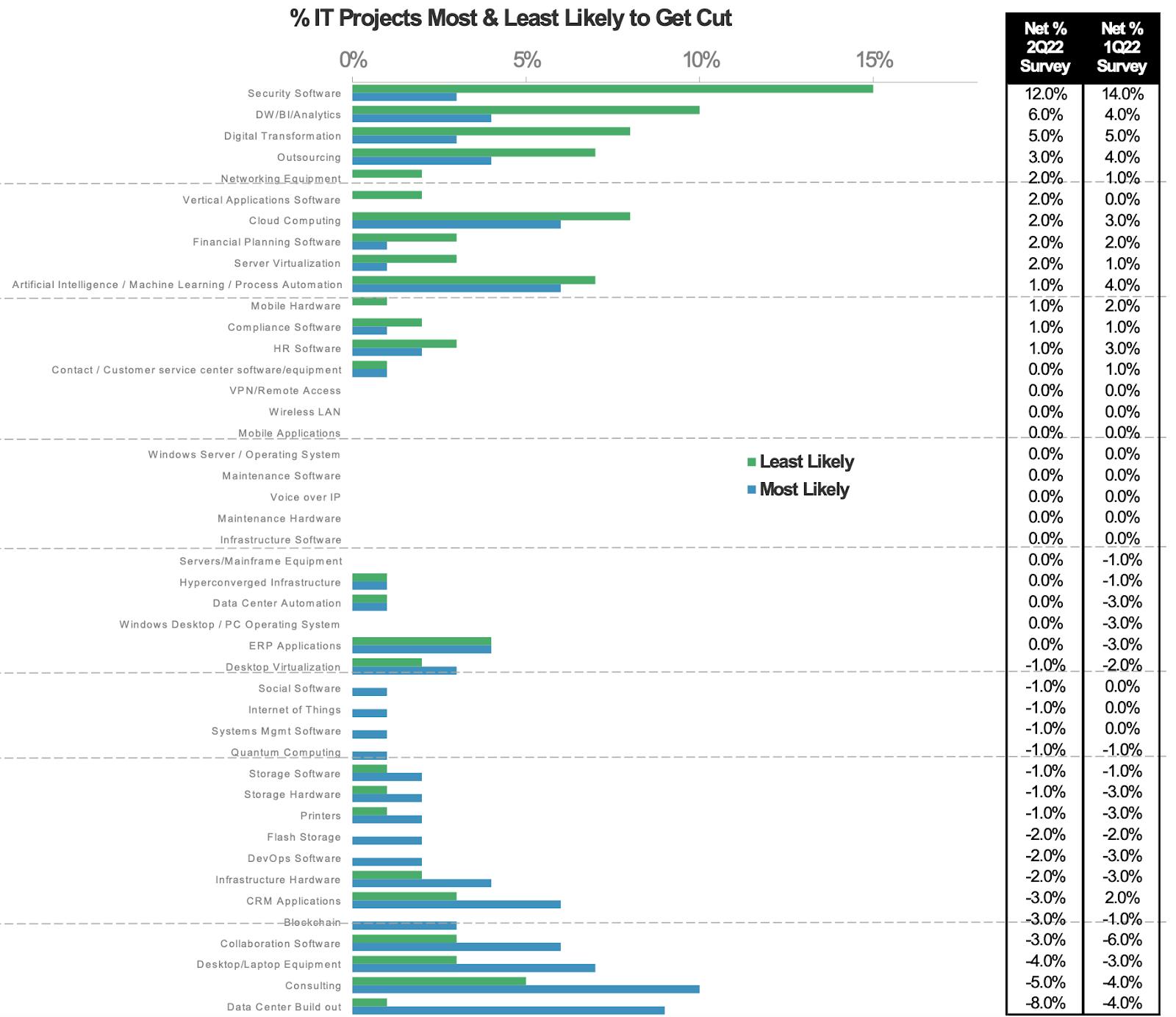
As of October 2022, the Wall Street Journal reported that security was once again at the top of every CIO’s agenda for the 3rd year in a row. In 2022, both Morgan Stanley's AlphaWise CTO Survey, and Gartner, confirmed that 66% of respondents said they planned to increase their investments in cybersecurity. Security software is the least likely IT project to be cut during an economic slowdown, as it is viewed as mission-critical for organizations.
Source: Morgan Stanley’s AlphaWise 2Q22 CIO Survey
ETR’s May 2022 executive survey found that over 1,200 IT leaders, representing roughly $570 billion in annual IT spend, ranked cybersecurity as the sector with the highest spending intent over the next year relative to other key technologies priorities. Cybersecurity remains a top priority for organizations going into an economic slowdown, even ahead of cloud migration initiatives.
Over 31% of survey respondents in Battery Ventures’ report stated that security was their number one priority, while over 92% of respondents expect their security budgets to increase between 2022 and 2023. This near-unanimity stood out even amidst other important enterprise initiatives, such as the 79% of respondents who expected increased budgets for AI/ML tools. Security has become a key pillar in mission-critical enterprise software.
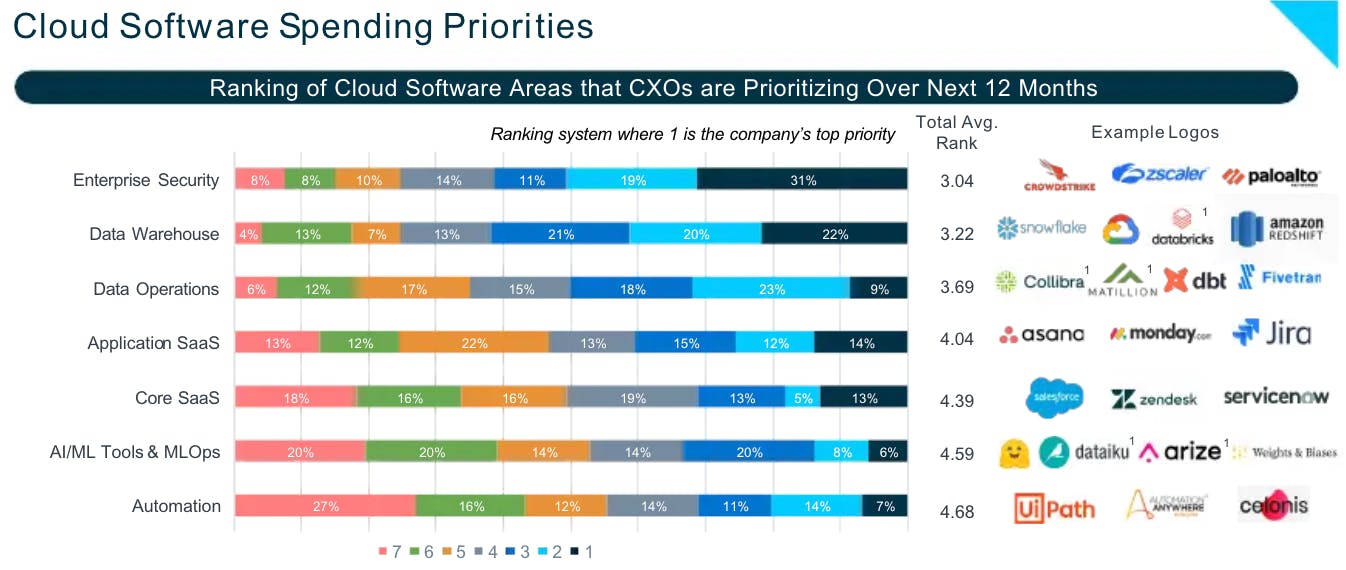
Source: Battery Ventures
While the financial losses from attacks are sizable, there are often even more significant losses including reputational damage, loss of consumer trust, and low employee morale that can cripple an organization. For example, the SolarWinds breach caused both reputational damage and huge financial loss for the company and its customers. Cases like these serve as a wake-up call to other leaders to address security loopholes within their organizations.
Public Sector’s Growing Demand For Cybersecurity
Security is increasingly a high priority, not only for major corporations, but also for the public sector. Governments are taking significant steps to invest in their own cybersecurity infrastructure. In 2019, President Biden signed an executive order to galvanize public and private efforts to help identify, protect, and respond to persistent malicious cyber campaigns. The US government also set it as a top priority for all government agencies to upgrade their infrastructure to be ready to respond to cyber attacks.
US government spending on cybersecurity has increased from $13 billion in 2017 to $18 billion in 2021. In July 2022, the House of Representatives approved a bill for $15.6 billion in cybersecurity funding for the 2023 fiscal year. In September 2022, the House also announced a new $1 billion grant for security projects. Public spending on security solutions continues to grow every year due, in large part, to the increased sophistication and quantity of nation state sponsored attacks, which come amidst rising tensions with Russia and China.
Cybersecurity Funding Has Slowed, but Momentum Persists
Cyber attacks aren’t simply a business problem; they affect corporations, governments, and individuals. These groups can be direct victims of the attack, but also be impacted as secondary victims of the attack as they wreak havoc on the economy at large.
According to Cybersecurity Ventures, cyberattacks could have cost the global economy a total of $6 trillion in 2021, and this number is projected to increase to more than $10.5 trillion by 2025. That’s almost 50% of the US GDP in 2021. If the cumulative economic cost of cyberattacks is seen as an addressable market unto itself, there are few that are bigger.
Although the current downturn in software continues to slow funding for cybersecurity companies, the last two years have seen tremendous heights in cybersecurity funding that will continue to reshape the security industry for many years, with Q4 2021 representing the high-water mark of cybersecurity funding for a single quarter. For example, Lacework's $1.3 billion Series D in November 2021 was the largest funding round in the history of cybersecurity. McAfee was acquired in November 2021 for $14 billion. During the same period, Thoma Bravo completed its run of cybersecurity acquisitions like Proofpoint ($12.3B), Ping Identity ($2.8B), Sailpoint ($6.9B), and Forgerock ($2.3B) representing some of the largest deals in the history of cybersecurity. In addition, SentinelOne’s 2021 IPO became the most highly valued cybersecurity IPOs at a market cap of over $10 billion, nearly doubling the previous mark set by Crowdstrike in 2019.
Amidst the ongoing market correction in 2022, cybersecurity is resilient. Investors continue to be interested in cybersecurity solutions given the enterprise demand and budget. Adding to this is a technology landscape with the rapid emergence of new software paradigms, which also means new channels for hackers to inflict harm.
That is why, in 2021, the total amount of investment into cybersecurity has soared. There were more than 1,000+ financing transactions worth a total of $29 billion in 2021, up from $12 billion in 2020. Similarly, as of September 2022, there has been over $16.5 billion in financing volume in cybersecurity, with 799 financing transactions and over $111 billion in M&A volume with two months to go. These numbers are comparable with 2021, which was a record year, indicating that almost despite the broader downturn in tech, investor interest in cybersecurity isn't slowing down.
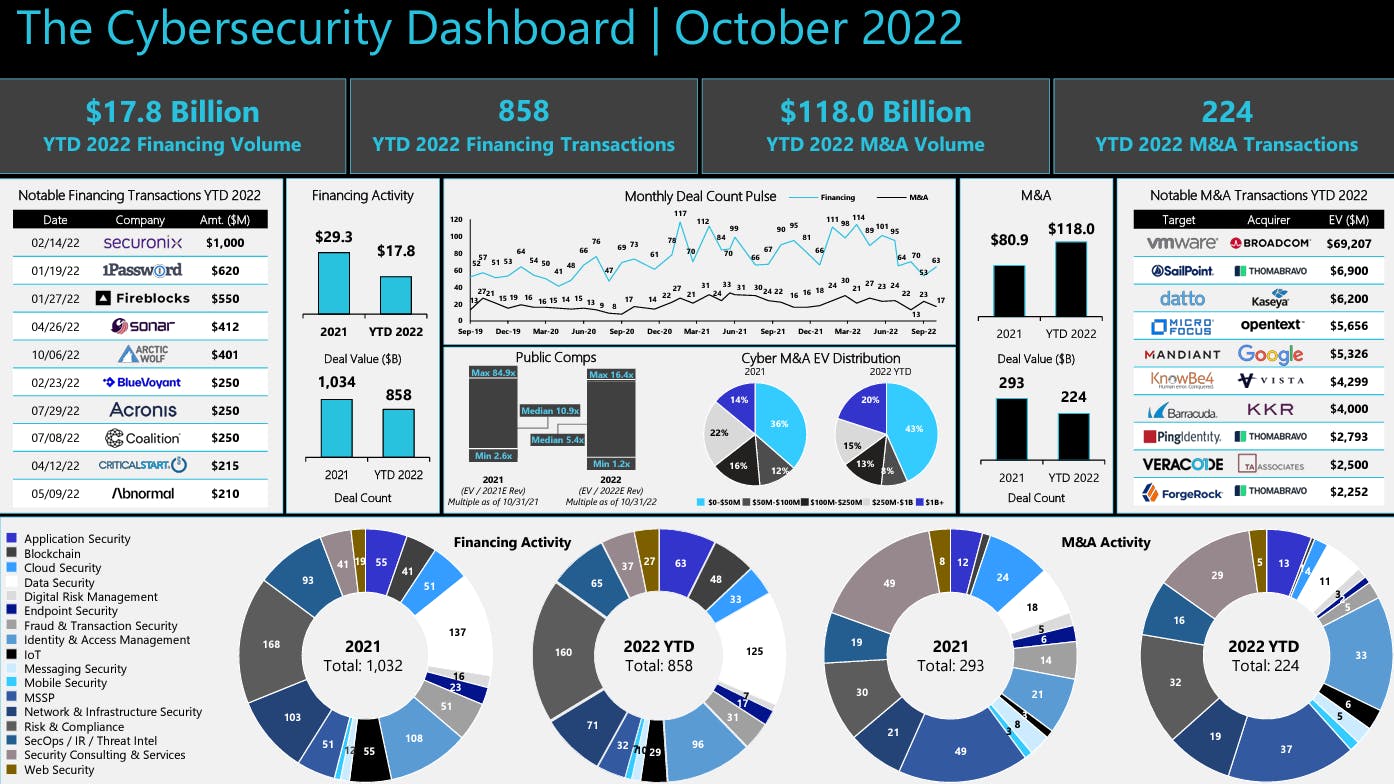
Source: Momentum Cyber
A core reason for the continued velocity of funding in cybersecurity is how quickly the threat landscape is changing. Hackers are constantly developing more sophisticated ways to threaten companies. This situation is exacerbated by the significant lack of skilled security talent available to companies.
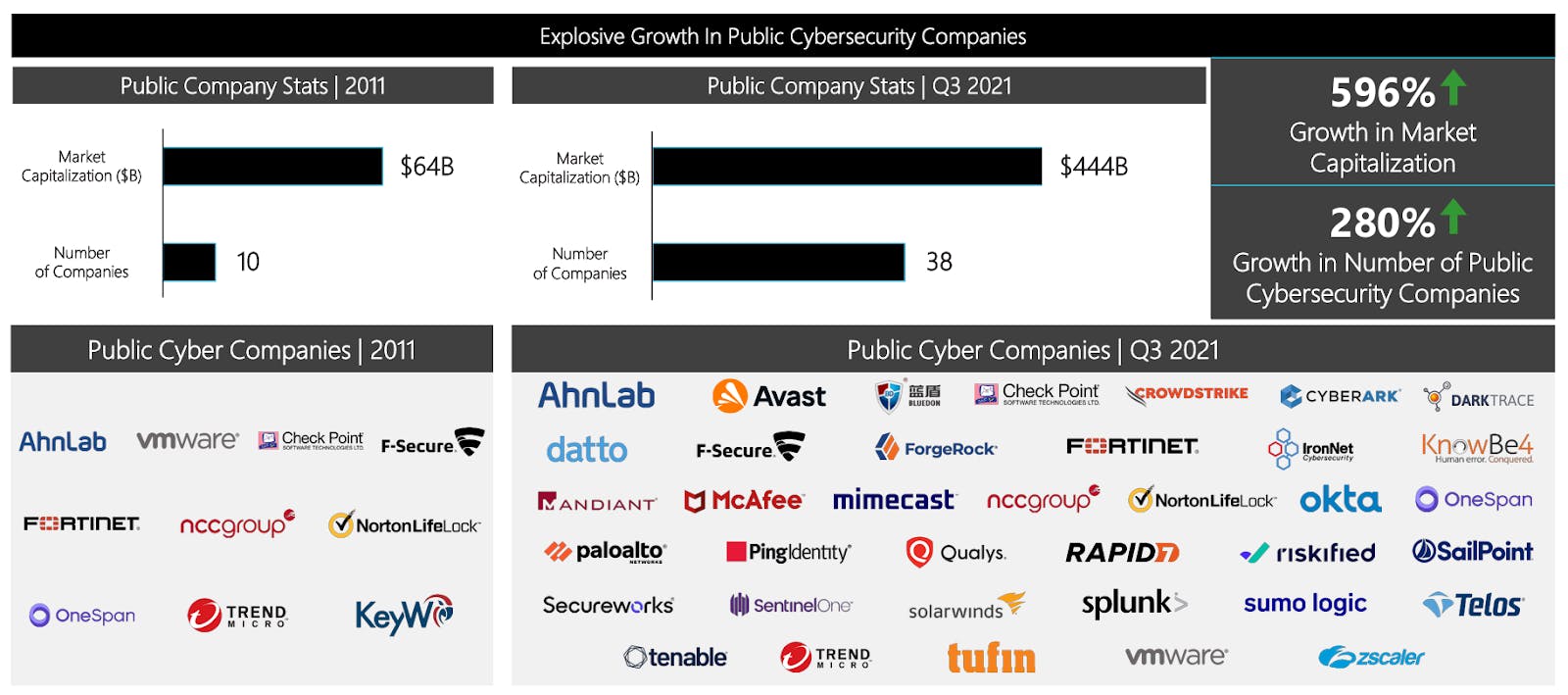
As long as cyberattacks remain prominent, and CTOs continue to prioritize solutions to protect their enterprise, companies will continue to get built in the space to meet that demand. This dynamic has led the number of public cybersecurity companies to grow by over 280% between 2011 and 2022. A consequence of this is industry fragmentation which drives towards vendor consolidation, a topic that will be discussed in more depth later in this report.
The complex web of threat vectors and security responses not only makes cybersecurity a highly fragmented and competitive market, but also a very big area of opportunity. As the market pushes towards consolidation, it’s important to understand the critical players in the security landscape, how they interact with each other, and how the space will continue to evolve.
The Evolution of Cybersecurity
A Brief Early History
Cybersecurity is unlike any other technology vertical because the space is defined by its ability to respond to two constantly evolving forces: the creativity of technologists and the creativity of hackers. As technology has evolved from on-prem servers to cloud-based workloads and everything in between, security has had to evolve right alongside it.
Early engineers experimented with computer worms and DoS to illustrate weaknesses of the internet. In 1989, the first malicious cyber attack was created. Joseph Popp created a Malware attack that he distributed through literally mailing floppy disks to people. The scale of these attacks continued to grow. In the early 2000s, with the rise of personal computers in the wake of Microsoft Windows 98, there was the ILOVEYOU worm that affected millions of computers within just a few hours of release. .
Fast forward to 2010, Stuxnet was a major milestone in malicious computer malware attacks. The program was co-developed by the US and Israeli intelligence services as a means to sabotage Iran's nuclear weapons. Stuxnet was the first cybersecurity incident that grabbed headlines across the world, and marked the entry into a new phase of cyber war capabilities, progressing from simple data theft and information gathering to actual physical destruction.
Today, some of the largest and most common cyber attacks are ransomware attacks. These are some of the most dangerous threats that have the ability to bring down enterprises across all industries. Security executives’ top concerns usually include these types of attacks. Ransomware attackers traditionally access enterprise environments via phishing and other common attack vectors, such as gaps in identity management and zero-day exploits. Once inside, they identify valuable data and delete or encrypt backups. Data is then possibly exfiltrated with malicious code and later used for extortion.
Ransomware attacks have increased over the last decade, largely thanks to the development of Ransomware-as-a-Service (RaaS), a model that uses affiliates to deploy already-developed ransomware software. This has become big business as it allows cyber extortionists to infiltrate an organization’s system and hold its data hostage via encryption. According to Sophos’ Ransomware report, the average ransom paid by mid-sized organizations for their stolen data was $170K. Added to this, the average cost for recovering from a ransomware attack — including downtime, lost people time, device cost, network cost, lost opportunity, and the ransom itself — was $1.85 million. But only 4% of companies that pay the ransom actually retrieve all their stolen data.
There are two paradigm shifts that drove cyber attacks to evolve from hobbyist hacker projects to full-scale enterprise threats: the move from monolithic to distributed systems, and the move from on-prem to the cloud.
From Monolithic To Distributed Systems
The growth in cybercriminal activity has been directly proportional to the evolution of computer networks and workloads. In the early 1900s, most computer systems were hardware such as mainframes that were easier to protect in-house. Punch cards were the norm for how people communicated and transferred information from one machine to another. The company had physical control over their mainframes and servers.
However, this started to change with the launch of AWS in 2006 and the iPhone in 2007. Companies have had to rethink their security landscape to include cloud, smartphones, tablets, WiFi, remote working, and modern IoT devices. As a result, the number of cyberattacks have tripled over the past decade. With more of companies’ data flowing through remote data centers, they no longer have complete control as they did when they relied on physical in-house servers. As the world has become more digital it’s become a hacker's playground, given how much more accessible someone’s sensitive data can be when stored online vs. stored in a physical system.
With the rapid advancements in semiconductors (think Moore’s Law), software has evolved from large monolithic hardware applications to virtual machines. Today, distributed systems are used to create more web applications. As more enterprises and IT teams build and create applications using containers and public cloud infrastructure, the number of vectors and areas that need to be protected has proportionally increased for many enterprise workloads.
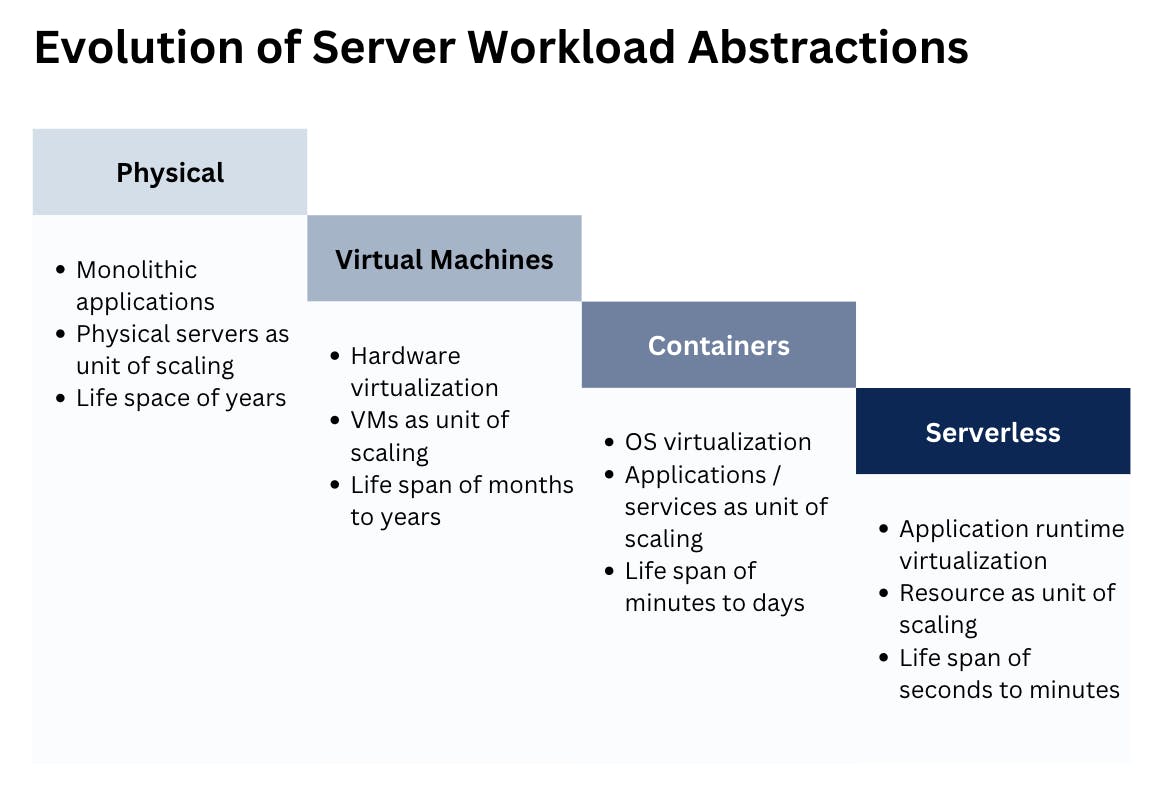
Source: Gartner
On-Prem To Cloud
Another contributing factor to the rise in cyberattacks is the move from on-prem to the public cloud. Although the cloud still remains a small portion of the enterprise market today, the most significant evolution in cybersecurity over the next decade will be the adoption of cloud computing.
Gartner estimates that digital workloads running in the cloud will grow dramatically going from 30% in 2021 to 95% in 2025. More than 85% of organizations will be cloud-first by 2025, by which time all their systems will either be cloud-based third-party applications or internal implementations of cloud solutions. The universal adoption of cloud computing will push cloud security from the cutting edge to the mainstream within the next 5 years. Most cloud breaches occur as a result of cloud misconfigurations, poorly configured cloud buckets, poor security practices, weak cloud security posture, and the widening gap in trained IT security professionals. The pandemic has only made the issue worse, with more distributed teams working from home creating the need for IT security to address unsecured home or public networks.
The Modern IT Enterprise Stack
This brings us to the modern enterprise in 2022. Today’s enterprise is fragmented and complex. The typical cloud data platform involves using 50-100+ software and infrastructure tools. Many of these applications are downloaded and have multiple different vendors, partners, and integrations. This fragmented enterprise network has given rise to a wide range of security solutions tracking specific niches within the enterprise.
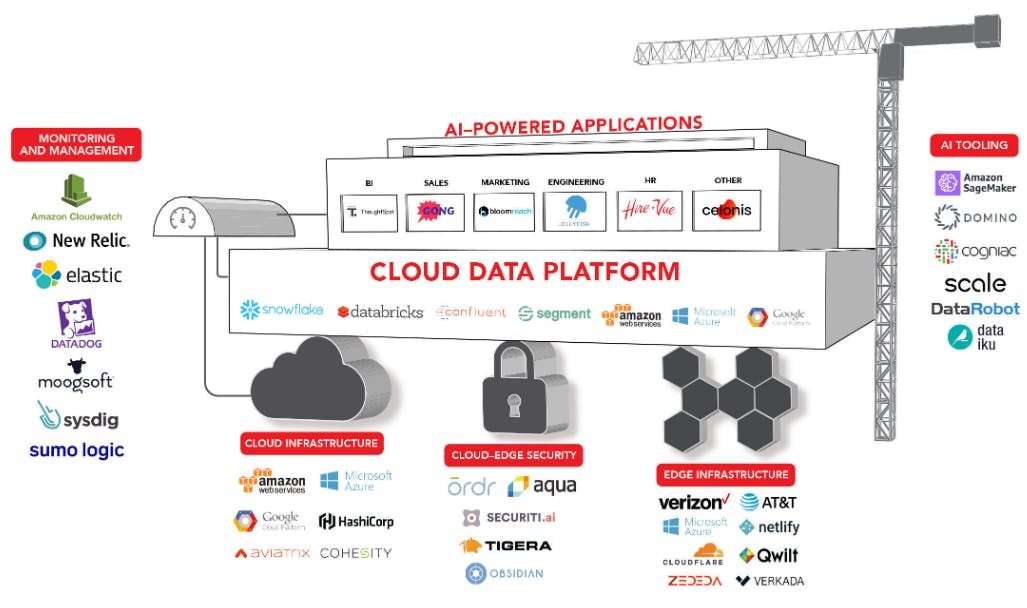
Source: WingVC
Security professionals must deal with the core building blocks of today’s IT infrastructure: hardware, software, networks, cloud computing, and users. Each building block with its associated security layer is addressed below.
Cybersecurity Landscape
If you simplify the modern enterprise into its most basic elements you can better map out the cybersecurity ecosystem. On a high level, the enterprise is made up of devices, infrastructure, networks, applications, identities and data.
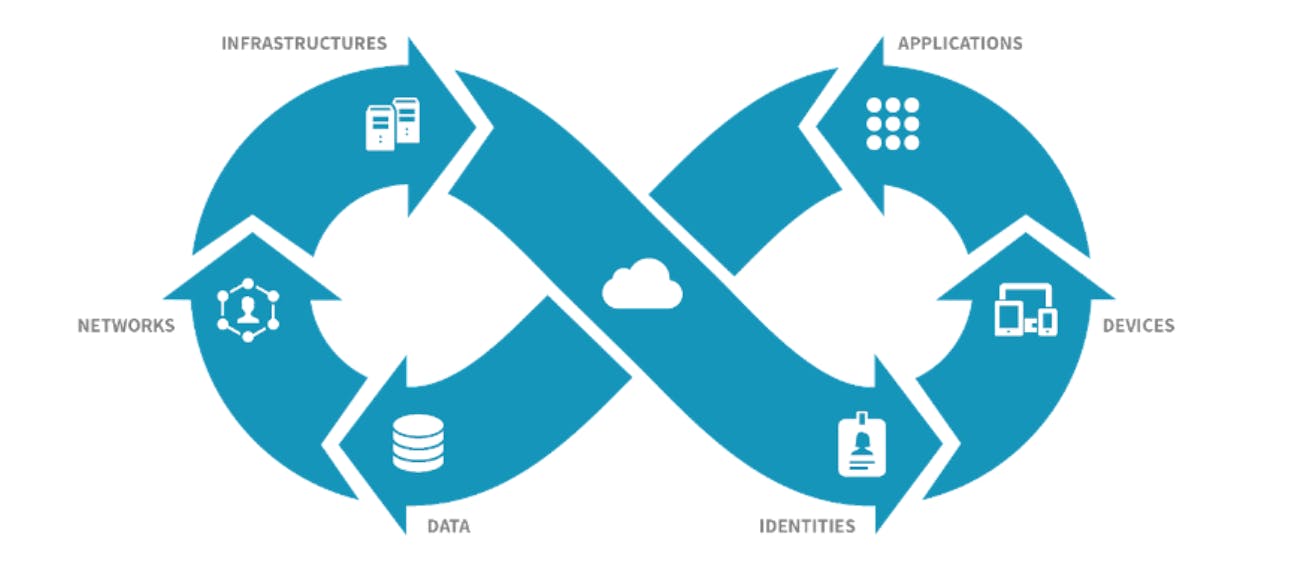
Source: CrowdStrike
Segmenting the cybersecurity landscape is never an easy exercise because of the way most platforms are attempting to tackle more and more of the security landscape. Taking into consideration these 6 core components (devices, infrastructure, networks, applications, identities and data), this is how many of the companies in the cybersecurity landscape map to those functions. Again, the complexity of cybersecurity means that no segmentation is perfect, and every solution can play in multiple buckets.

Source: Contrary Research
Devices
Every company is made up of machines, whether user-facing (laptops, phones, iPads) or machine-facing (server infrastructure, data centers). Each of these represent an endpoint. Security solutions that cater to this category are referred to as endpoint detection and response (EDR). Endpoint security is the gateway that protects access to a company’s network, managing requests and data flows that go in and out.
Managed Detection and Response (MDR) and managed security service provider (MSSP) can be mapped together, while also looking at Security Information Events and Management (SIEM) players. The role of MDR and MSSPs can be referred to as the human extension of Endpoint platforms. SIEM, MDR and MSSPs can be outsourced cybersecurity services through security professionals that help companies monitor devices against threat violations.
Identity
One of the most significant points of failure in cybersecurity is human error. As remote work, VPNs, and cloud computing have pushed more processes outside a firewall, security solutions have had to redouble their efforts to correctly identify and protect individual users. Identity and access management (IAM) revolves around understanding who someone is, whether they’re authorized to access certain things, and what their typical behavior looks like (vs. the behavior of fraudulent bad actors pretending to be someone else). The modern enterprise IT stack is more fragmented and complex in 2022 than it's ever been before. IT teams have an ever-increasing threat surface area to protect against bad actors.
Software
Software facilitates the communication between hardware devices and humans. Software can include categories like application, cloud, API, and infrastructure. Applications like a CRM, ERP, or a payroll system are programs that run on a computer’s operating system. Application security platforms protect these SaaS applications against potential threats once they are brought into an enterprise network.
Cloud can sit within software, though some may categorize it elsewhere. Without the evolution of cloud, we wouldn't have widespread delivery of software. Cloud security is one of the most rapidly evolving categories in security. More and more applications are cloud-based, so cloud security involves both application security and individual user security and identity protection. Networking is also progressively becoming more cloud-based, making firewalls less relevant. The emergence of the public and private cloud has advanced computing and storage for the enterprise. Cloud infrastructure does not specifically have direct security solutions for securing every workload given the significant infrastructural costs that would require. As a result, cloud security players have risen to solve those problems with CWPP (cloud workload protection).
Network
Networking allows hardware and software applications to communicate with each other. Network security solutions are designed to monitor network traffic requests coming in and out of the company’s network to stop threats before they materialize. A perimeter can be thought of as a company’s walled garden. A company’s perimeter deals with both its VPN (virtual private networks) which extends over a company’s private network and its WAN (wireless area networks) which connect separate networks to join various physical locations together. Because network security is focused on connections between hardware and applications, it also extends to securing things like email.
Data
Over the past decade, data has become an integral part of assets and information within the enterprise. Data security is primarily associated with protecting digital data, such as those in a database, from hackers or unauthorized users or in the case of a data breach. It covers everything — devices, software, identities, access and organizations’ policies and procedures. These security tools protect data through processes like data masking, encryption, and redaction of sensitive information.
This field also gained traction because there is an increasing amount of regulations for companies to protect customer and user data from being stolen. For example, industry and state regulations like the California Consumer Privacy Act (CCPA), the European Union’s General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), and more outline organizations’ legal obligations to protect data. We’ve categorized email security and encryption into all the buckets for companies that protect data.
Key Trends In Cybersecurity
Cloud Security Continues to Be a Top Priority
As previously mentioned, by 2025 over 95% of digital workloads will be cloud-based, up from 30% in 2021. As more workloads move to the cloud, the cloud will become the main attack surface for hackers to penetrate the modern organization. The rise of cloud infrastructure creates a meaningful opportunity for bad actors, given the diversity of available attack vectors and troves of available data. Cloud security is currently the biggest priority for technology executives. A primary driver is the rapid migration to the cloud over the past two years, which means that now CTOs are scrambling to protect themselves from hackers.
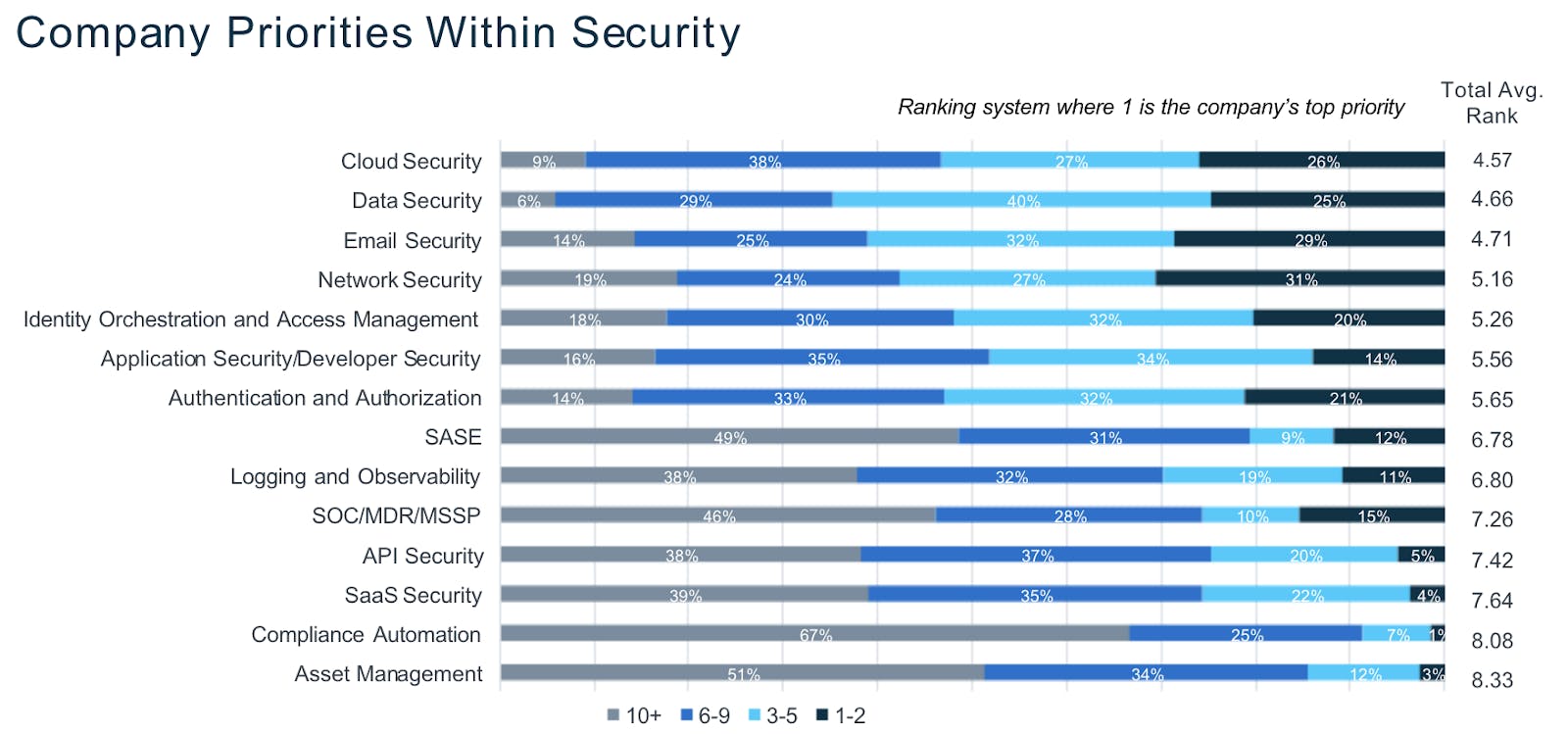
Source: Battery Ventures
There are many security vulnerabilities companies experience while migrating to the cloud. However, within cloud security spending there are two key areas emerging over the next couple of years.
First, there is rapid growth in the software supply chain (SSC). The software supply chain is popularly known as the connection that extends from software development to deployment, including open-source dependencies, build tools, package managers, and testing tools. Software supply chain security is about securing the components, activities, and practices involved in the creation and deployment of software that includes third-party infrastructure.
As vulnerabilities such as Log4j spread through the supply chain, more threats are expected to emerge. Gartner predicts that by 2025, 45% of organizations worldwide will have experienced attacks on their software supply chains, a three-fold increase from 2021. Cybercriminals have discovered that attacks on the digital supply chain on the cloud can provide a high return on investment.
The second major trend is the cloud-delivered secure access service edge (SASE), a market that merges networking and security together. This presents the fastest growing opportunity in the network security market. Gartner estimates that by 2025, more than 50% of organizations will have strategies to adopt SASE, up from less than 5% in 2020. This is going to be a rapid growth over the next five years sparked by how much companies have to move to the cloud and have to manage distributed teams globally. Despite the fact the cloud-security market is already at $11 billion and growing 20% annually, it represents less than 10% of total spending on public clouds, proving there is a significant amount of runway ahead for companies adopting cloud-first security solutions.
Embedded Security in the Tech Stack
Security continues to be intertwined with every component across the enterprise network. Many technology companies also want to be security companies, or provide security services. As the tech stack becomes fragmented, CTOs want solutions that bring some security into their organization so that it reduces the number of security solutions they need to purchase. Security has become entrenched in IT networking, observability, infrastructure and data analytics.
For example, security has become embedded with observability.
Datadog started as an application monitoring service but has evolved to offer more cloud security management solutions together with their core observability products.
Cloudflare started as a content delivery network (CDN) for websites, but has evolved to provide more full-stack zero enterprise security products in zero-trust and SASE.
Snowflake started out as a data warehouse and machine learning company, but has started to broaden its security services.
ServiceNow, which provides IT service management, has now incorporated more security operations and monitoring tools over the past few years
Companies like Snowflake and Databricks are approaching security as a data problem, something Contrary Research covered in our Snowflake vs Databrick report. In addition, there’s a similar trend in the evolution of DevSecOps where security is becoming infused with the DevOps process, something we covered in The Evolution of DevOps and our memos on companies like Snyk. The list goes on, but it seems clear this is going to be a core trend over the next few years.
Distributed Teams Continue to Complicate Security Efforts
Although the rise of remote work has seen a moderation in 2022, it seems that hybrid work is here to stay for many technology companies. Distributed teams have much more complex digital footprints than in-person teams. For enterprises to successfully implement hybrid work environments, zero-trust security models are required. Hybrid work seems likely to accelerate the adoption of zero-trust.
Gartner estimates that currently 60% of knowledge workers are remote, and at least 18% will not return to the office. TechCrunch reported that over 42% of IT staff are still working entirely remotely. These changes in the way we work, together with greater use of the public cloud, have exposed new and challenging attacks. Gartner recommends security leaders look beyond traditional approaches to security monitoring, detection and response to manage a wider set of risks.
The increase in remote and hybrid work will require companies to switch from using traditional corporate VPNs to more SASE offerings. This allows enterprises to approach the networking problem from an identity-first standpoint. This should lead to the adoption of solutions like Zero Trust Network Access (ZTNA) and Secure Web Gateway (SWG), all of which are solutions for securing remote workers. Zero trust network access grants appropriate access based on the identity of the humans and their devices. It monitors geolocation, historical usage patterns, and device posture.
Beyond managing access and identities, monitoring every employee’s devices and activity is more difficult because the company’s network can’t be relied upon. As a result, shadow IT has become a major trend within cybersecurity. Shadow IT refers to the growing number of applications and IT infrastructure utilized by employees that are not managed by the IT staff. And this isn’t a fringe problem; 50% of applications are not managed by IT teams. Accordingly, organizations will continue to allocate budget share to remote work cybersecurity solutions, both proactively and in response to attacks.
Vendor Consolidation and Aggregation
Due to the many trends and evolving technologies discussed throughout this report, cybersecurity has continued to see a proliferation of feature security solutions that aim to solve minor components of the technology stack. The sector is gradually experiencing vendor fatigue and agent bloat. As a result, there are two types of vendor consolidation and aggregation happening within the industry.
First, CTOs are now looking for solutions that can help them consolidate spending. The industry is gradually evolving from vendors providing individual, point solutions into bundled multi-product platform businesses. Larger enterprises are looking for vendors that can integrate across their heterogeneous environments from endpoint to cloud. One example is Palo Alto Networks, which has evolved from being a network security tool to becoming a broader platform, many of their offerings coming from 16 acquisitions over the last 5 years. Crowdstrike is another player that has evolved from providing single endpoint security into multiple product categories in security. This kind of platformization makes it easier for Chief Information Security Officers (CISO) to purchase one product that solves many different challenges.
The second type of consolidation and aggregation happening is the bundling of solutions into new sector categories. Gartner has taken the lead to help the industry consolidate these solutions. For example, we’ve seen multiple aspects of endpoint security bridged into extended detection and response (XDR), multiple aspects of network security merged into security service edge (SSE), and the many cloud solutions popping have been consolidated into cloud-native application protection platforms (CNAPP). These areas of XDR, SSE and CNAPP are major attempts that have merged over 15 individual point solutions into one unified terminology. Security companies can then ensure when they sell to CISOs and CTOs, that they’re bundling everything into one package. Gartner predicts that by 2024, 30% of enterprises will adopt cloud-delivered Secure Access Service Edge (SASE) platforms that bundle together all major aspects of networking and cloud security. The benefits of vendor consolidation also bring about cost reductions and lower total cost of ownership for already overwhelmed IT staff.
The Critical “Now” In Security
The threat landscape continues to evolve every day. The advancement in cloud, AI, and distributed services will only continue to accelerate and with it the scale of potential cyberattacks. There is no shortage of avenues for hackers to exploit, and most organizations are still struggling to detect and respond to threats.
Cybersecurity continues to take on increasing significance at the executive and board levels of every major organization. This ever-growing trend is not confined to the private sector, as governments around the world continue to expand their security budgets to prevent nation state attacks. Therefore, cybersecurity appears to be at an inflection point in the technology sector that will create multiple winners.